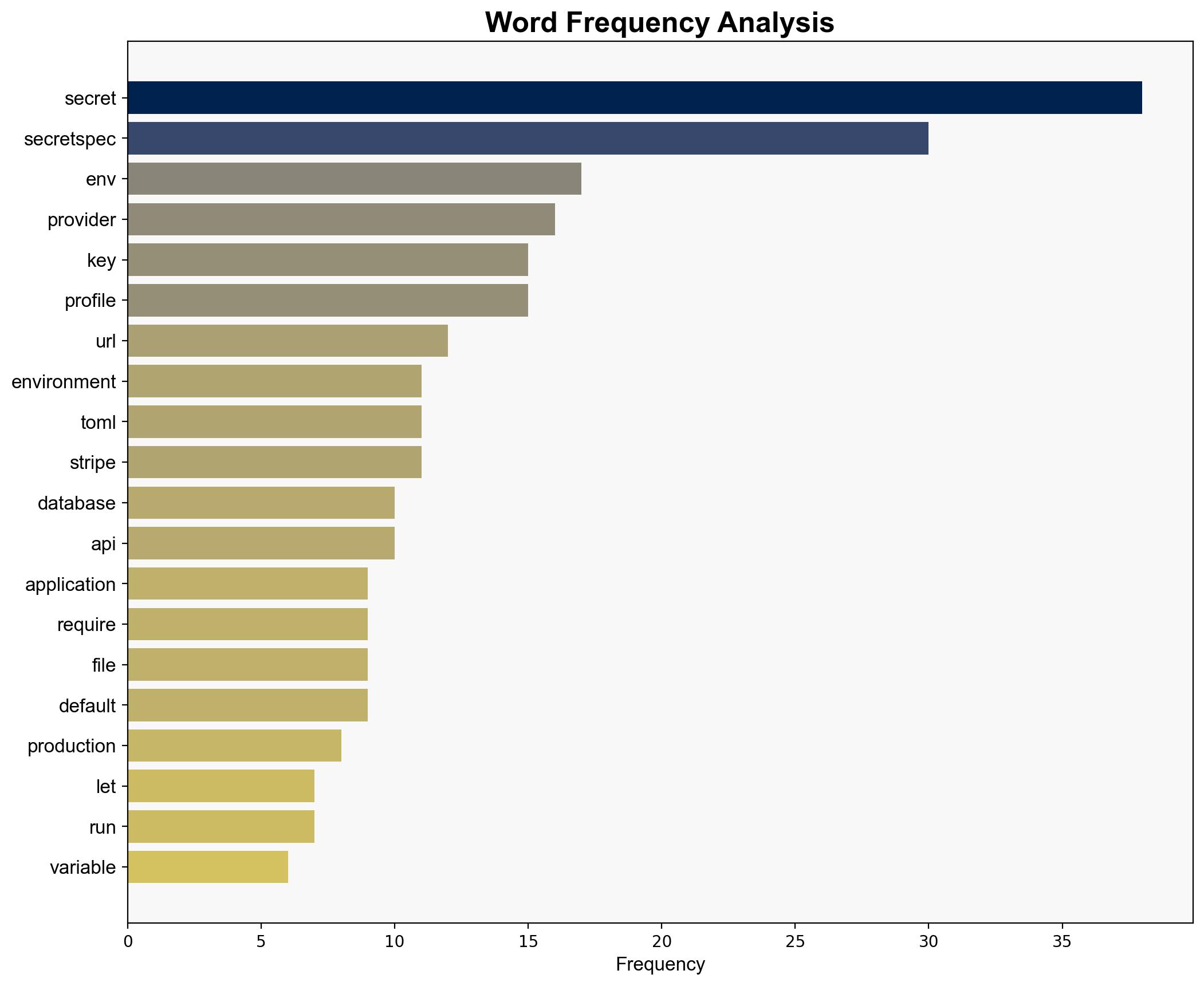
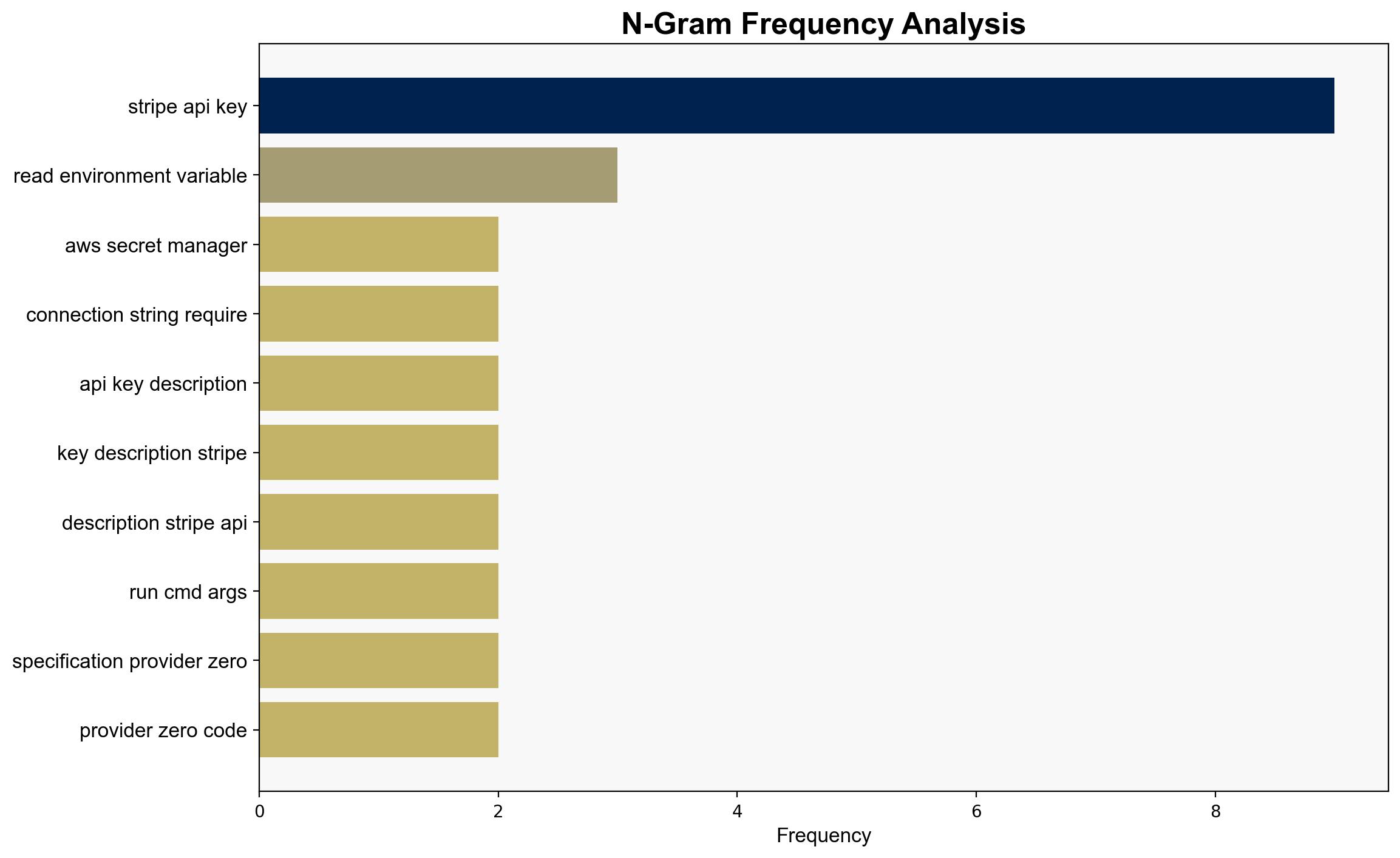
SecretSpec Declarative Secrets Management – Devenv.sh
Published on: 2025-07-21
Intelligence Report: SecretSpec Declarative Secrets Management – Devenv.sh
1. BLUF (Bottom Line Up Front)
SecretSpec offers a declarative approach to secrets management, aiming to address challenges such as vendor lock-in, manual secret handling, and security vulnerabilities associated with plaintext storage. The proposed solution integrates seamlessly with various environments, enhancing security and operational efficiency. Key recommendations include adopting SecretSpec for its ability to simplify secrets management and improve security posture.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
SecretSpec’s approach mitigates risks of unauthorized access by encrypting secrets and reducing reliance on plaintext environment files. Simulations indicate a reduced attack surface for cyber adversaries targeting secrets management systems.
Indicators Development
SecretSpec’s integration with environment variables and secret stores like AWS Secret Manager provides a robust framework for detecting anomalies. This integration supports early threat detection by monitoring access patterns and changes in secret management workflows.
Bayesian Scenario Modeling
Probabilistic models suggest that adopting SecretSpec reduces the likelihood of successful cyberattacks on secrets management systems by streamlining secret handling processes and minimizing human error.
3. Implications and Strategic Risks
The transition to SecretSpec could disrupt existing workflows, requiring adaptation and training. However, the long-term benefits include enhanced security and reduced operational risks. The strategic risk lies in the potential for incomplete adoption, leading to fragmented security practices.
4. Recommendations and Outlook
- Adopt SecretSpec to streamline secrets management and enhance security across development and production environments.
- Conduct training sessions to ensure smooth transition and full utilization of SecretSpec features.
- Best Case: Full adoption leads to improved security and operational efficiency.
- Worst Case: Partial adoption results in inconsistent security practices.
- Most Likely: Gradual adoption with initial challenges, followed by improved security posture.
5. Key Individuals and Entities
Doman Koar
6. Thematic Tags
cybersecurity, secrets management, encryption, operational efficiency, risk mitigation