Security Researchers Uncover 29 Zero-Day Vulnerabilities on Day Two of Pwn2Own Automotive 2026
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers exploit 29 zero-days on second day of Pwn2Own Automotive
1. BLUF (Bottom Line Up Front)
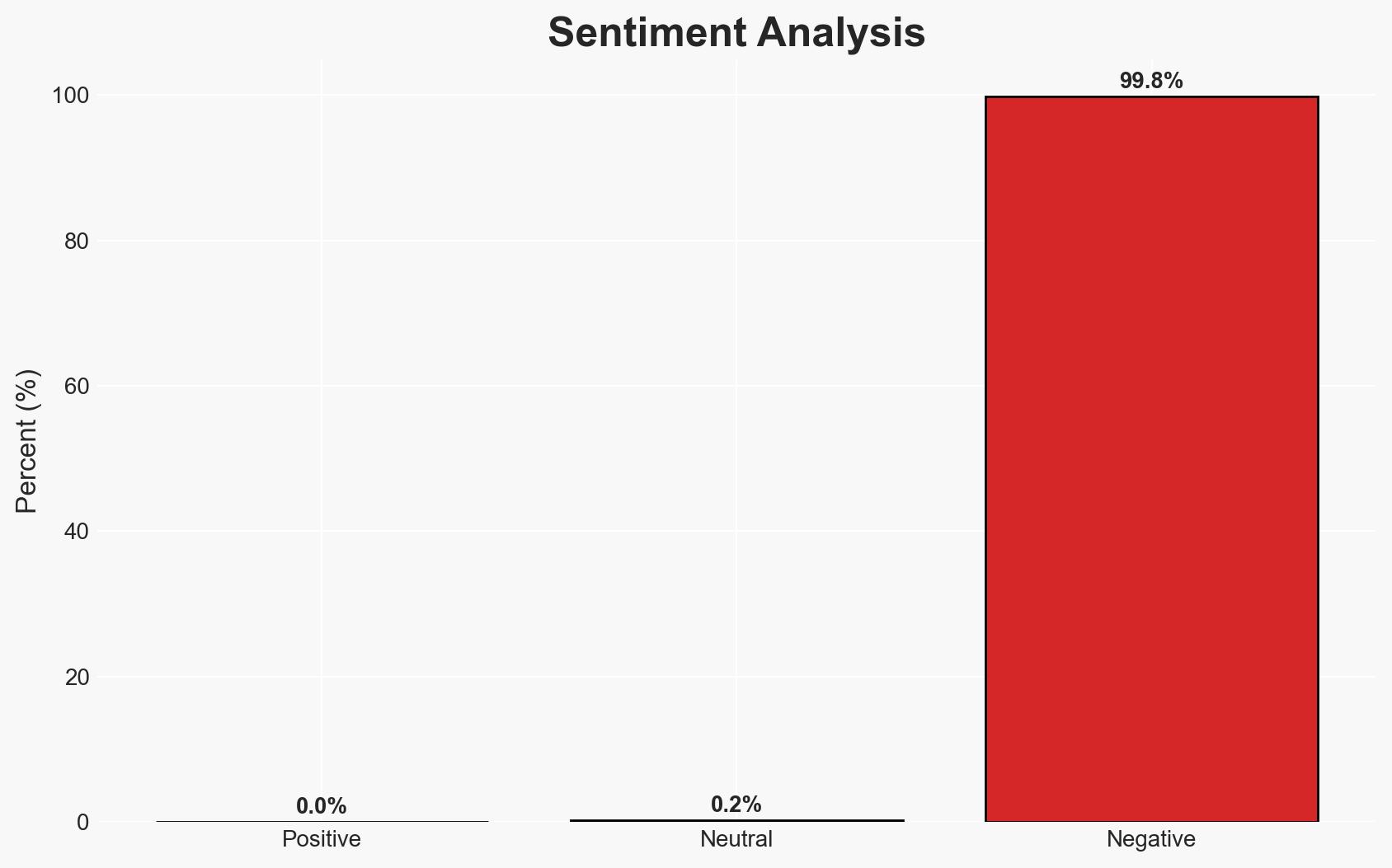
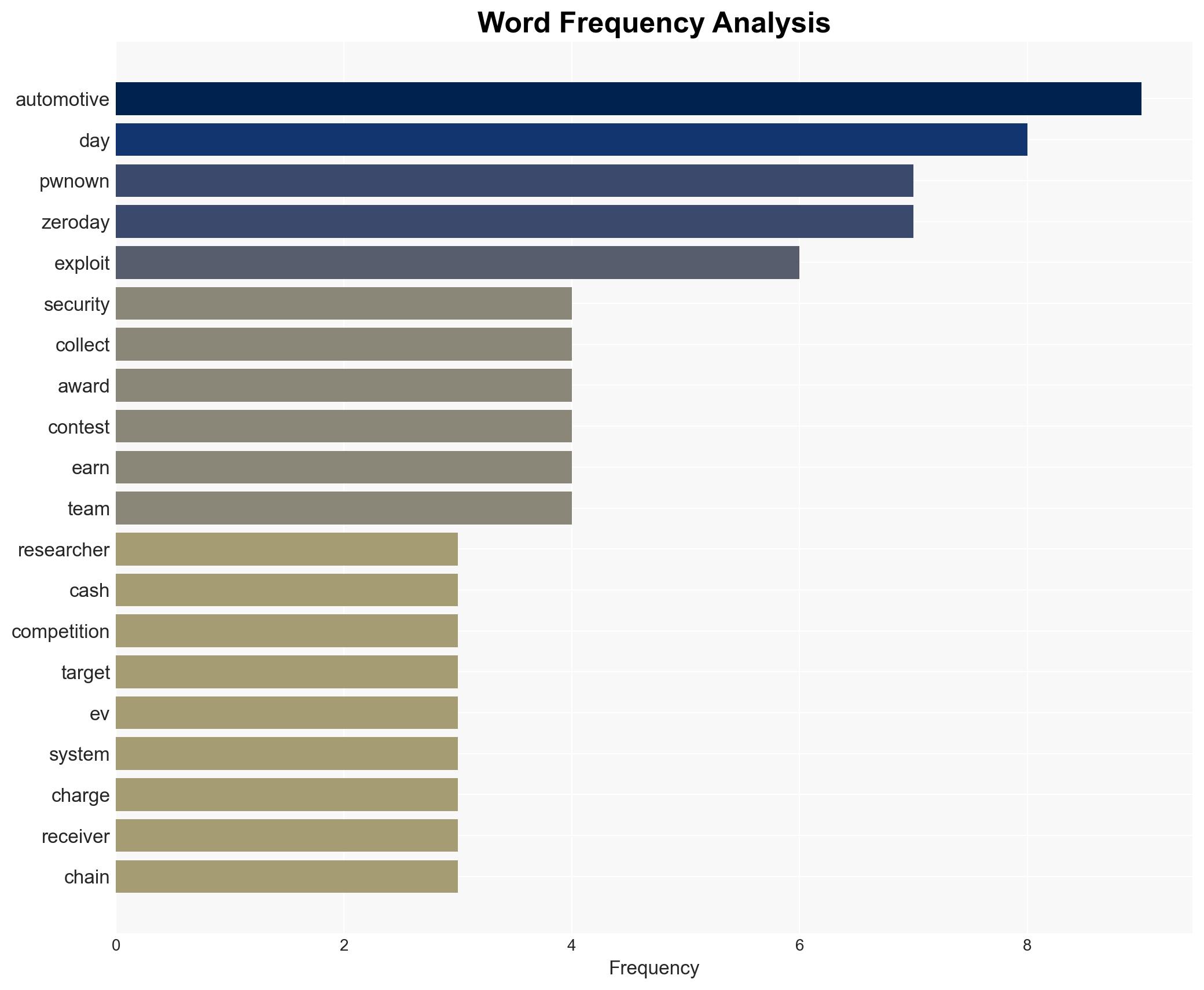
During the Pwn2Own Automotive 2026 event, security researchers exploited 29 zero-day vulnerabilities, highlighting significant security gaps in automotive technologies, particularly in EV chargers and infotainment systems. This development underscores the persistent vulnerabilities in automotive cybersecurity, with moderate confidence that these findings will prompt manufacturers to expedite security patching and enhance system defenses. The affected entities include automotive manufacturers, technology providers, and consumers relying on these systems.
