SharePoint zero-day CVE-2025-53770 actively exploited in the wild – Securityaffairs.com
Published on: 2025-07-21
Intelligence Report: SharePoint zero-day CVE-2025-53770 actively exploited in the wild – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
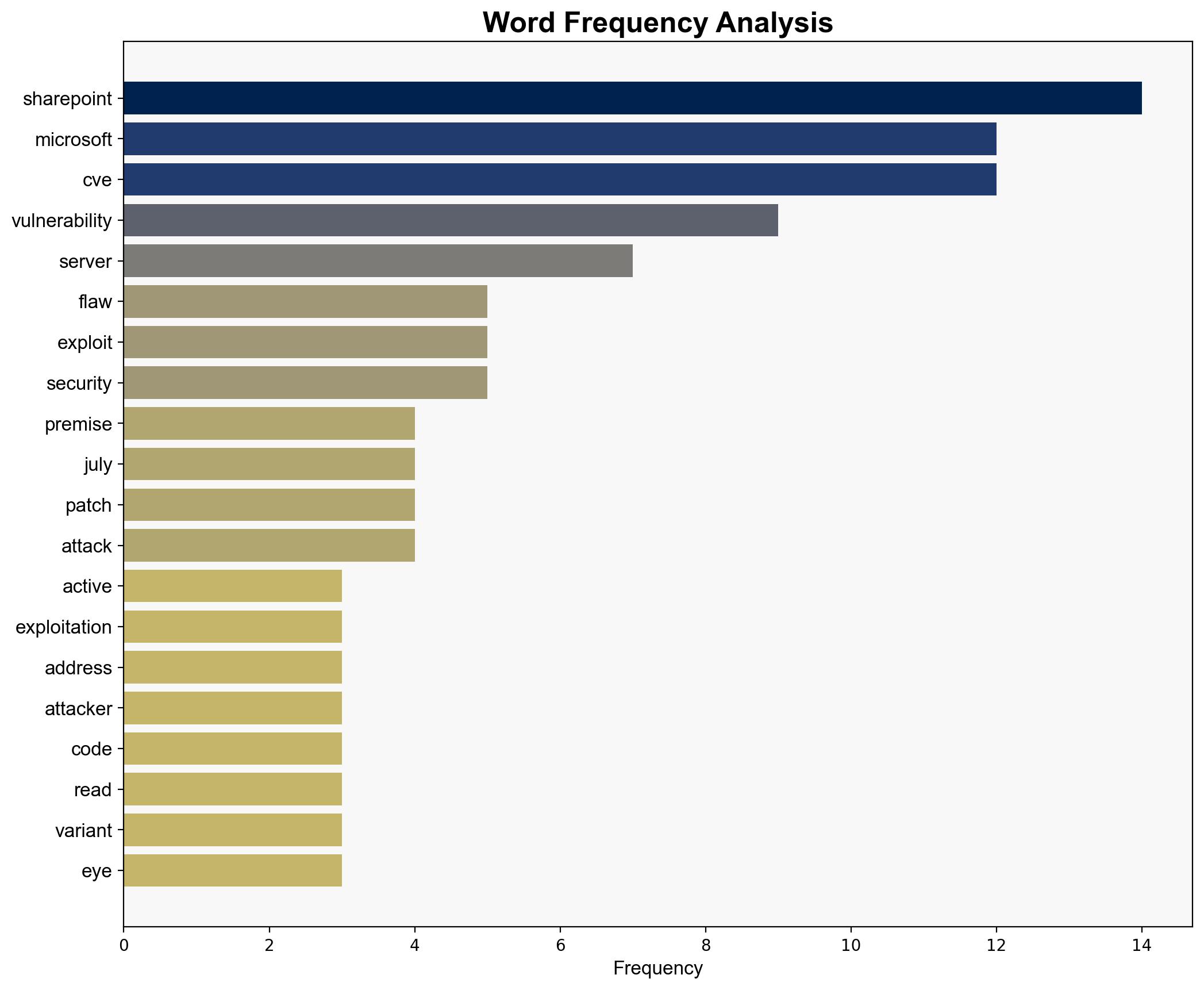
The SharePoint zero-day vulnerability, CVE-2025-53770, is actively exploited, posing significant risks to organizations using on-premise SharePoint servers. Microsoft has yet to release a comprehensive patch, but mitigation strategies are advised. Immediate actions include enabling AMSI integration and deploying Microsoft Defender to protect against exploitation. The vulnerability allows unauthorized code execution, complicating detection and increasing the potential for lateral movement within networks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated adversary actions reveal potential exploitation pathways, emphasizing the need for robust defensive measures.
Indicators Development
Key indicators include unauthorized code execution attempts and unusual network behavior, crucial for early threat detection.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued exploitation, necessitating immediate defensive actions.
Network Influence Mapping
Mapping reveals potential influence and impact of adversaries exploiting the vulnerability, aiding in prioritizing defensive efforts.
3. Implications and Strategic Risks
The exploitation of CVE-2025-53770 could lead to significant data breaches, loss of sensitive information, and operational disruptions. The vulnerability’s ability to facilitate lateral movement increases the risk of widespread network compromise. Organizations may face cascading effects, including reputational damage and financial losses.
4. Recommendations and Outlook
- Implement recommended mitigations immediately, including AMSI integration and Microsoft Defender deployment.
- Conduct thorough compromise assessments to identify and address potential breaches.
- Prepare for scenario-based outcomes:
- Best case: Successful mitigation prevents further exploitation.
- Worst case: Widespread exploitation leads to major data breaches.
- Most likely: Continued targeted attacks until a comprehensive patch is released.
5. Key Individuals and Entities
Viettel Cyber Security, Trend Micro’s ZDI, Eye Security, Palo Alto Networks
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus