Severe Vulnerabilities in n8n Platform Enable Full Server Control and Credential Theft
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Two Critical Flaws in n8n AI Workflow Automation Platform Allow Complete Takeover
1. BLUF (Bottom Line Up Front)
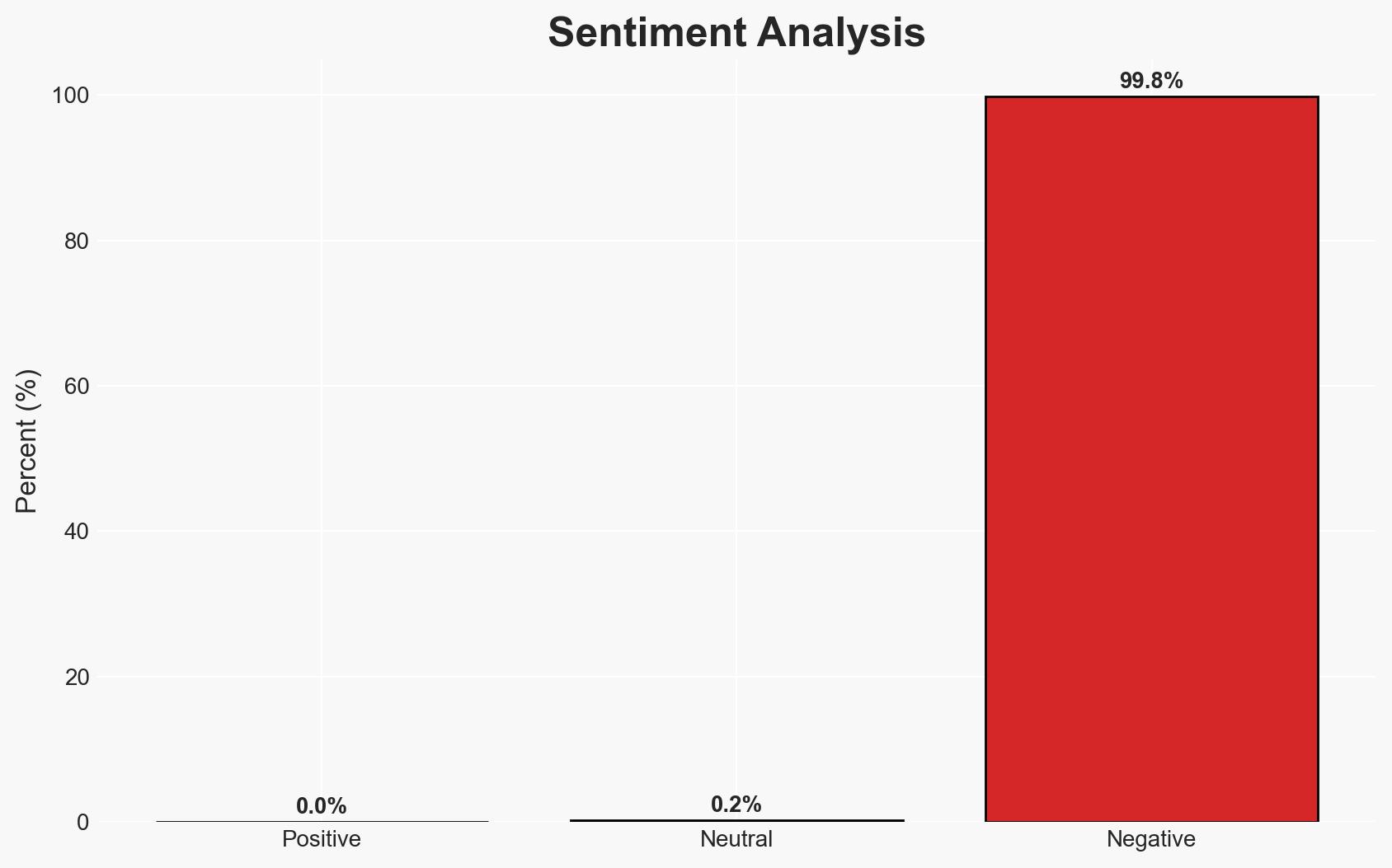
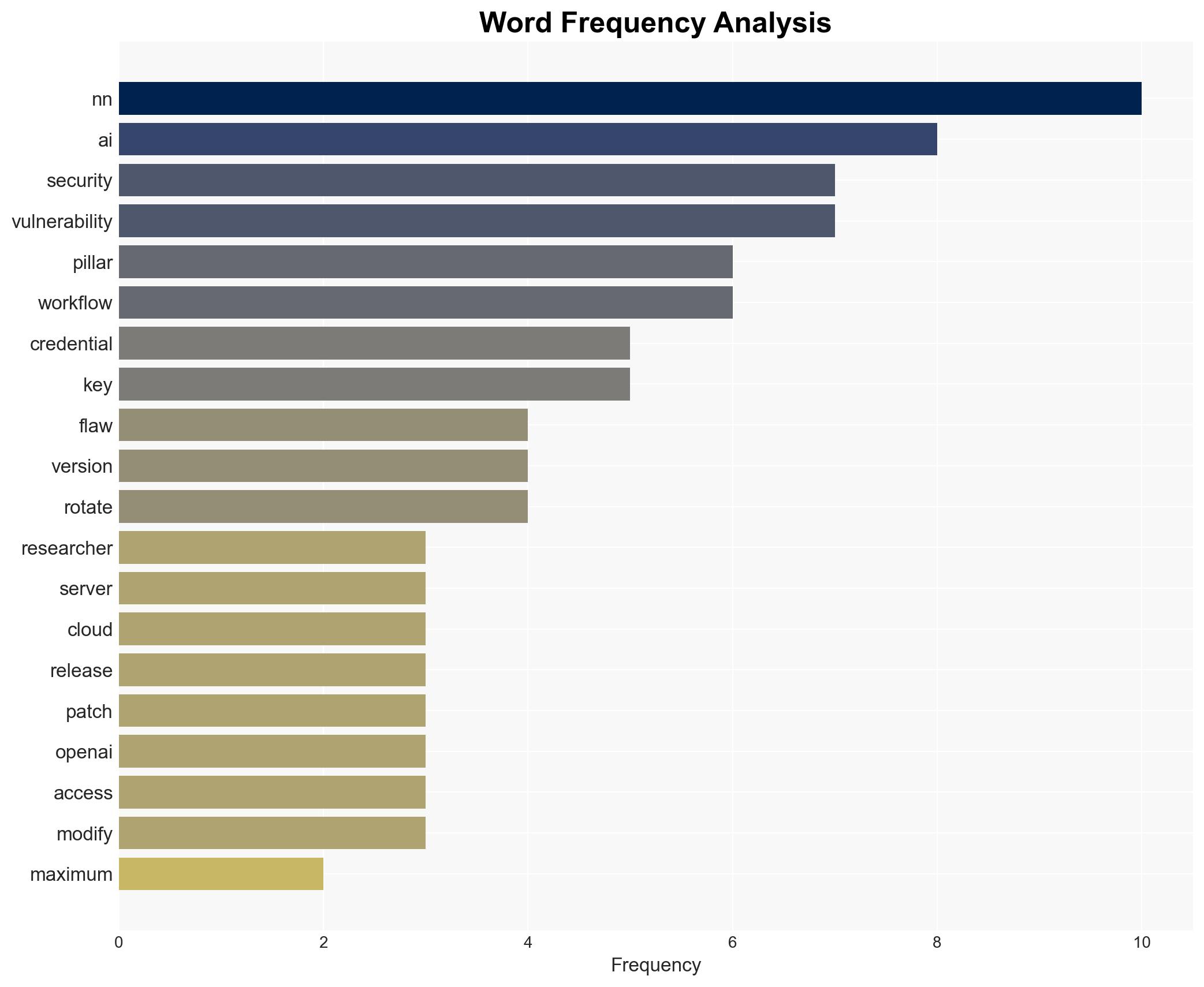
The discovery of two critical vulnerabilities in the n8n AI workflow automation platform poses a significant security risk, potentially allowing attackers to gain complete server control and access sensitive credentials. This affects enterprises using n8n for AI orchestration, exposing them to data breaches and operational disruptions. The most likely hypothesis is that these vulnerabilities will be actively exploited if not promptly mitigated. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities in n8n will be rapidly exploited by cybercriminals due to the high value of the exposed targets and the ease of exploitation. Supporting evidence includes the critical nature of the vulnerabilities (CVSS score of 10.0) and the potential for widespread credential theft. Key uncertainties include the speed and extent of patch adoption by affected enterprises.
- Hypothesis B: The vulnerabilities will have limited exploitation due to swift patch deployment and effective mitigation strategies by affected organizations. This is supported by the release of a patched version (2.4.0) and recommended mitigation actions. However, the lack of a CVE identifier and potential delays in patch implementation contradict this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the critical severity of the vulnerabilities and the potential for significant impact if exploited. Indicators that could shift this judgment include widespread and rapid patch adoption and effective monitoring and response by affected organizations.
3. Key Assumptions and Red Flags
- Assumptions: n8n users will prioritize patching and mitigation; attackers have the capability to exploit these vulnerabilities; affected enterprises have adequate monitoring systems in place.
- Information Gaps: The extent of patch adoption among n8n users; specific details of the second vulnerability; the presence of active exploitation in the wild.
- Bias & Deception Risks: Potential bias in reporting by Pillar Security due to vested interests; lack of independent verification of vulnerability details; possible underreporting of exploitation incidents.
4. Implications and Strategic Risks
The vulnerabilities in n8n could lead to significant disruptions if exploited, affecting not only the targeted organizations but also broader industry trust in AI workflow automation platforms.
- Political / Geopolitical: Potential for increased regulatory scrutiny on AI platforms and cybersecurity standards.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks targeting AI systems, potentially impacting critical infrastructure.
- Cyber / Information Space: Increased cyber threat landscape complexity, with potential for data breaches and information manipulation.
- Economic / Social: Economic impact on enterprises due to data breaches and operational disruptions; potential loss of consumer trust in AI technologies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urge all n8n users to upgrade to version 2.4.0 or later, rotate credentials, and implement enhanced monitoring of AI workflows.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for ongoing threat intelligence; invest in resilience measures and employee training on cybersecurity best practices.
- Scenario Outlook:
- Best Case: Rapid patch adoption and effective mitigation prevent widespread exploitation.
- Worst Case: Delayed patching leads to significant data breaches and operational disruptions.
- Most Likely: Mixed response with some exploitation incidents, but overall containment through proactive measures.
6. Key Individuals and Entities
- Pillar Security (researchers)
- Eilon Cohen (AI security researcher at Pillar Security)
- n8n (platform maintainers)
- Infosecurity (media outlet)
7. Thematic Tags
cybersecurity, AI vulnerabilities, data breaches, workflow automation, enterprise security, patch management, credential theft
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us