Scattered Spider targets VMware ESXi in using social engineering – Securityaffairs.com
Published on: 2025-07-28
Intelligence Report: Scattered Spider targets VMware ESXi using social engineering – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
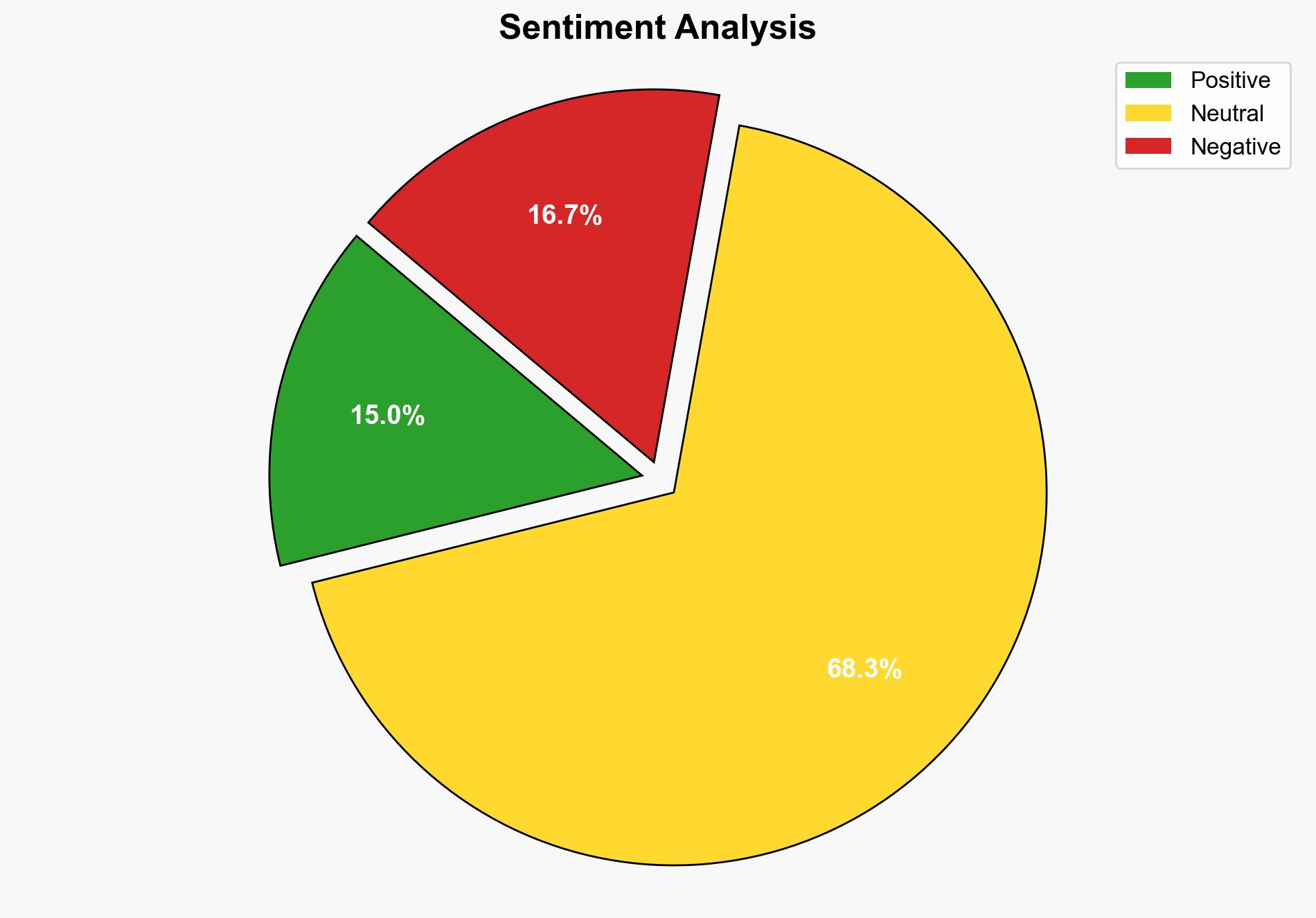
The cybercrime group known as Scattered Spider is leveraging social engineering tactics to exploit VMware ESXi hypervisors, posing a significant threat to sectors such as retail, airline, and transportation in North America. The most supported hypothesis is that Scattered Spider is primarily focused on rapid, stealthy data exfiltration and ransomware deployment. Confidence level: High. Recommended action: Enhance monitoring and harden defenses around VMware infrastructure, particularly focusing on social engineering vulnerabilities.
2. Competing Hypotheses
1. **Hypothesis A**: Scattered Spider’s primary objective is to exfiltrate sensitive data and deploy ransomware for financial gain. This hypothesis is supported by their use of social engineering to gain access to privileged accounts and the subsequent deployment of ransomware.
2. **Hypothesis B**: Scattered Spider aims to disrupt critical infrastructure operations in North America as part of a broader geopolitical agenda. This hypothesis considers the sectors targeted and the potential for causing widespread disruption.
Using Bayesian Scenario Modeling, Hypothesis A is better supported due to the group’s focus on rapid data exfiltration and ransomware deployment, which aligns with typical financially motivated cybercrime patterns.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Scattered Spider’s primary motivation is financial gain, and that their tactics are primarily opportunistic rather than strategically targeted.
– **Red Flags**: The lack of detailed attribution to specific individuals within Scattered Spider raises questions about the group’s structure and potential state sponsorship. The rapidity of attacks suggests a high level of sophistication that may not align with purely criminal motivations.
4. Implications and Strategic Risks
The tactics used by Scattered Spider could inspire similar groups to adopt these methods, increasing the overall threat landscape. The focus on critical infrastructure sectors raises the risk of cascading effects on supply chains and economic stability. If state-sponsored, this could escalate geopolitical tensions, particularly if linked to adversarial nations.
5. Recommendations and Outlook
- Implement stringent access controls and multi-factor authentication for all privileged accounts.
- Conduct regular social engineering awareness training for employees, particularly those in help desk roles.
- Scenario Projections:
- Best Case: Enhanced defenses prevent further breaches, and Scattered Spider’s operations are disrupted.
- Worst Case: Continued successful attacks lead to significant data breaches and operational disruptions across critical sectors.
- Most Likely: Increased awareness and defensive measures mitigate some risks, but the threat persists due to evolving tactics.
6. Key Individuals and Entities
No specific individuals are identified in the intelligence. The group is referred to as Scattered Spider, aka Ktapus, Muddle, Libra, Octo, and TEMP.UNC.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus