Security Forces Intensify Search for Three Jaish-e-Mohammad Terrorists in Kishtwar After Gunfight
Published on: 2026-02-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Operation to track down 3 holed-up terrorists underway following encounter in Kishtwar
1. BLUF (Bottom Line Up Front)
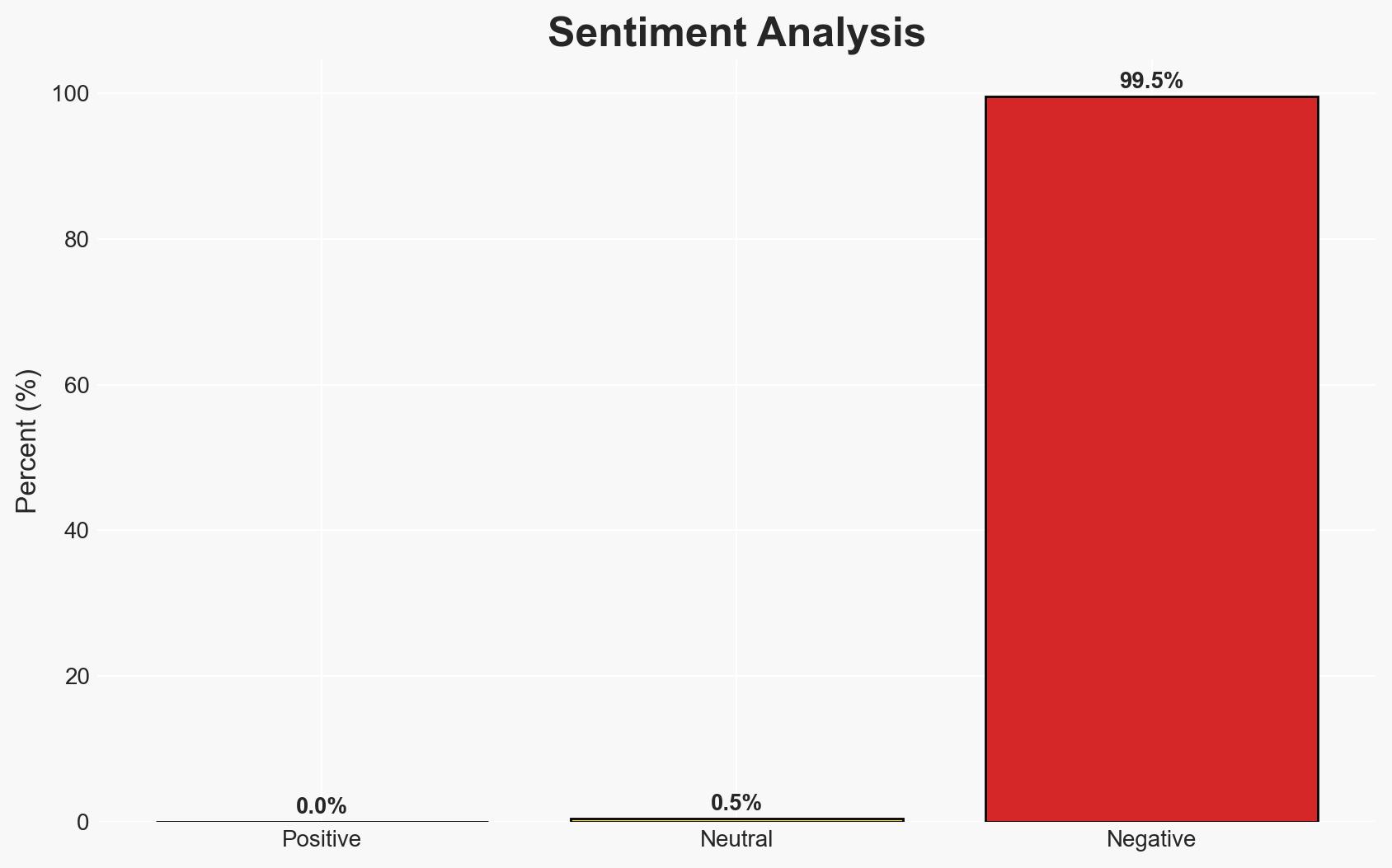
The ongoing operation in Kishtwar district aims to neutralize three Jaish-e-Mohammad terrorists, with heightened security measures in place. The operation is supported by aerial surveillance and ground forces, but the challenging terrain and weather conditions complicate efforts. The most likely hypothesis is that the terrorists are leveraging local support and environmental conditions to evade capture. Overall confidence in this judgment is moderate.
2. Competing Hypotheses
- Hypothesis A: The terrorists are receiving substantial local support, allowing them to evade capture despite sustained military efforts. This is supported by the prolonged nature of the operation and the repeated loss of contact with the terrorists. However, the extent of local support remains uncertain.
- Hypothesis B: The terrorists are primarily relying on the challenging terrain and weather conditions to avoid detection and capture. This is supported by the operational difficulties faced by security forces and the repeated encounters in difficult-to-access areas. However, this does not fully explain the duration of the operation.
- Assessment: Hypothesis A is currently better supported due to indications of local support, such as potential assistance with food and shelter. Key indicators that could shift this judgment include intelligence on local sympathizers or changes in the operational tempo of the security forces.
3. Key Assumptions and Red Flags
- Assumptions: The terrorists are affiliated with Jaish-e-Mohammad; local support is critical to their evasion; security forces have accurate intelligence on terrorist locations; the terrain significantly hinders operations.
- Information Gaps: Precise details on local support networks; the exact number and condition of the terrorists; the impact of weather on operational capabilities.
- Bias & Deception Risks: Potential over-reliance on drone surveillance data; confirmation bias towards assuming local support without concrete evidence; possible misinformation from local informants.
4. Implications and Strategic Risks
The operation’s outcome could influence regional stability and counter-terrorism dynamics. Prolonged operations may strain local resources and affect civilian perceptions.
- Political / Geopolitical: Potential escalation in regional tensions if operations extend or result in significant casualties.
- Security / Counter-Terrorism: Continued terrorist evasion may embolden other groups; successful neutralization could deter future activities.
- Cyber / Information Space: Potential for misinformation campaigns or propaganda by terrorist groups to exploit operational delays.
- Economic / Social: Disruption to local economies and social cohesion due to prolonged military presence and internet shutdowns.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence collection on local support networks; maintain operational pressure with adaptive tactics; ensure civilian safety and communication.
- Medium-Term Posture (1–12 months): Strengthen community engagement to reduce local support for terrorists; invest in terrain-adaptive technologies and training.
- Scenario Outlook: Best: Terrorists captured, reducing regional threat. Worst: Prolonged evasion leading to increased local support. Most-Likely: Continued operations with gradual attrition of terrorist capabilities.
6. Key Individuals and Entities
- Jaish-e-Mohammad (JeM)
- Security Forces (Special Forces, Rashtriya Rifles, Special Operations Group, CRPF)
- Northern Army Commander Lt Gen Pratik Sharma
7. Thematic Tags
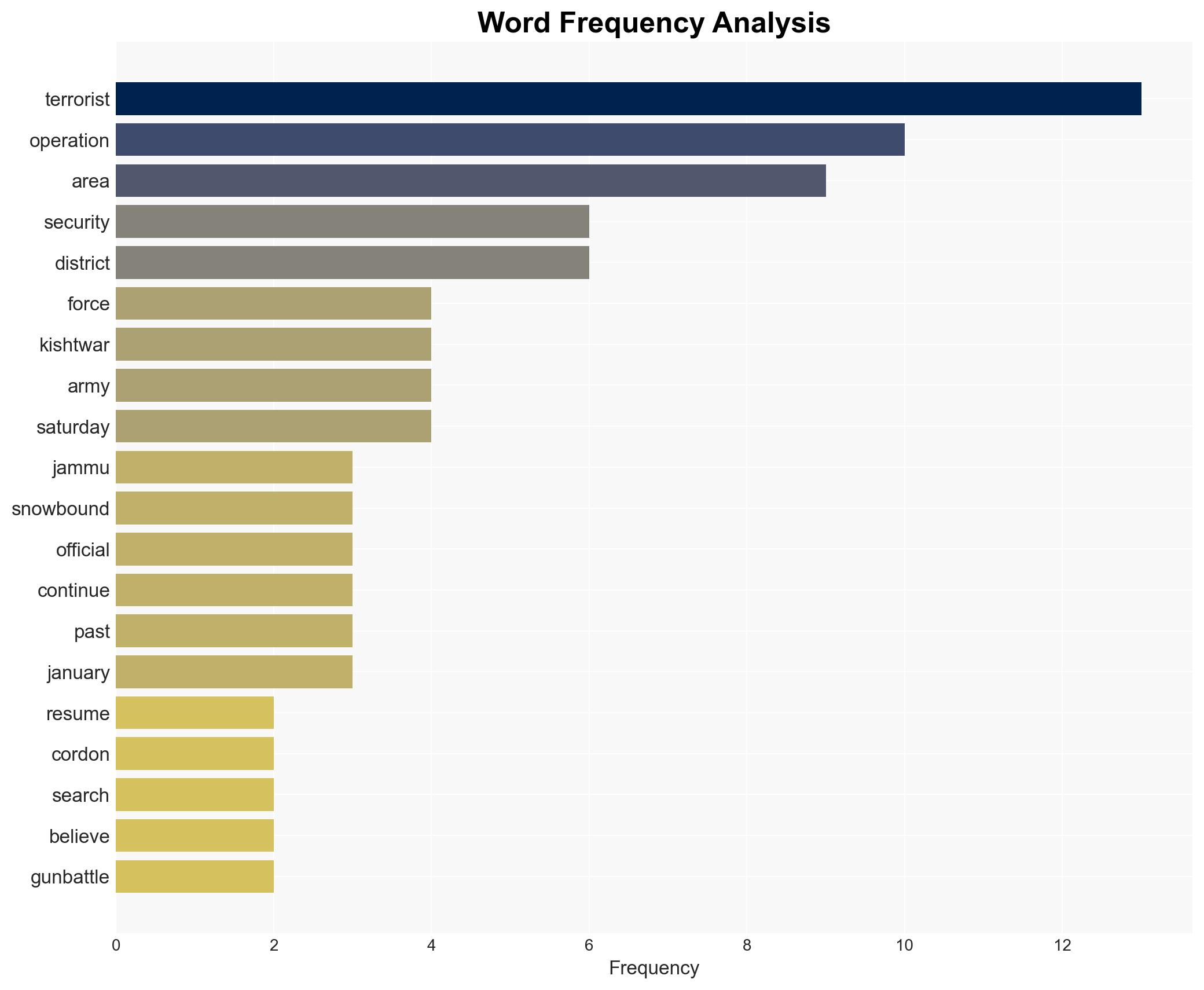
Counter-Terrorism, Jaish-e-Mohammad, Kishtwar, military operations, local support networks, security forces, aerial surveillance
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us