Sedgwick reports data breach linked to TridentLocker ransomware affecting its federal contractor division
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Sedgwick discloses data breach after TridentLocker ransomware attack
1. BLUF (Bottom Line Up Front)
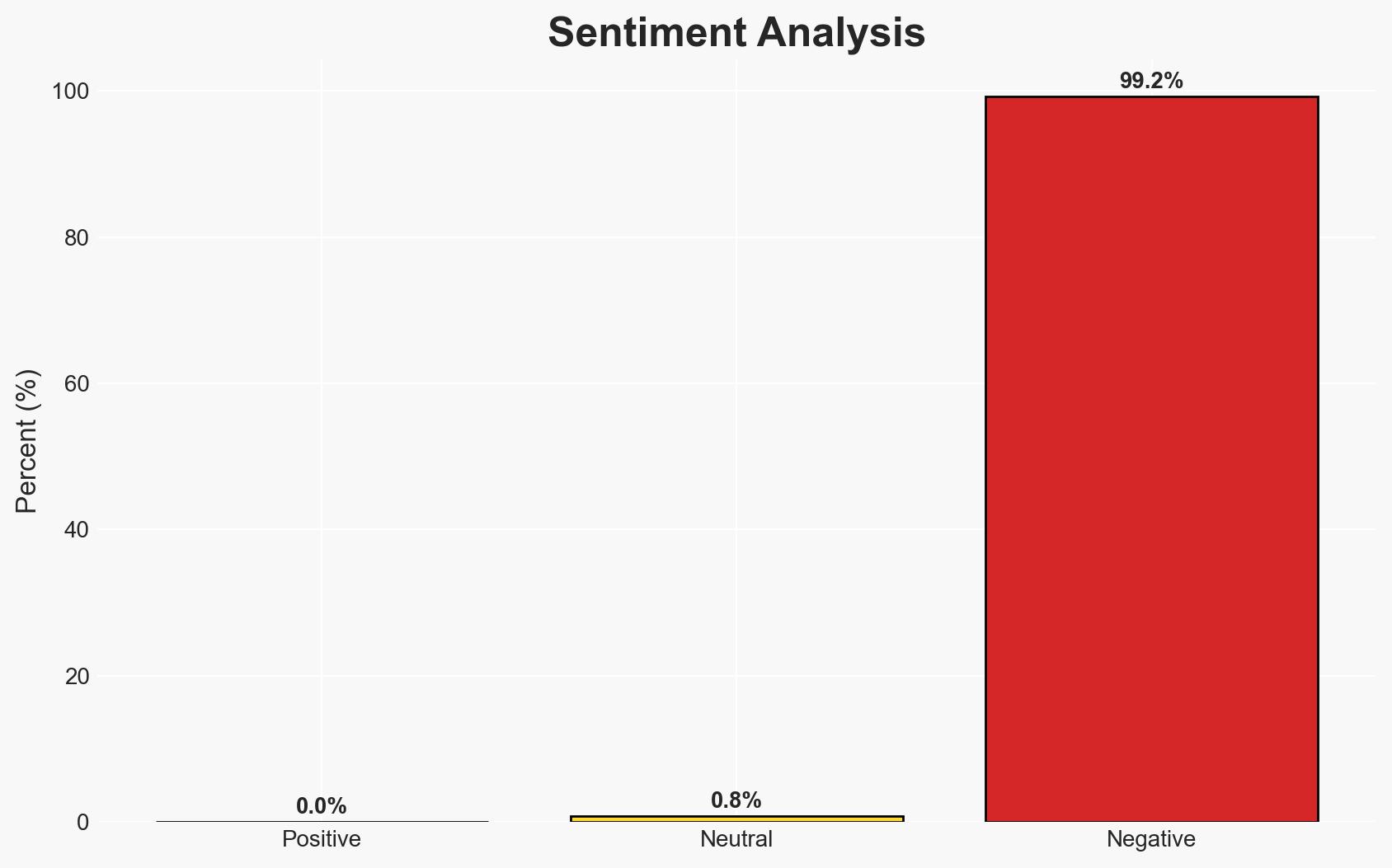
Sedgwick Government Solutions experienced a ransomware attack by TridentLocker, compromising 3.4GB of data. The incident appears contained to the subsidiary, with no broader impact on Sedgwick’s operations. The most likely hypothesis is that TridentLocker targeted Sedgwick for its federal contractor status, seeking sensitive data for extortion. Overall confidence in this assessment is moderate due to limited information on the breach’s full scope.
2. Competing Hypotheses
- Hypothesis A: TridentLocker targeted Sedgwick Government Solutions specifically for its federal contracts, aiming to exploit sensitive government-related data for extortion. Supporting evidence includes the group’s focus on government sectors and the timing of the attack. Contradicting evidence is the lack of confirmed data release or ransom payment.
- Hypothesis B: The attack was opportunistic, with TridentLocker targeting Sedgwick as part of a broader campaign against large corporations, regardless of their government ties. This is supported by the group’s history of targeting diverse sectors. However, the specific focus on a federal contractor suggests a more targeted approach.
- Assessment: Hypothesis A is currently better supported due to the specific targeting of a federal contractor and the potential value of government-related data. Indicators that could shift this judgment include evidence of broader targeting patterns or confirmation of ransom demands.
3. Key Assumptions and Red Flags
- Assumptions: Sedgwick’s segmentation of systems is effective; TridentLocker seeks financial gain through extortion; the breach is limited to the reported data volume.
- Information Gaps: Details on the specific data compromised, the exact method of breach, and whether any ransom demands were made or paid.
- Bias & Deception Risks: Potential bias in company reporting to minimize perceived impact; TridentLocker’s claims may exaggerate the breach’s scope.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny of cybersecurity practices among federal contractors and influence future policy on cyber defense. The breach may also embolden similar groups if perceived as successful.
- Political / Geopolitical: Potential for increased regulatory oversight on federal contractors’ cybersecurity measures.
- Security / Counter-Terrorism: Heightened alert for ransomware threats targeting government-affiliated entities.
- Cyber / Information Space: Possible increase in ransomware activity against high-value targets; need for enhanced cyber defense strategies.
- Economic / Social: Potential financial losses for Sedgwick and reputational damage, affecting client trust and future contracts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation, enhance monitoring of federal contractor networks, and review incident response protocols.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms, invest in advanced threat detection technologies, and conduct regular security audits.
- Scenario Outlook:
- Best: No further breaches occur, and Sedgwick strengthens its cybersecurity posture.
- Worst: Additional breaches are discovered, leading to significant data leaks and financial losses.
- Most-Likely: Sedgwick contains the breach, but faces increased scrutiny and must enhance cybersecurity measures.
6. Key Individuals and Entities
- TridentLocker (Ransomware Group)
- Sedgwick Government Solutions
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, federal contractors, data breach, cyber defense, information security, risk management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us