Security Teams Must Deploy Anti-Infostealer Defenses Now – Infosecurity Magazine
Published on: 2025-10-17
Intelligence Report: Security Teams Must Deploy Anti-Infostealer Defenses Now – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
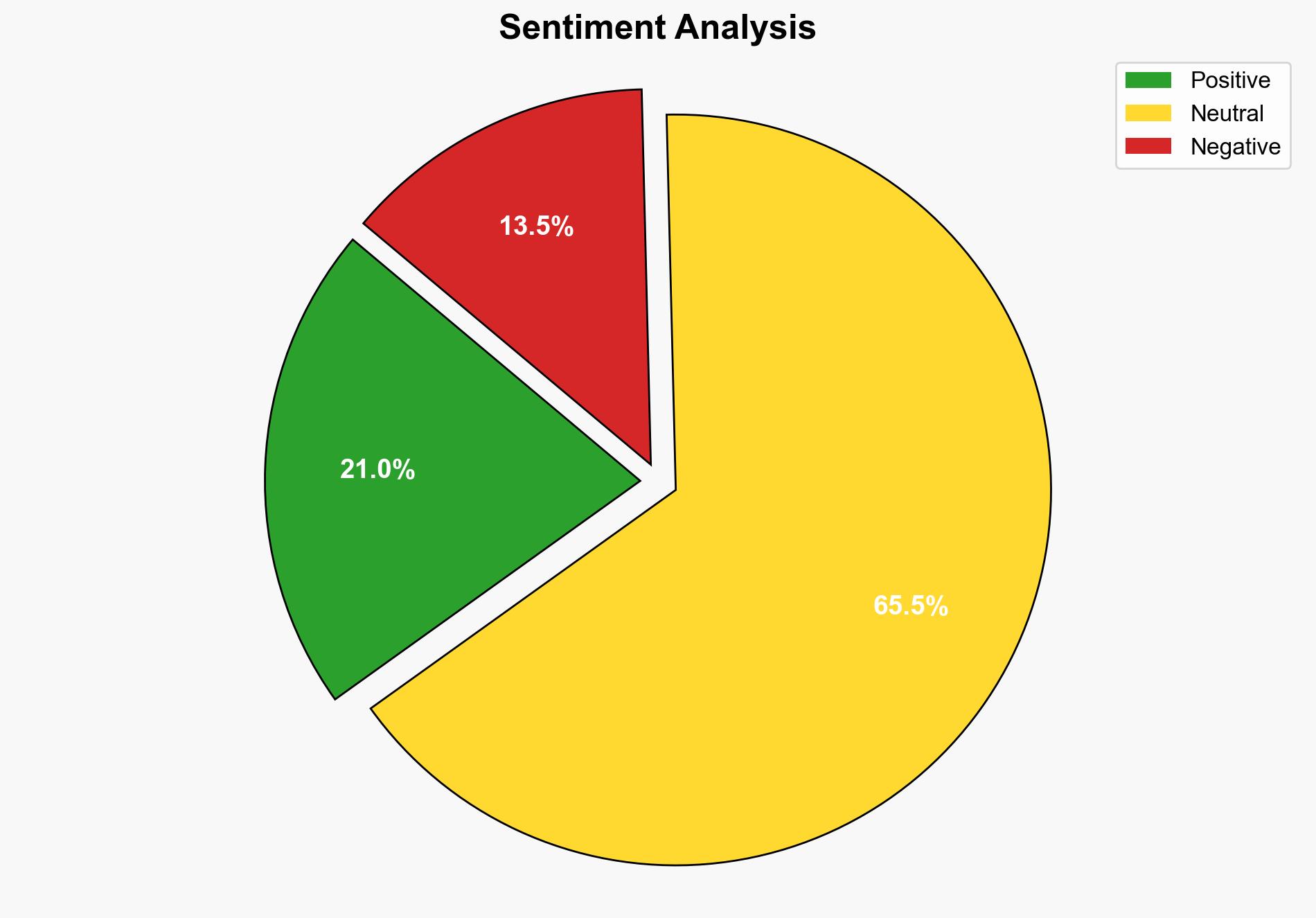
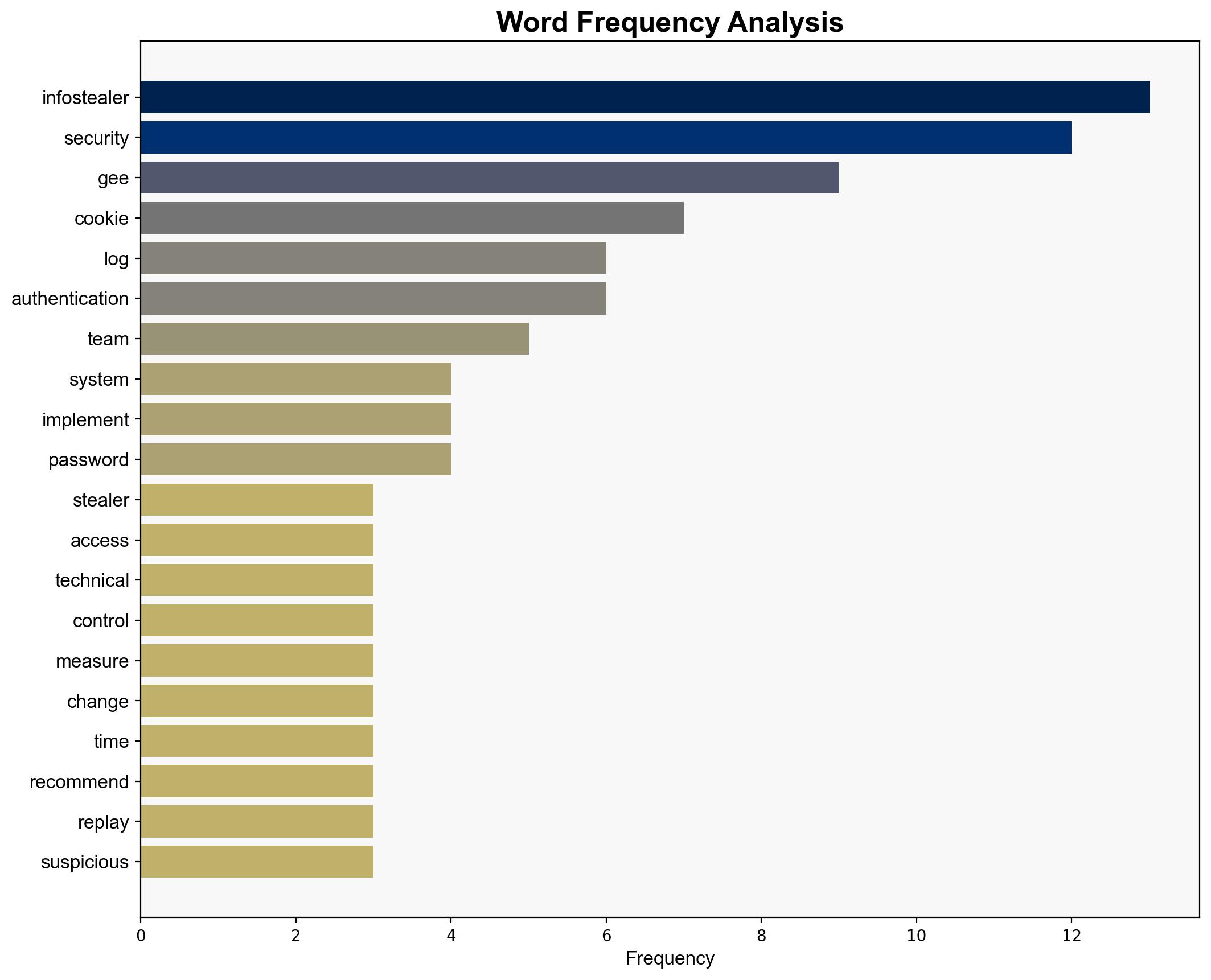
The most supported hypothesis is that the evolution of infostealer malware poses a significant and immediate threat to cybersecurity, necessitating urgent deployment of advanced defenses. Confidence in this assessment is high due to the increasing sophistication and market presence of infostealers. Recommended actions include implementing specific technical controls, adopting a zero-trust architecture, and enhancing security awareness training.
2. Competing Hypotheses
1. **Hypothesis A**: The rise in infostealer malware represents a critical escalation in cyber threats, requiring immediate and comprehensive defensive measures by security teams.
2. **Hypothesis B**: The threat from infostealer malware is overstated, with existing security measures being sufficient if properly implemented and maintained.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the documented integration of advanced capabilities in new infostealer families and their widespread availability on dark web marketplaces. Hypothesis B is weakened by evidence of infostealers bypassing traditional security controls.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that infostealer malware will continue to evolve and integrate more sophisticated capabilities. It is also assumed that current security measures are inadequate without enhancements.
– **Red Flags**: Potential over-reliance on the effectiveness of zero-trust architecture and multifactor authentication without considering user compliance and implementation challenges.
– **Blind Spots**: Lack of detailed analysis on the cost and resource implications for organizations to upgrade their defenses.
4. Implications and Strategic Risks
The increasing sophistication of infostealers could lead to more frequent and severe data breaches, impacting economic stability and national security. Organizations failing to adapt may face significant financial losses and reputational damage. The potential for cascading threats exists if infostealers are used as entry points for more destructive cyberattacks, such as ransomware.
5. Recommendations and Outlook
- Immediate deployment of advanced technical controls, including FIDO-enabled multifactor authentication and cookie replay detection mechanisms.
- Adoption of a zero-trust architecture to minimize unauthorized access risks.
- Enhanced security awareness training to ensure compliance with new security protocols.
- Scenario-based projections:
- Best Case: Successful implementation of defenses leads to a significant reduction in infostealer incidents.
- Worst Case: Failure to adapt results in widespread breaches and financial losses.
- Most Likely: Gradual improvement in security posture with a moderate decrease in successful infostealer attacks.
6. Key Individuals and Entities
Tony Gee, a principal cybersecurity consultant, is a key figure advocating for enhanced defenses against infostealers.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus