Securonix alerts hospitality sector to ongoing phishing-driven malware campaign exploiting social engineering…
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
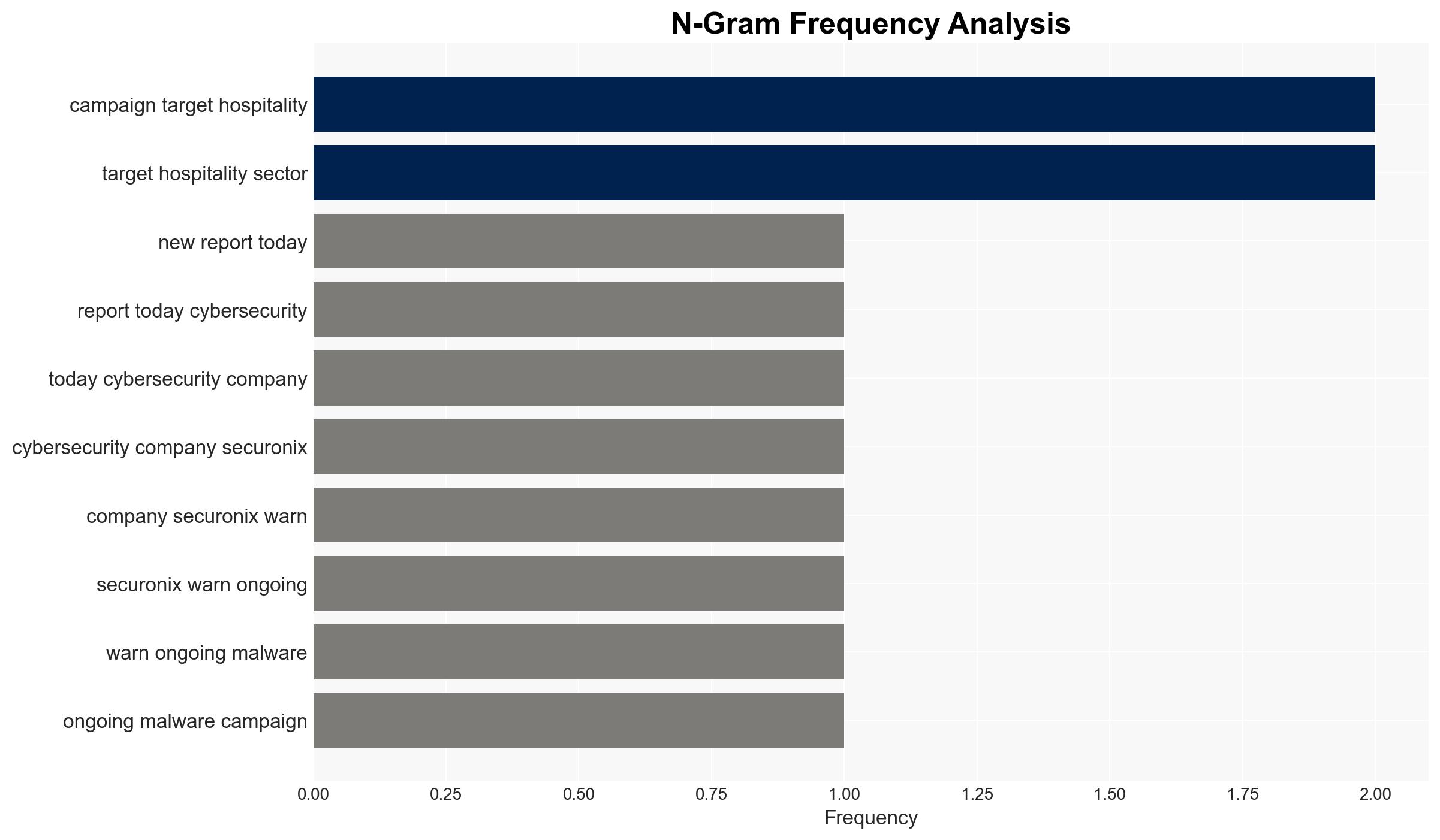
Intelligence Report: Securonix warns of malware campaign targeting hospitality sector
1. BLUF (Bottom Line Up Front)
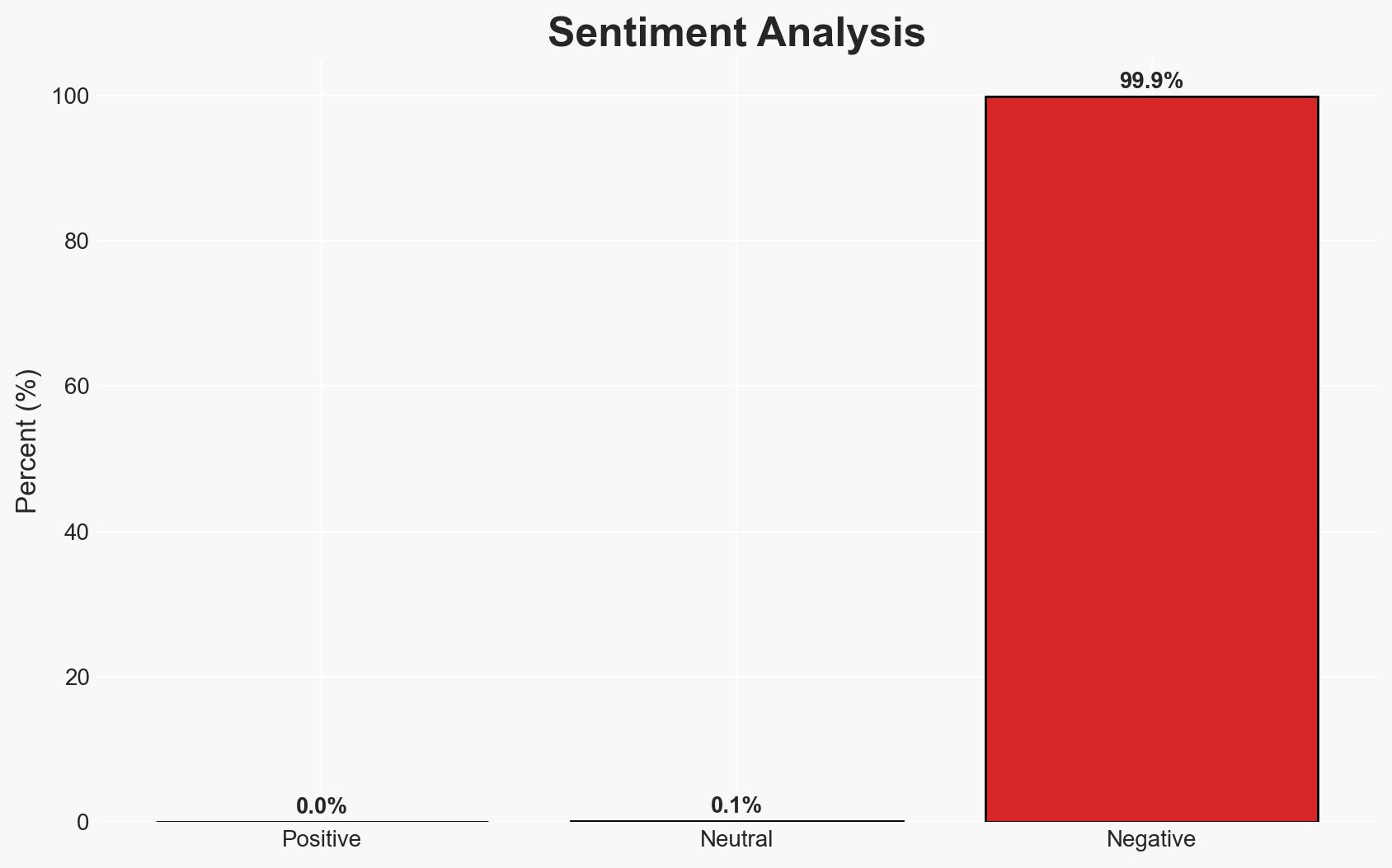
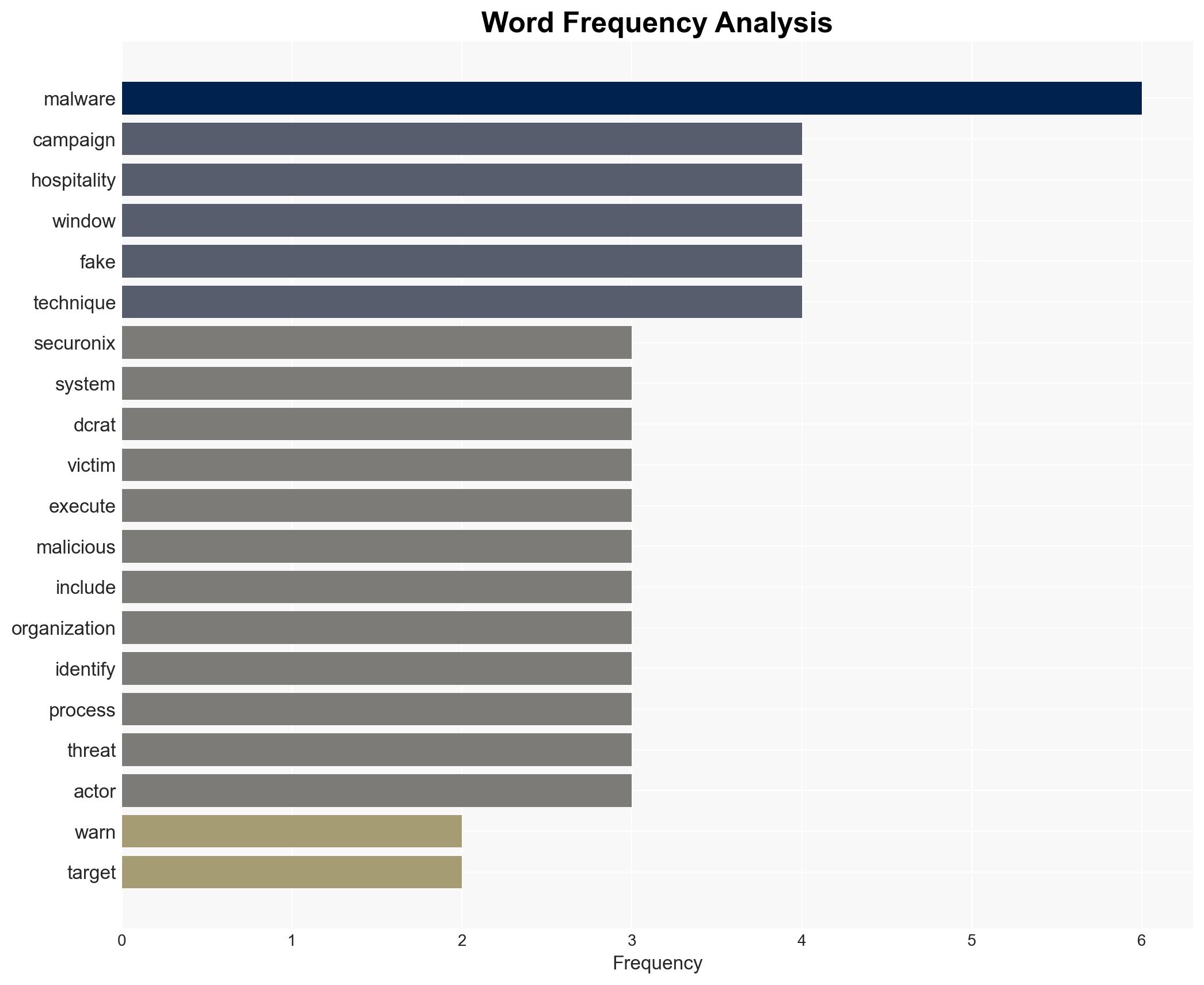
The PHALT#BLYX malware campaign is targeting the hospitality sector in Europe, utilizing advanced social engineering and trusted Windows tools to evade detection. The campaign is likely linked to Russian-speaking threat actors. There is moderate confidence in this assessment due to the presence of Cyrillic artifacts and infrastructure overlaps. The tactics could be adapted to other industries, posing a broader threat.
2. Competing Hypotheses
- Hypothesis A: The PHALT#BLYX campaign is primarily driven by Russian-speaking cybercriminals targeting the hospitality sector for financial gain. Supporting evidence includes Cyrillic debug strings and infrastructure overlaps. However, the exact identity of the threat actors remains uncertain.
