Secure Borders Win Wars Like This One – Daily Signal
Published on: 2025-06-26
Intelligence Report: Secure Borders Win Wars Like This One – Daily Signal
1. BLUF (Bottom Line Up Front)
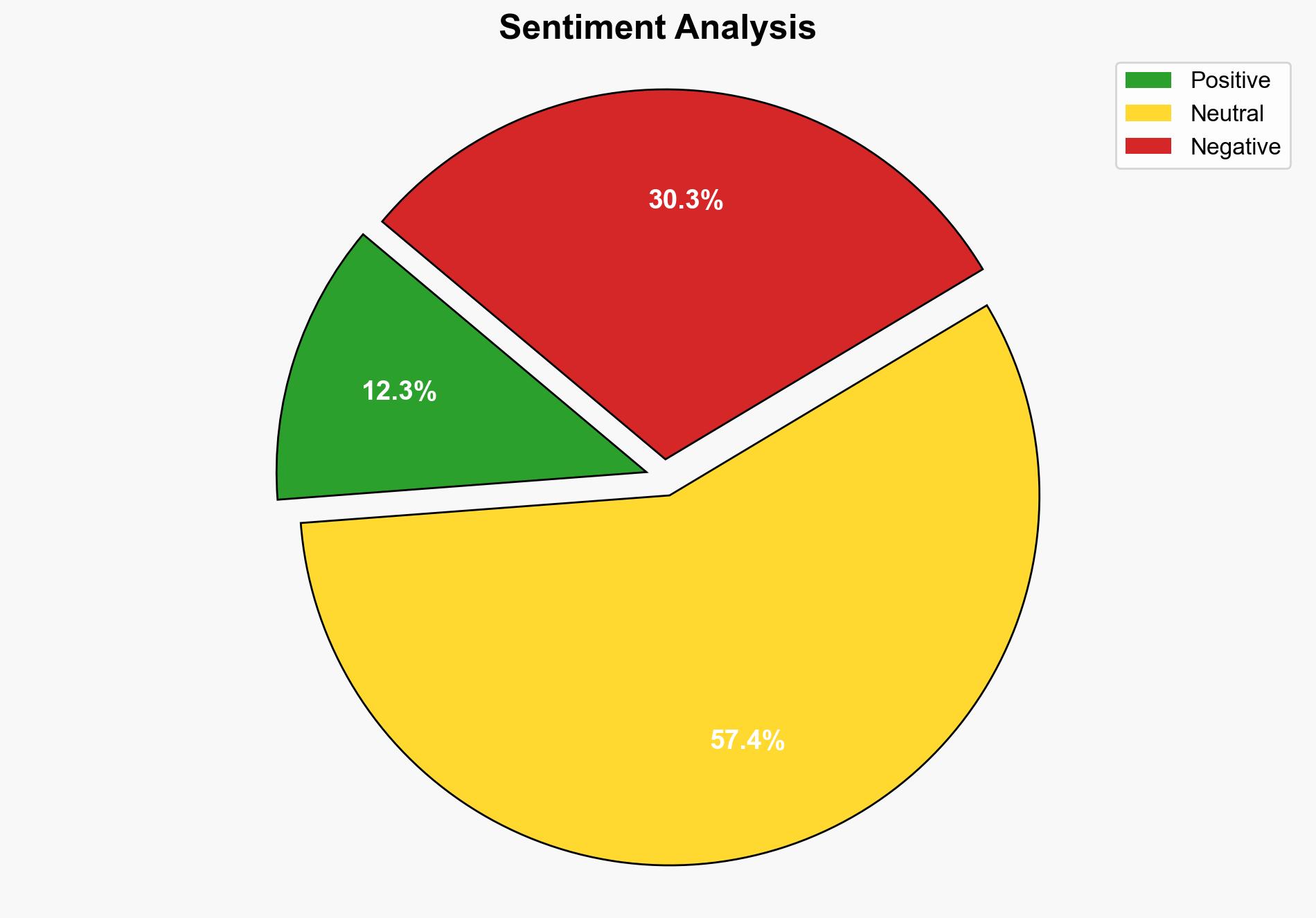
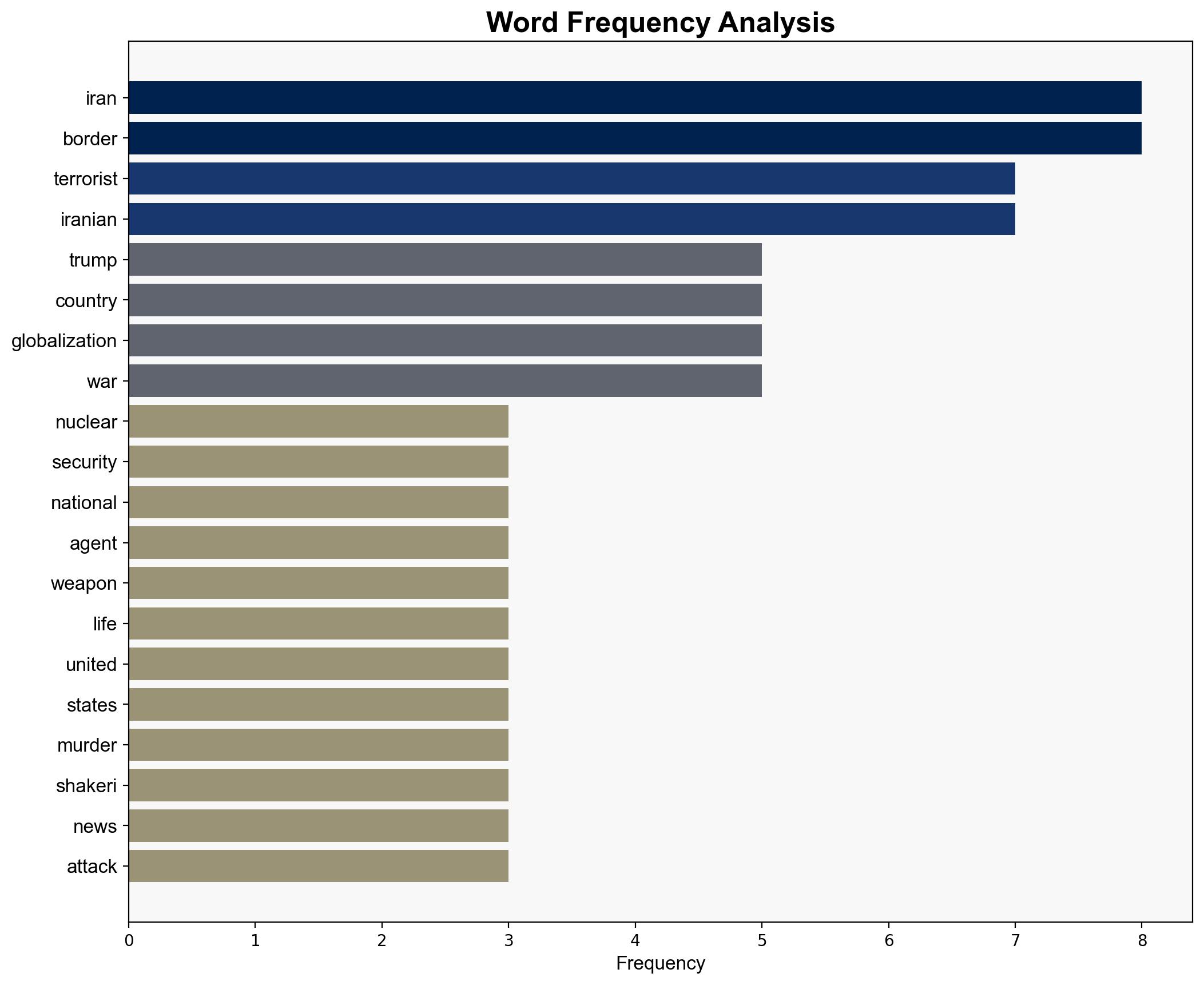
The report underscores the critical link between border security and national security, emphasizing the potential threats posed by Iranian-sponsored terrorism. It highlights recent plots targeting high-profile individuals in the United States and stresses the need for stringent border control measures. The strategic recommendation is to enhance border security protocols to prevent infiltration by hostile actors and mitigate the risk of terrorism.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Analysis suggests that Iranian-backed operatives may be attempting to exploit porous borders to execute attacks. The intention appears to be to destabilize and retaliate against perceived adversaries.
Indicators Development
Monitoring digital radicalization, suspicious travel patterns, and online propaganda is crucial to preemptively identifying and thwarting operational planning by hostile entities.
Narrative Pattern Analysis
Ideological narratives are being adapted for recruitment and incitement, with a focus on anti-American and anti-Israeli sentiments. These narratives are likely used to justify and promote terrorist activities.
3. Implications and Strategic Risks
The report identifies a heightened risk of terrorism linked to inadequate border controls. The potential for cross-domain threats, including cyber and economic disruptions, is significant. The systemic vulnerability lies in the ability of hostile actors to exploit immigration and border security weaknesses, potentially leading to cascading effects on national security.
4. Recommendations and Outlook
- Enhance border security measures, including advanced surveillance and intelligence-sharing protocols, to detect and deter hostile infiltrations.
- Implement scenario-based planning to prepare for potential terrorist threats, considering best case (successful deterrence), worst case (successful attacks), and most likely scenarios (attempted but thwarted attacks).
- Increase collaboration with international partners to monitor and counteract transnational terrorist networks.
5. Key Individuals and Entities
– Asif Merchant
– Farhad Shakeri
– Rodney Scott
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus