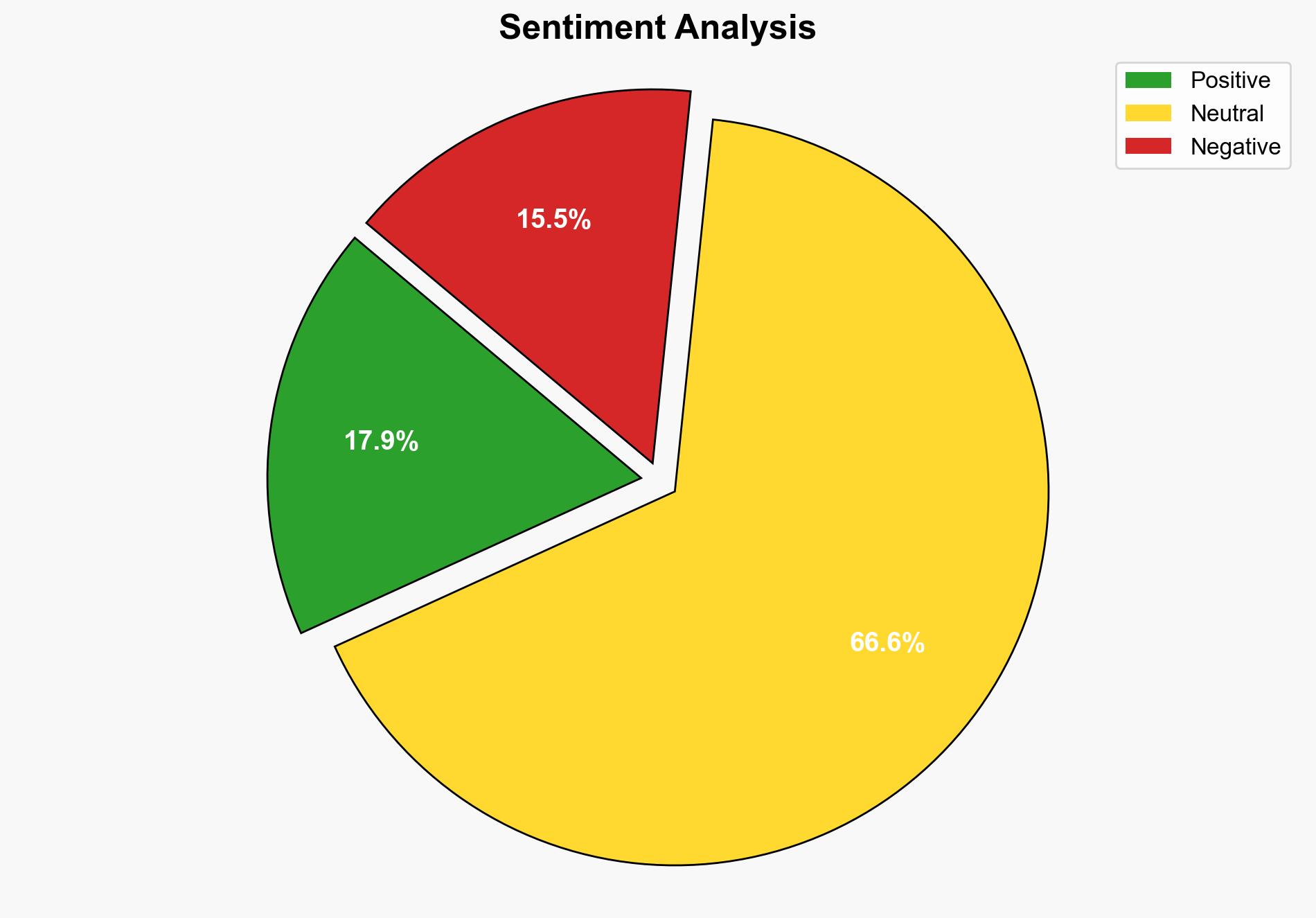
Security Database Used by Apple Goes Independent After Funding Cut – MacRumors
Published on: 2025-04-16
Intelligence Report: Security Database Used by Apple Goes Independent After Funding Cut – MacRumors
1. BLUF (Bottom Line Up Front)
The Common Vulnerabilities and Exposures (CVE) program, critical for global cybersecurity, faces a funding crisis due to abrupt cessation of U.S. government support. A newly formed CVE Foundation aims to ensure its continuity independently. Immediate strategic action is required to prevent disruption in vulnerability management and maintain cybersecurity integrity.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The funding cut may be driven by broader government downsizing initiatives. Alternatively, it could be a strategic shift towards decentralizing cybersecurity responsibilities. The establishment of the CVE Foundation suggests preemptive measures were anticipated, possibly indicating foresight into governmental policy changes.
SWOT Analysis
Strengths: CVE’s established global reputation and widespread adoption.
Weaknesses: Dependency on a single funding source.
Opportunities: Transition to a non-profit model could enhance global cooperation and governance.
Threats: Potential for increased cyber threats due to temporary disruption in CVE operations.
Indicators Development
Warning signs include increased cyber incidents due to lack of standardized vulnerability identifiers, delays in security patches, and heightened activity in cyber threat forums discussing vulnerabilities.
3. Implications and Strategic Risks
The funding cut poses significant risks to global cybersecurity infrastructure. Without CVE, the ability to effectively communicate and manage vulnerabilities is compromised, potentially leading to increased cyberattacks. Economically, companies reliant on CVE for security updates may face operational disruptions. Politically, this move could signal a shift in U.S. cybersecurity strategy, impacting international relations and cooperation.
4. Recommendations and Outlook
- Encourage immediate international collaboration to support the CVE Foundation’s transition to a non-profit model.
- Develop contingency plans for vulnerability management in the interim period.
- Scenario-based projection: If the CVE Foundation successfully transitions, expect enhanced global cybersecurity governance. Conversely, failure to secure adequate support could lead to fragmented vulnerability management systems.
5. Key Individuals and Entities
Kent Landfield, MITRE Corporation, CVE Foundation, U.S. Cybersecurity and Infrastructure Security Agency (CISA).