2. Competing Hypotheses
- Hypothesis A: The high number of zero-days exploited is primarily due to inherent vulnerabilities in rapidly evolving automotive technologies. Supporting evidence includes the focus on EV chargers and infotainment systems, which are complex and frequently updated. However, the uncertainty lies in whether all vulnerabilities are systemic or if some are due to poor implementation by specific vendors.
- Hypothesis B: The vulnerabilities are largely due to insufficient security measures and testing by manufacturers before deployment. This is supported by the repeated targeting of specific systems and devices. Contradicting evidence includes the possibility that some vulnerabilities are newly introduced by recent updates, not due to lack of initial security.
- Assessment: Hypothesis A is currently better supported, as the rapid technological advancements in automotive systems often outpace security measures. Key indicators that could shift this judgment include evidence of systemic security oversights across multiple manufacturers or a pattern of vulnerabilities in newly updated systems.
3. Key Assumptions and Red Flags
- Assumptions: Automotive manufacturers will prioritize patching vulnerabilities; the vulnerabilities are not being exploited maliciously in the wild; the event findings are comprehensive and accurately reported.
- Information Gaps: Specific details on the nature of the vulnerabilities; the response strategies of affected manufacturers; potential exploitation of these vulnerabilities outside the contest environment.
- Bias & Deception Risks: Potential bias in reporting by event organizers to highlight the contest’s success; limited visibility into the full scope of vulnerabilities due to proprietary technology details.
4. Implications and Strategic Risks
The exploitation of zero-day vulnerabilities in automotive technologies could lead to increased scrutiny on cybersecurity practices within the industry. Over time, this may drive regulatory changes and influence consumer trust in automotive technology.
- Political / Geopolitical: Potential for increased regulatory pressure on automotive cybersecurity standards globally.
- Security / Counter-Terrorism: Elevated risk of these vulnerabilities being leveraged for malicious purposes, including potential threats to public safety.
- Cyber / Information Space: Highlighted need for robust cybersecurity frameworks and collaboration between manufacturers and cybersecurity experts.
- Economic / Social: Possible financial implications for manufacturers in terms of recalls and reputation management; consumer hesitancy towards adopting new automotive technologies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor manufacturer responses and patch releases; engage with cybersecurity experts to assess potential risks and mitigation strategies.
- Medium-Term Posture (1–12 months): Develop partnerships between automotive and cybersecurity sectors; invest in research and development for secure automotive technologies.
- Scenario Outlook:
- Best: Rapid patching and improved security measures prevent exploitation, restoring consumer confidence.
- Worst: Delayed responses lead to exploitation in the wild, resulting in regulatory penalties and loss of consumer trust.
- Most-Likely: Manufacturers implement patches and enhance security, but ongoing vulnerabilities necessitate continuous vigilance and updates.
6. Key Individuals and Entities
- Fuzzware.io
- Sina Kheirkhah of Summoning Team
- Rob Blakely of Technical Debt Collectors
- Hank Chen of InnoEdge Labs
- Slow Horses of Qrious Secure
- PetoWorks team
- Juurin Oy team
- Ryo Kato
- Synacktiv Team
- Not clearly identifiable from open sources in this snippet for some entities
7. Thematic Tags
cybersecurity, automotive cybersecurity, zero-day vulnerabilities, Pwn2Own, EV chargers, infotainment systems, cybersecurity collaboration, regulatory implications
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us