ShadowSilk Campaign Targets Central Asian Governments – Infosecurity Magazine
Published on: 2025-08-27
Intelligence Report: ShadowSilk Campaign Targets Central Asian Governments – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
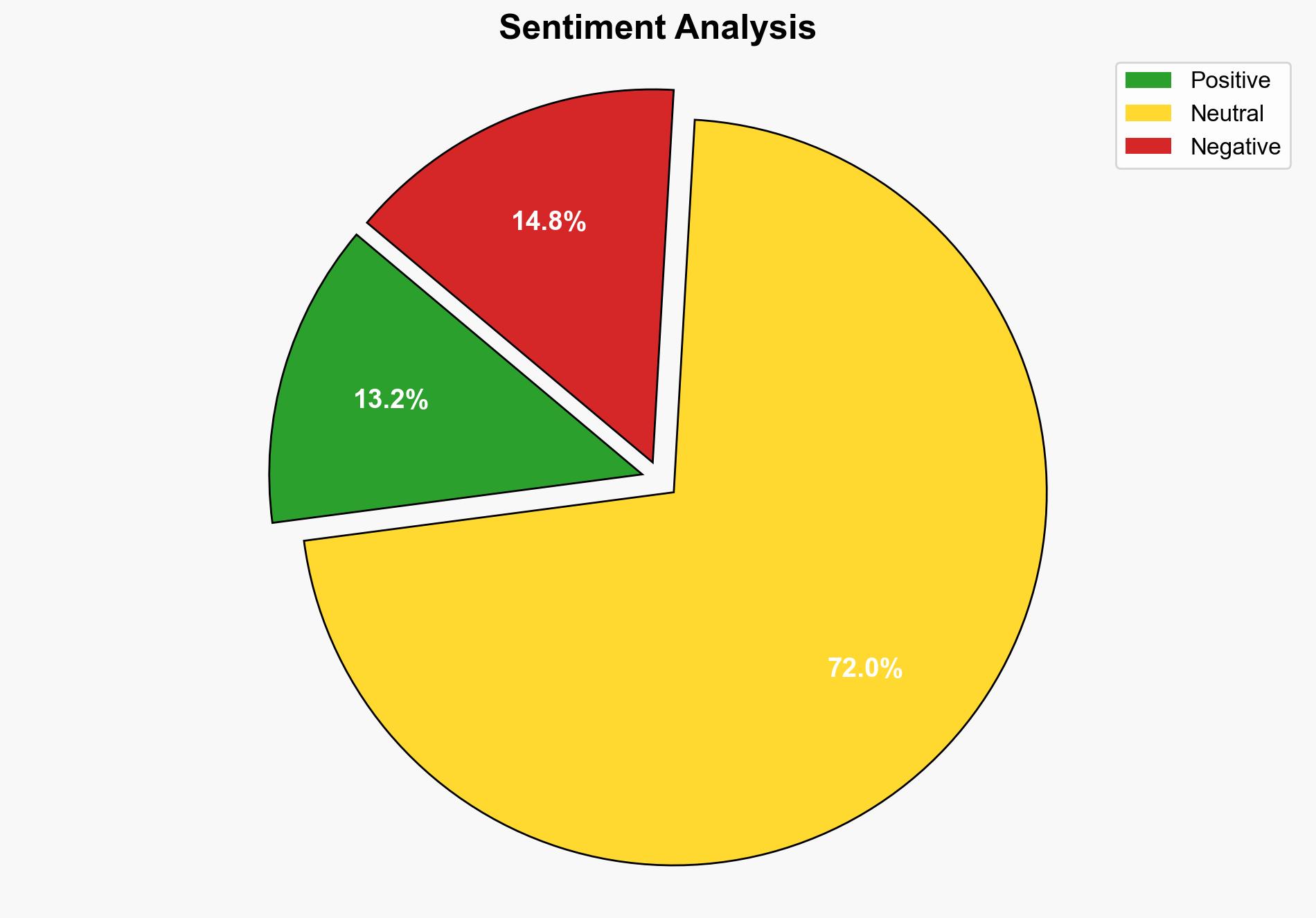
The ShadowSilk campaign, potentially involving Russian and Chinese operators, poses a significant cybersecurity threat to Central Asian governments. The most supported hypothesis suggests a dual-nation operation aimed at data theft and long-term infiltration. Confidence in this assessment is moderate due to the complexity of attributing cyber operations. Immediate action is recommended to enhance cybersecurity measures, focusing on email protection and proactive threat hunting.
2. Competing Hypotheses
1. **Hypothesis A**: ShadowSilk is a coordinated operation between Russian and Chinese actors targeting Central Asian governments for data theft and strategic espionage.
2. **Hypothesis B**: ShadowSilk is primarily a Russian-led operation, with Chinese elements involved only peripherally or as a false flag to obscure the true origin.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the presence of both Russian and Chinese language elements in the malware development and infrastructure, as well as the strategic interest both nations have in the region.
3. Key Assumptions and Red Flags
– **Assumptions**: The assumption that language indicators directly correlate with national involvement may be misleading due to potential false flag operations.
