Securing DNS With Umbrella at Black Hat – Cisco.com
Published on: 2025-09-03
Intelligence Report: Securing DNS With Umbrella at Black Hat – Cisco.com
1. BLUF (Bottom Line Up Front)
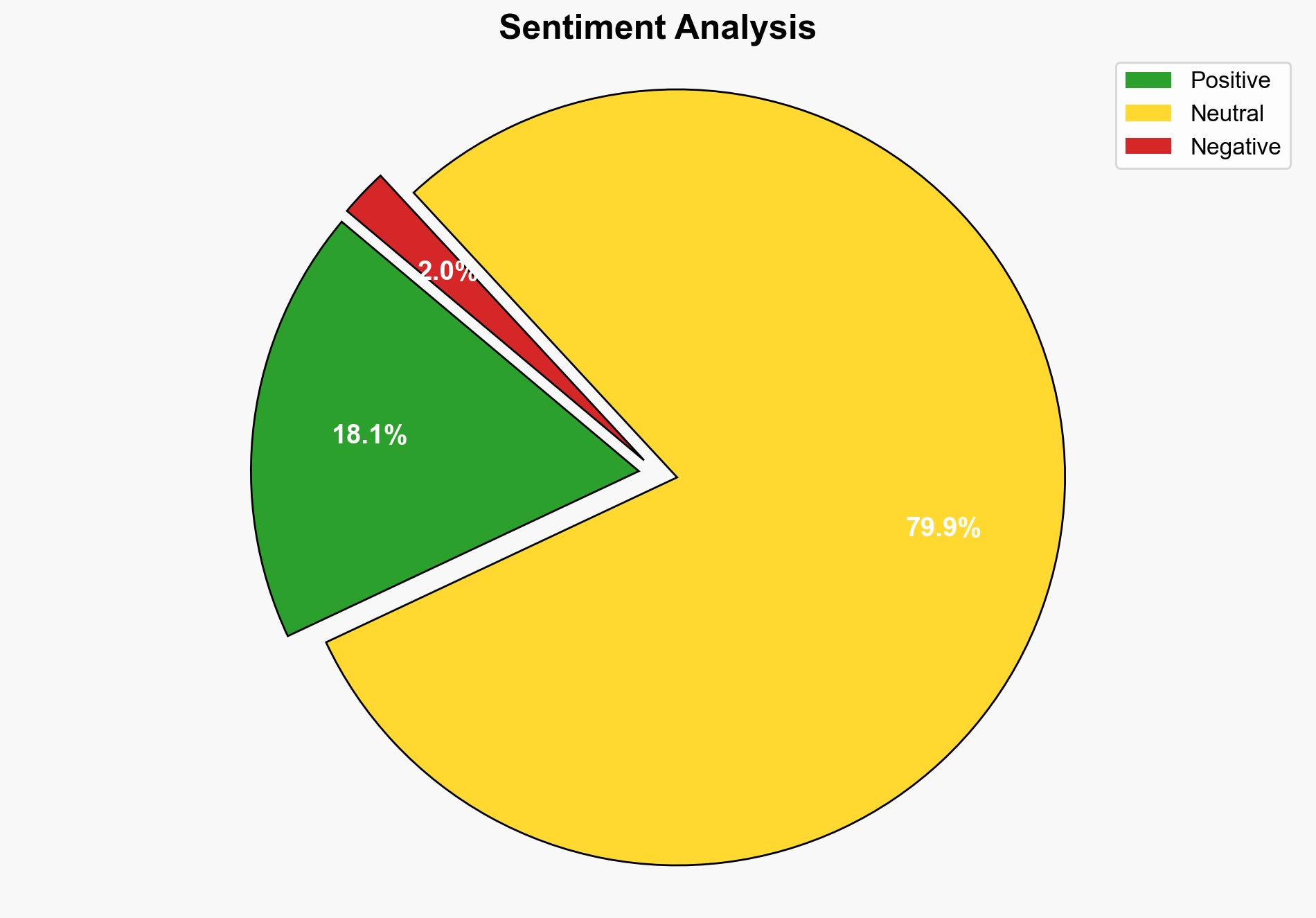
The most supported hypothesis is that Cisco’s DNS monitoring and security measures at Black Hat events are primarily aimed at enhancing cybersecurity by detecting and mitigating malicious activities, such as malware and phishing, through centralized intelligence. Confidence in this hypothesis is moderate due to potential gaps in data transparency and the evolving nature of cyber threats. Recommended action includes continued investment in DNS security technologies and collaboration with cybersecurity communities to address emerging threats.
2. Competing Hypotheses
– **Hypothesis 1**: Cisco’s DNS monitoring at Black Hat is primarily focused on enhancing cybersecurity by detecting and preventing malicious activities, such as malware and phishing, through centralized intelligence.
– **Hypothesis 2**: Cisco’s involvement in DNS monitoring at Black Hat is driven by a strategic interest in gathering data on network usage trends and application popularity, which could be used for commercial advantage or product development.
Using ACH 2.0, Hypothesis 1 is better supported due to the explicit mention of detecting malicious activities and the emphasis on security measures. Hypothesis 2 lacks direct evidence and relies more on inference about commercial interests.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Cisco’s primary motivation is cybersecurity rather than commercial interests. Another assumption is that DNS monitoring provides comprehensive visibility into network threats.
– **Red Flags**: The potential for bias exists if Cisco’s commercial interests are not fully disclosed. Additionally, the reliance on DNS data alone may overlook other vectors of cyber threats.
4. Implications and Strategic Risks
The focus on DNS security at high-profile events like Black Hat highlights the increasing sophistication of cyber threats. There is a risk of over-reliance on DNS monitoring, which may not capture all threat vectors. The evolving landscape of generative AI applications poses new challenges, potentially increasing the complexity of threat detection. Geopolitically, the collaboration at such events can foster international cybersecurity cooperation but also expose vulnerabilities if not managed carefully.
5. Recommendations and Outlook
- Enhance DNS security measures by integrating with broader threat intelligence platforms to capture a wider range of cyber threats.
- Foster partnerships with other cybersecurity entities to share insights and develop comprehensive threat detection strategies.
- Scenario Projections:
- Best Case: Enhanced security measures lead to significant reductions in cyber threats at major events.
- Worst Case: Over-reliance on DNS monitoring results in undetected threats, leading to security breaches.
- Most Likely: Continued evolution of threats requires adaptive security strategies and ongoing collaboration.
6. Key Individuals and Entities
David Keller is mentioned as a contributor to the DNS monitoring efforts. Cisco is the primary entity involved in the DNS security measures at Black Hat events.
7. Thematic Tags
cybersecurity, DNS security, malware detection, phishing prevention, generative AI, network monitoring