Shai-Hulud v2 Campaign Expands to Maven, Compromising Thousands of Secrets Across Ecosystems
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Shai-Hulud v2 Campaign Spreads From npm to Maven Exposing Thousands of Secrets
1. BLUF (Bottom Line Up Front)
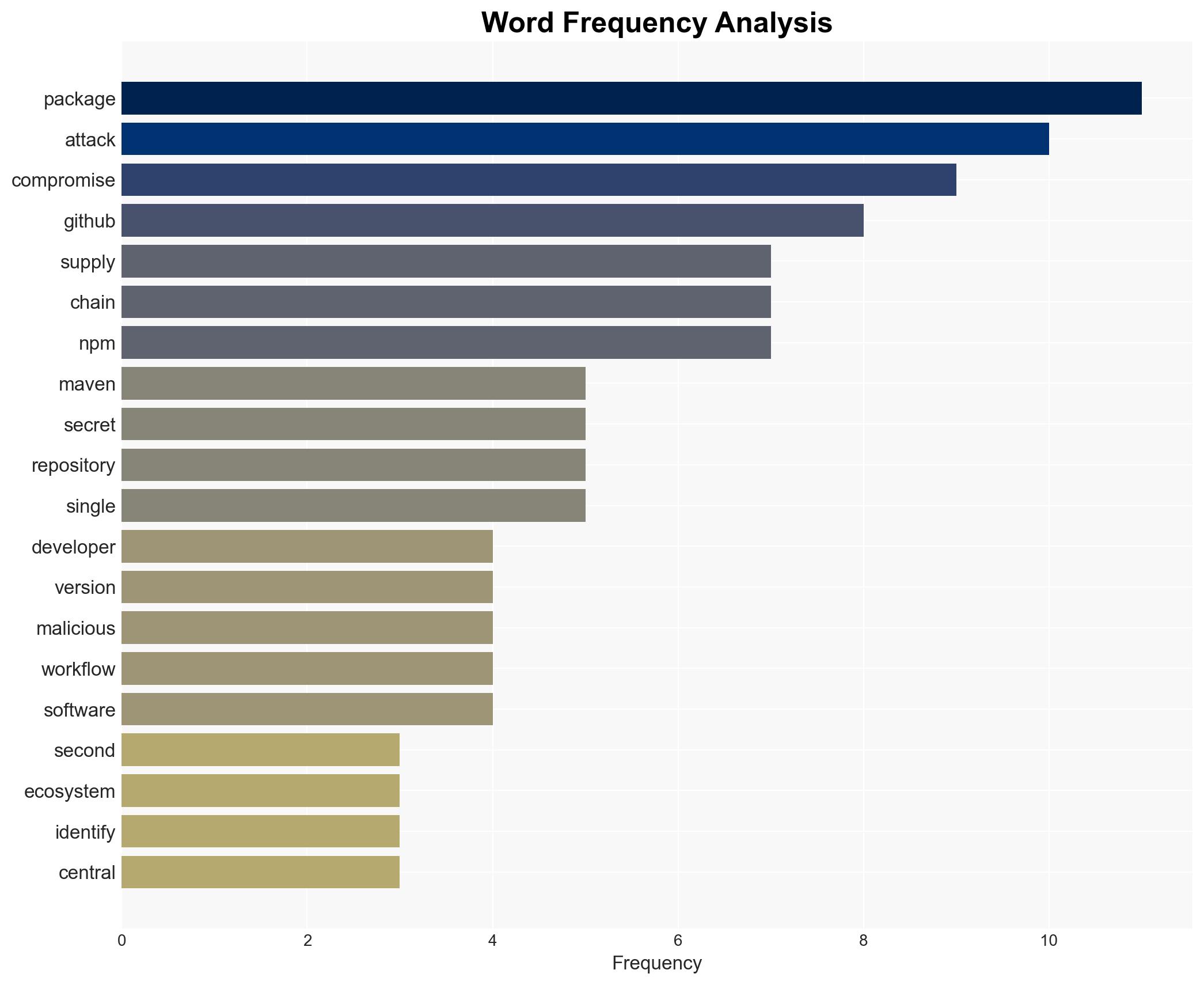
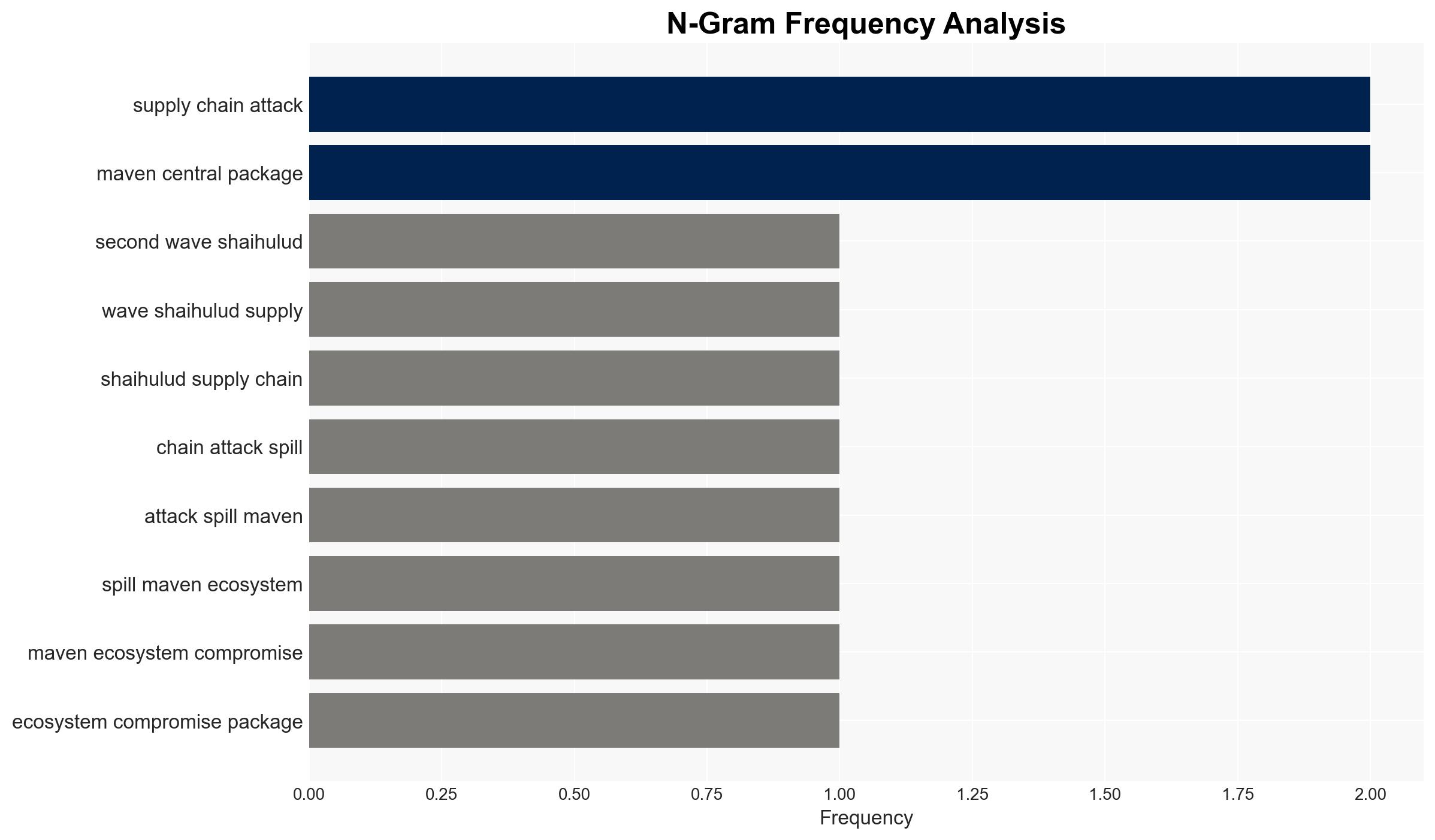
The Shai-Hulud v2 campaign represents a significant escalation in supply chain attacks, transitioning from npm to the Maven ecosystem. This campaign has compromised thousands of secrets, affecting developers globally. The most likely hypothesis is that this is a coordinated effort to exploit software distribution pathways, with moderate confidence in this assessment due to the evolving nature of the attack and limited visibility into the threat actor’s full capabilities and intentions.
2. Competing Hypotheses
- Hypothesis A: The Shai-Hulud v2 campaign is primarily aimed at stealing sensitive data such as API keys and cloud credentials through a sophisticated supply chain attack. This is supported by the campaign’s focus on embedding malicious code in widely used software packages and the use of stealthy techniques to exfiltrate data. However, there is uncertainty regarding the ultimate goals of the attackers beyond data theft.
- Hypothesis B: The campaign is a broader effort to establish persistent access within compromised environments for future operations, possibly including espionage or sabotage. This is suggested by the use of backdoors and the potential for arbitrary command execution. Contradicting this is the lack of direct evidence linking the campaign to specific long-term objectives.
- Assessment: Hypothesis A is currently better supported due to the immediate focus on data exfiltration and the technical indicators observed. Key indicators that could shift this judgment include evidence of long-term persistence mechanisms or strategic targeting of specific organizations.
3. Key Assumptions and Red Flags
- Assumptions: The threat actor has the capability to exploit both npm and Maven ecosystems; the primary objective is data theft; affected organizations have limited detection and response capabilities.
- Information Gaps: The identity and motivations of the threat actor; the full scope of compromised entities; the potential for further evolution of the attack techniques.
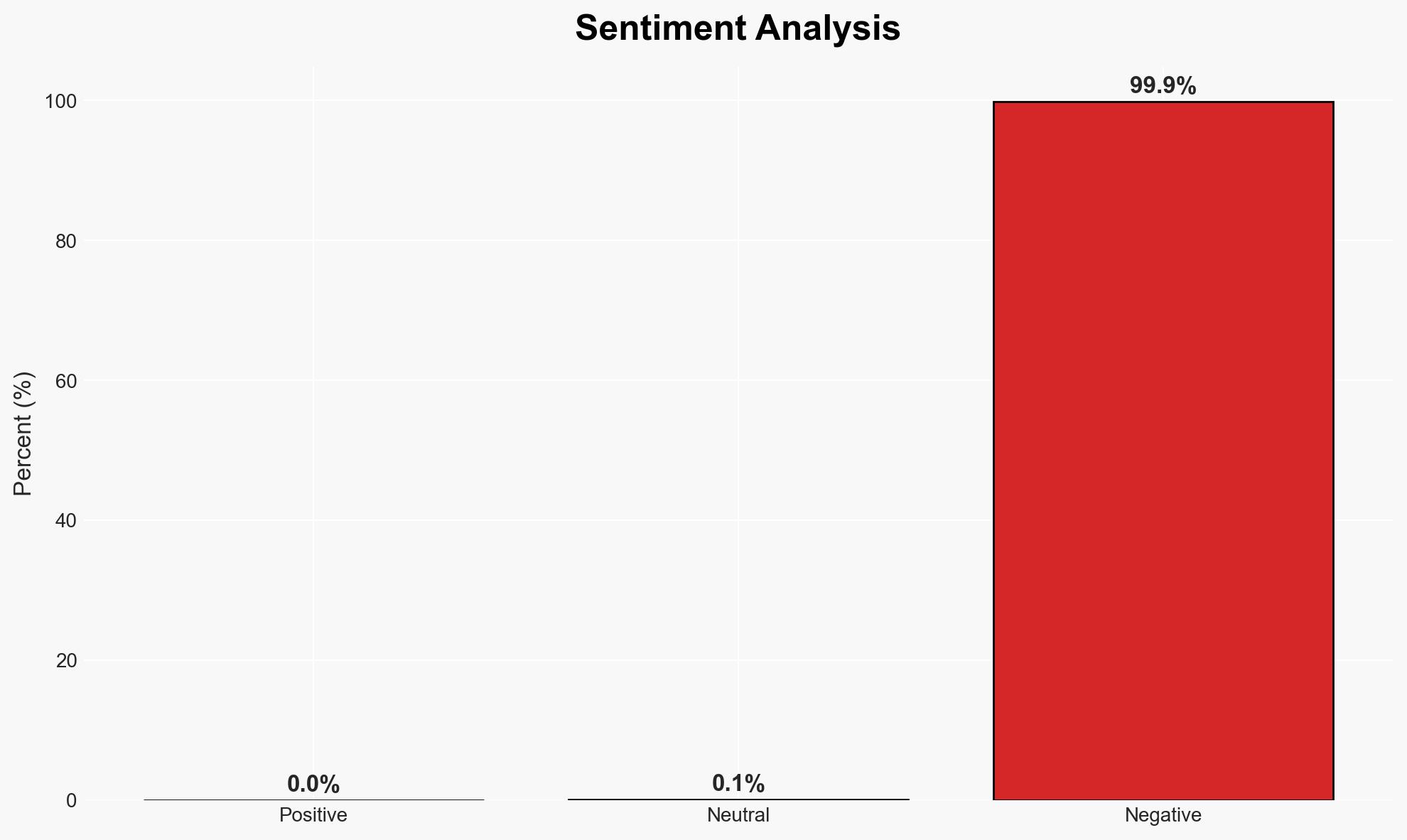
- Bias & Deception Risks: Confirmation bias towards data theft as the primary motive; potential manipulation of public reporting by the threat actor to mislead investigators.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and security measures within software development ecosystems, potentially disrupting supply chains and affecting developer trust.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is suspected or confirmed.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation towards securing software supply chains.
- Cyber / Information Space: Increased focus on securing CI/CD pipelines and software repositories; potential for copycat attacks.
- Economic / Social: Possible economic impact on affected companies and industries reliant on compromised software.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of npm and Maven ecosystems; deploy threat intelligence sharing among affected entities; conduct immediate audits of software dependencies.
- Medium-Term Posture (1–12 months): Develop resilience measures for supply chain security; foster public-private partnerships for threat intelligence sharing; invest in capability development for detecting and mitigating supply chain attacks.
- Scenario Outlook:
- Best: Rapid containment and mitigation with minimal long-term impact.
- Worst: Widespread compromise leading to significant data breaches and operational disruptions.
- Most-Likely: Continued evolution of attack techniques with periodic disruptions and data theft incidents.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us