- Hypothesis B: The campaign is a false flag operation designed to implicate Russian actors while the true perpetrators are from a different region or group. This hypothesis is less supported due to the lack of contradictory evidence against the Russian-speaking link.
- Assessment: Hypothesis A is currently better supported due to the technical indicators pointing towards Russian-speaking actors. Future evidence, such as different linguistic artifacts or infrastructure links, could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The campaign’s primary motive is financial gain; the use of Cyrillic artifacts indicates a Russian-speaking origin; the tactics can be adapted to other industries.
- Information Gaps: The specific identity of the threat actors; potential targets outside the hospitality sector; the full extent of the campaign’s reach.
- Bias & Deception Risks: Attribution bias towards Russian actors; potential for false flag operations; reliance on technical artifacts that could be manipulated.
4. Implications and Strategic Risks
The PHALT#BLYX campaign could evolve to target other sectors, leveraging its sophisticated social engineering tactics. This poses a risk of broader economic and operational disruptions.
- Political / Geopolitical: Potential for increased tensions between affected countries and Russia if attribution is confirmed.
- Security / Counter-Terrorism: Heightened threat environment for sectors reliant on digital infrastructure, requiring enhanced cybersecurity measures.
- Cyber / Information Space: Demonstrates evolving cyber threat tactics that bypass traditional security measures, necessitating a focus on behavioral detection.
- Economic / Social: Disruptions in the hospitality sector could lead to economic losses and affect consumer trust in digital transactions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of phishing campaigns; enhance user awareness training; deploy behavioral anomaly detection systems.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in advanced cybersecurity technologies; conduct regular security audits.
- Scenario Outlook:
- Best Case: The campaign is contained within the hospitality sector and mitigated through improved defenses.
- Worst Case: The tactics are adapted to other sectors, leading to widespread disruptions.
- Most Likely: The campaign expands to a few additional sectors, prompting a moderate increase in cybersecurity measures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, malware, social engineering, Russian-speaking threat actors, hospitality sector, phishing, cyber-espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us