– **Red Flags**: The reliance on language and infrastructure analysis could be deceptive, as cyber actors often use misleading tactics to obscure their identity.
– **Blind Spots**: Lack of direct evidence linking specific individuals or state entities to the operation.
4. Implications and Strategic Risks
The ShadowSilk campaign could lead to significant geopolitical tensions in the region, particularly if state-sponsored involvement is confirmed. The campaign’s focus on data theft and long-term infiltration suggests a strategic aim to undermine governmental stability and gather intelligence. This could escalate into broader cyber conflicts or diplomatic disputes.
5. Recommendations and Outlook
- Enhance cybersecurity frameworks with a focus on email protection and regular patch management.
- Implement proactive threat hunting and monitoring of dark web forums for data leaks.
- Scenario Projections:
- Best Case: Strengthened defenses prevent further breaches, and diplomatic channels mitigate tensions.
- Worst Case: Continued infiltration leads to significant data breaches and geopolitical instability.
- Most Likely: Ongoing cyber skirmishes with intermittent breaches and gradual improvements in defense mechanisms.
6. Key Individuals and Entities
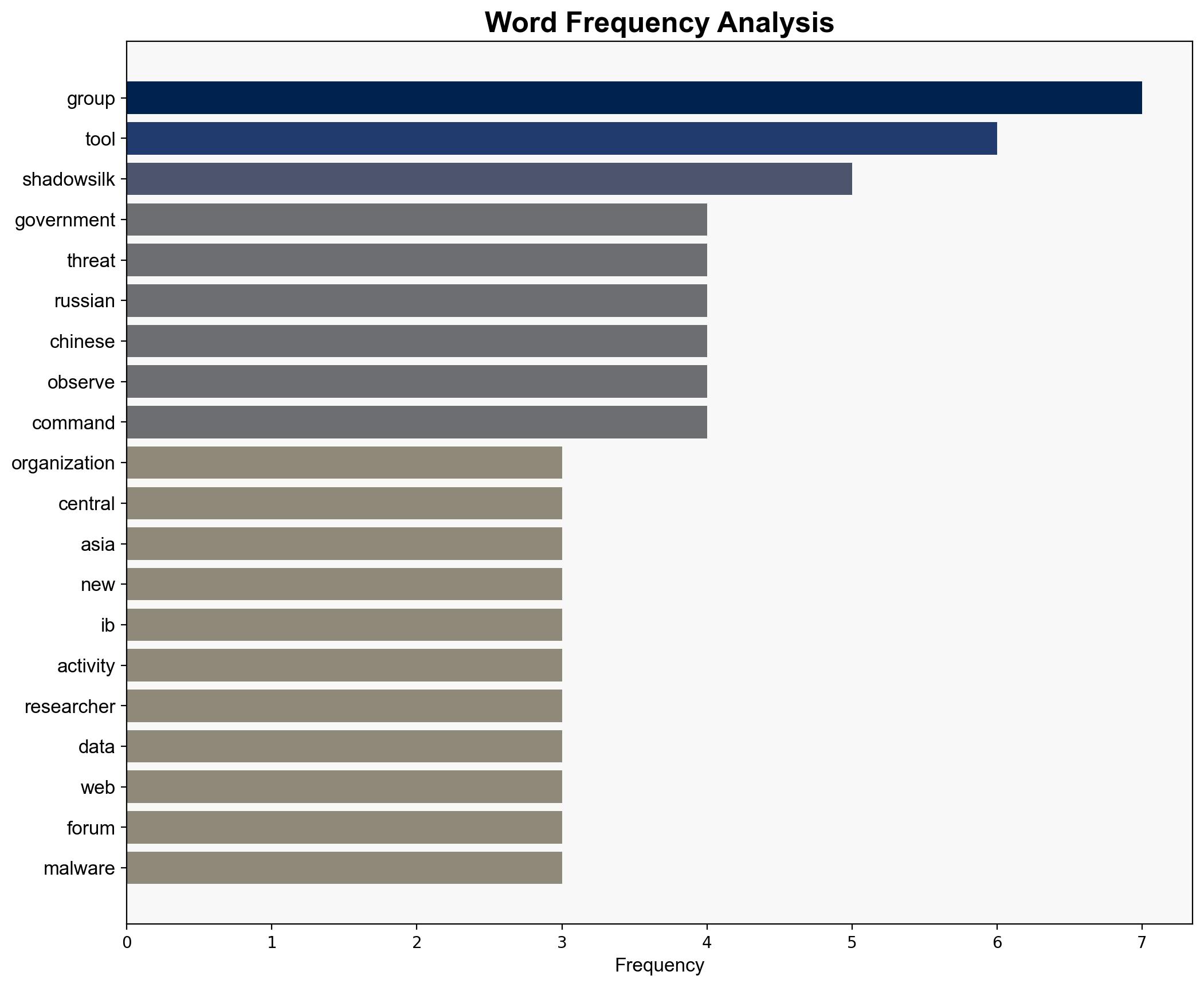
No specific individuals are named in the intelligence provided. The entities involved include the ShadowSilk group, Group-IB, and CERT-KG.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus