Seven Hidden Settings to Limit Your Phone’s Tracking Capabilities
Published on: 2025-11-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Your Phone Is Tracking More Than You Think And These 7 Hidden Settings Stop It
1. BLUF (Bottom Line Up Front)
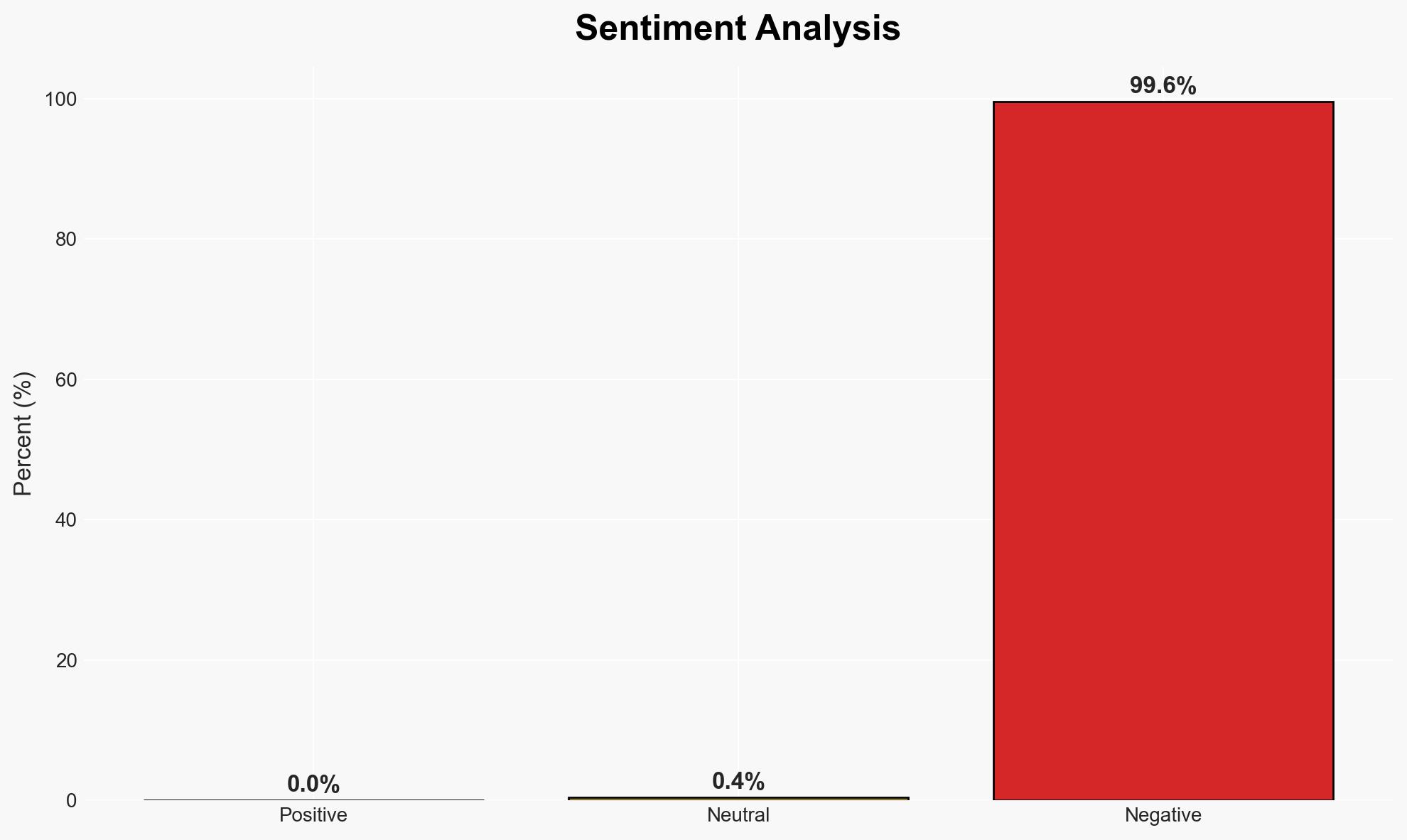
Smartphones are capable of extensive tracking through various settings that are often hidden from average users. This tracking can be mitigated by adjusting specific settings on both iPhone and Android devices. The most likely hypothesis is that users are largely unaware of these tracking mechanisms, leading to privacy vulnerabilities. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Smartphone users are generally unaware of the extent to which their devices track their movements and behaviors due to hidden settings. This is supported by the complexity and obscurity of the settings required to disable tracking.
- Hypothesis B: Users are aware of tracking capabilities but choose not to disable them due to perceived benefits or convenience. This is contradicted by the lack of user engagement with privacy settings and the technical knowledge required to adjust them.
- Assessment: Hypothesis A is currently better supported due to the intricate and non-intuitive nature of the settings involved, which likely deters average users from taking action. Indicators such as increased public awareness or simplified privacy controls could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Users lack technical knowledge to navigate privacy settings; smartphone manufacturers have no incentive to simplify privacy controls; users prioritize convenience over privacy.
- Information Gaps: Detailed statistics on user engagement with privacy settings; data on manufacturer incentives related to privacy controls.
- Bias & Deception Risks: Potential bias in assuming user ignorance; risk of manufacturer deception in presenting privacy controls as more effective than they are.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of smartphone manufacturers and calls for regulatory intervention. Over time, user awareness may increase, impacting device usage patterns and privacy expectations.
- Political / Geopolitical: Potential for regulatory actions or policy changes aimed at enhancing consumer privacy protections.
- Security / Counter-Terrorism: Increased privacy could complicate law enforcement and intelligence operations reliant on digital tracking.
- Cyber / Information Space: Enhanced privacy settings could reduce the effectiveness of data-driven cyber operations.
- Economic / Social: Changes in consumer behavior could impact business models reliant on data collection and targeted advertising.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase public awareness campaigns about privacy settings; encourage smartphone manufacturers to simplify privacy controls.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance user privacy; consider regulatory measures to enforce transparency in data collection.
- Scenario Outlook:
- Best: Users become more privacy-conscious, leading to industry-wide improvements in privacy controls.
- Worst: Continued user apathy results in unchecked data collection and potential privacy breaches.
- Most-Likely: Gradual increase in user awareness and minor adjustments by manufacturers to privacy settings.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, privacy, smartphone tracking, user awareness, data collection, regulatory implications, consumer behavior, digital privacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us