Severe n8n Flaw CVE-2026-21858 (CVSS 10.0) Enables Unauthenticated Remote Control of Affected Systems
Published on: 2026-01-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Critical n8n Vulnerability CVSS 100 Allows Unauthenticated Attackers to Take Full Control
1. BLUF (Bottom Line Up Front)
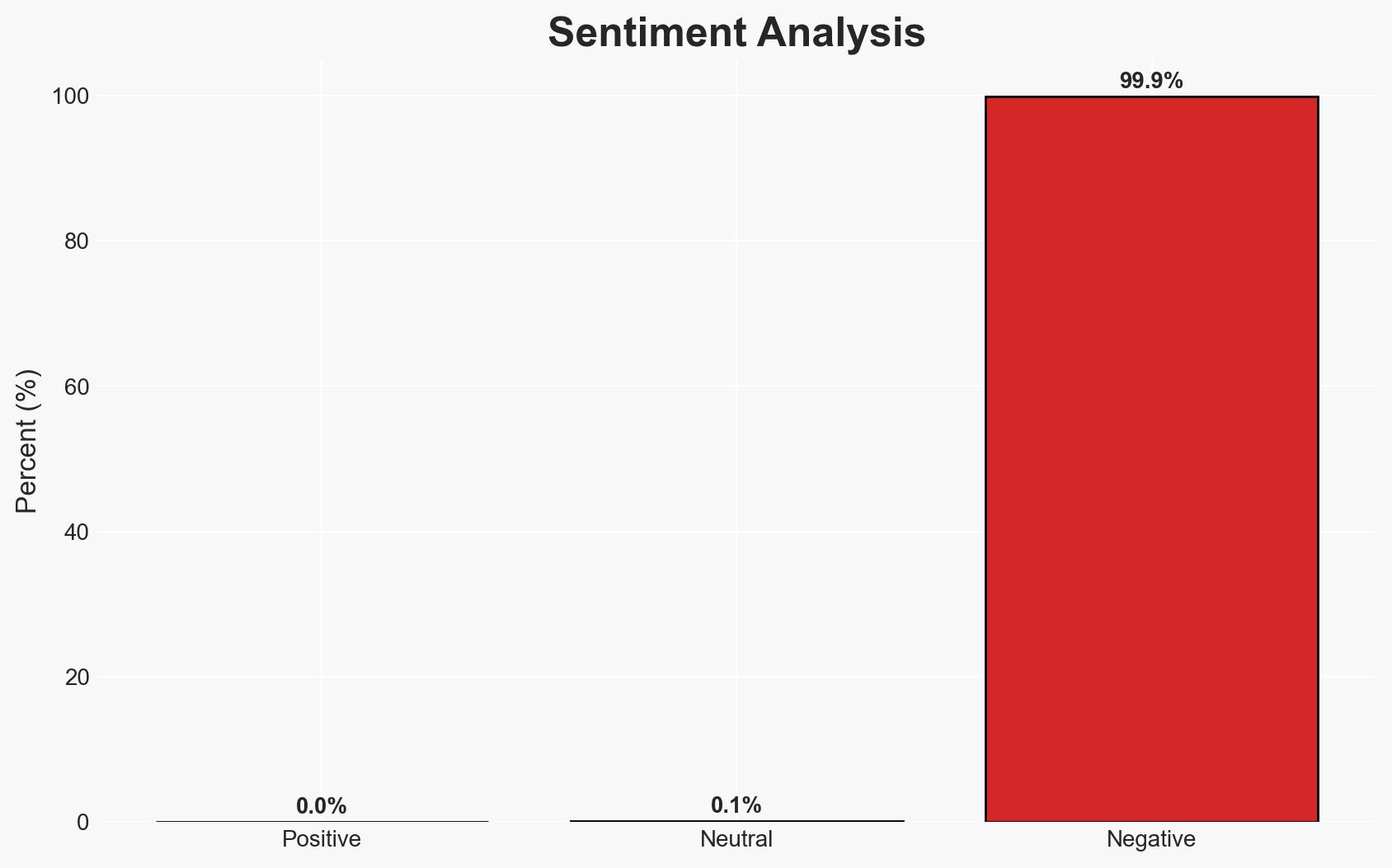
The discovery of CVE-2026-21858, a critical vulnerability in the n8n workflow automation platform, poses a significant risk of unauthorized access and control over affected systems. This vulnerability, which does not require authentication, could lead to severe data breaches and system compromises. The most likely hypothesis is that this vulnerability will be actively exploited by threat actors, affecting organizations using n8n versions prior to 1.121.0. Overall confidence in this assessment is moderate, given the limited information on exploitation in the wild.
2. Competing Hypotheses
- Hypothesis A: The vulnerability will be rapidly exploited by cybercriminals and state-sponsored actors to gain unauthorized access to sensitive systems. Supporting evidence includes the high CVSS score and the unauthenticated nature of the exploit. Key uncertainties involve the speed and scale of exploitation.
- Hypothesis B: Organizations will quickly patch the vulnerability, minimizing exploitation opportunities. This is supported by the availability of a fix and the advisory issued by n8n. Contradicting evidence includes potential delays in patch deployment due to operational constraints.
- Assessment: Hypothesis A is currently better supported due to the critical nature of the vulnerability and the potential for rapid exploitation. Indicators that could shift this judgment include widespread adoption of the patch and reports of exploitation in the wild.
3. Key Assumptions and Red Flags
- Assumptions: Organizations are aware of the vulnerability and have the capability to apply patches; threat actors have the technical capability to exploit the vulnerability; n8n’s advisory reaches all affected users.
- Information Gaps: Lack of data on current exploitation attempts and the number of unpatched systems; unclear if other vulnerabilities in n8n are being exploited concurrently.
- Bias & Deception Risks: Potential over-reliance on vendor advisories; risk of underestimating the capability of threat actors to exploit the vulnerability quickly.
4. Implications and Strategic Risks
This vulnerability could lead to significant security breaches, impacting organizations’ operational integrity and data confidentiality. The situation could evolve with increased cyber threat activity targeting unpatched systems.
- Political / Geopolitical: Potential for state-sponsored actors to leverage the vulnerability for espionage or disruptive operations.
- Security / Counter-Terrorism: Increased risk of cyber-attacks on critical infrastructure and sensitive sectors.
- Cyber / Information Space: Potential for widespread data breaches and unauthorized access to sensitive information.
- Economic / Social: Possible financial losses and reputational damage for affected organizations, leading to broader economic impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply patches to all affected n8n systems; increase monitoring for signs of exploitation; disseminate threat intelligence to stakeholders.
- Medium-Term Posture (1–12 months): Enhance vulnerability management practices; foster partnerships for threat intelligence sharing; invest in cybersecurity training and awareness.
- Scenario Outlook:
- Best: Rapid patch adoption minimizes exploitation, with no significant breaches reported.
- Worst: Widespread exploitation leads to major data breaches and operational disruptions.
- Most-Likely: Moderate exploitation occurs, with some organizations experiencing breaches due to delayed patching.
6. Key Individuals and Entities
- Cyera Research Labs
- Dor Attias
- n8n
- The Hacker News
7. Thematic Tags
cybersecurity, vulnerability management, cyber threat, information security, patch management, workflow automation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us