ShinyHunters claims data breach at Panera Bread exposes over 14 million records, including personal informati…
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Let them eat sourdough ShinyHunters claims Panera Bread as stolen credentials victim
1. BLUF (Bottom Line Up Front)
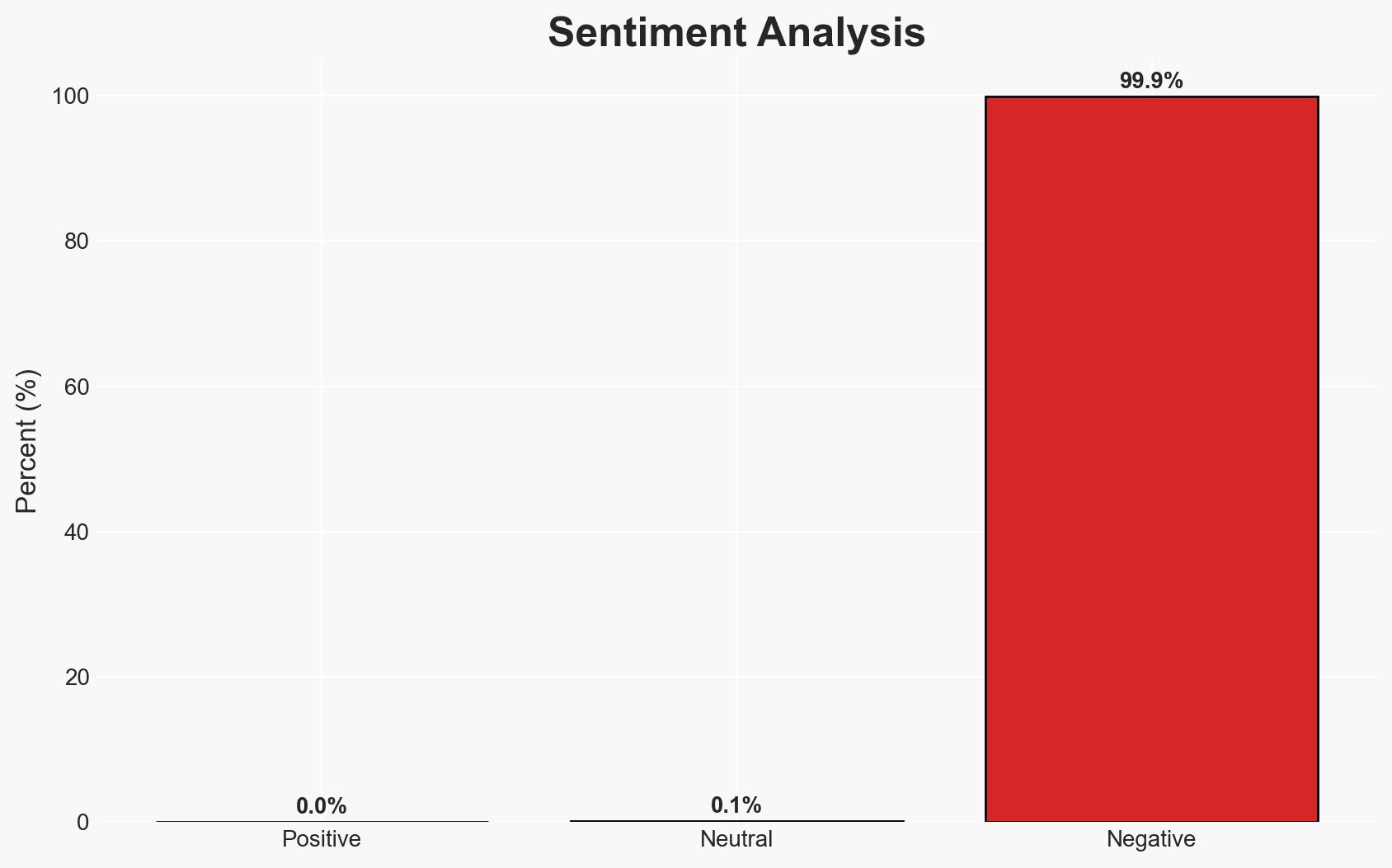
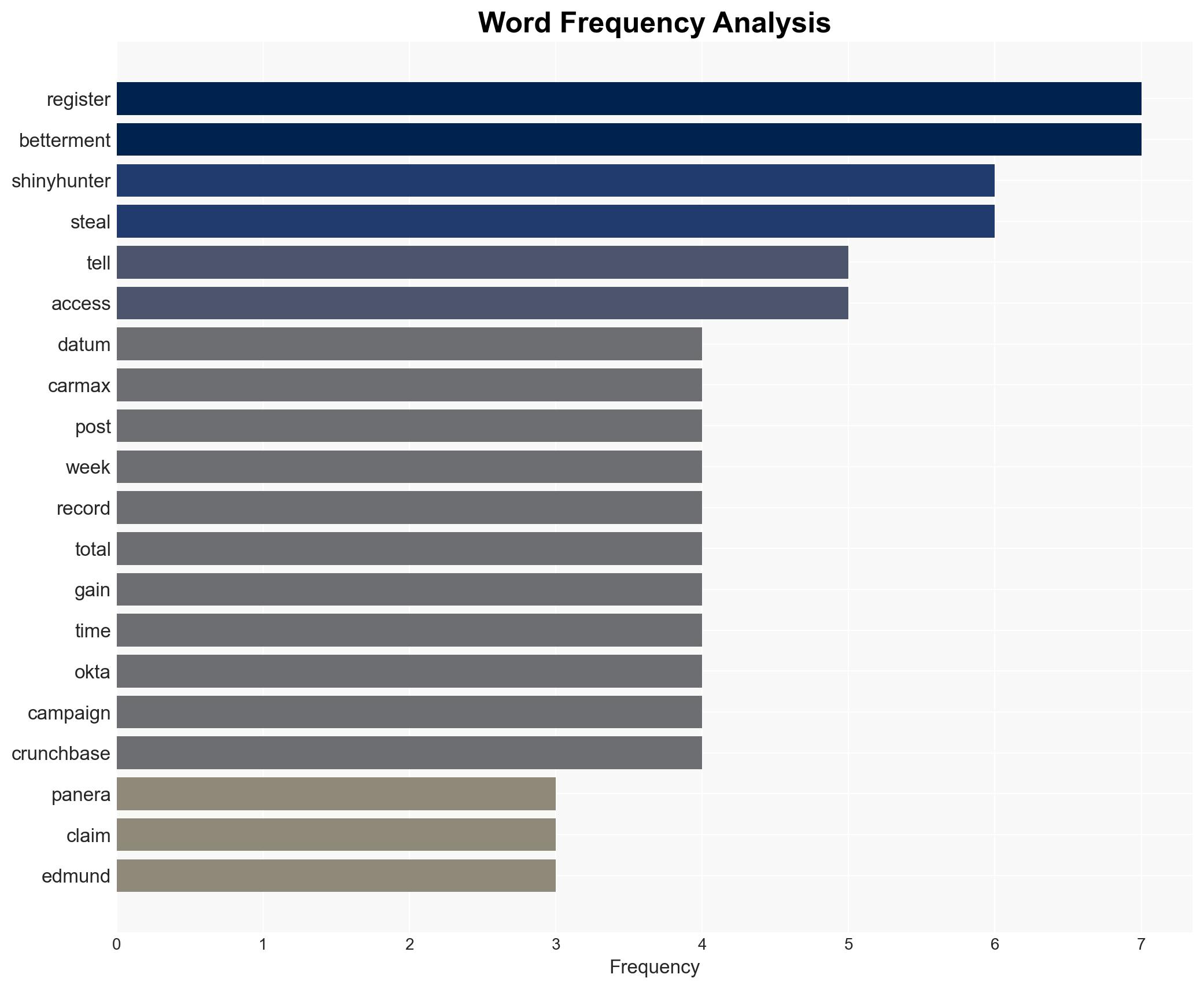
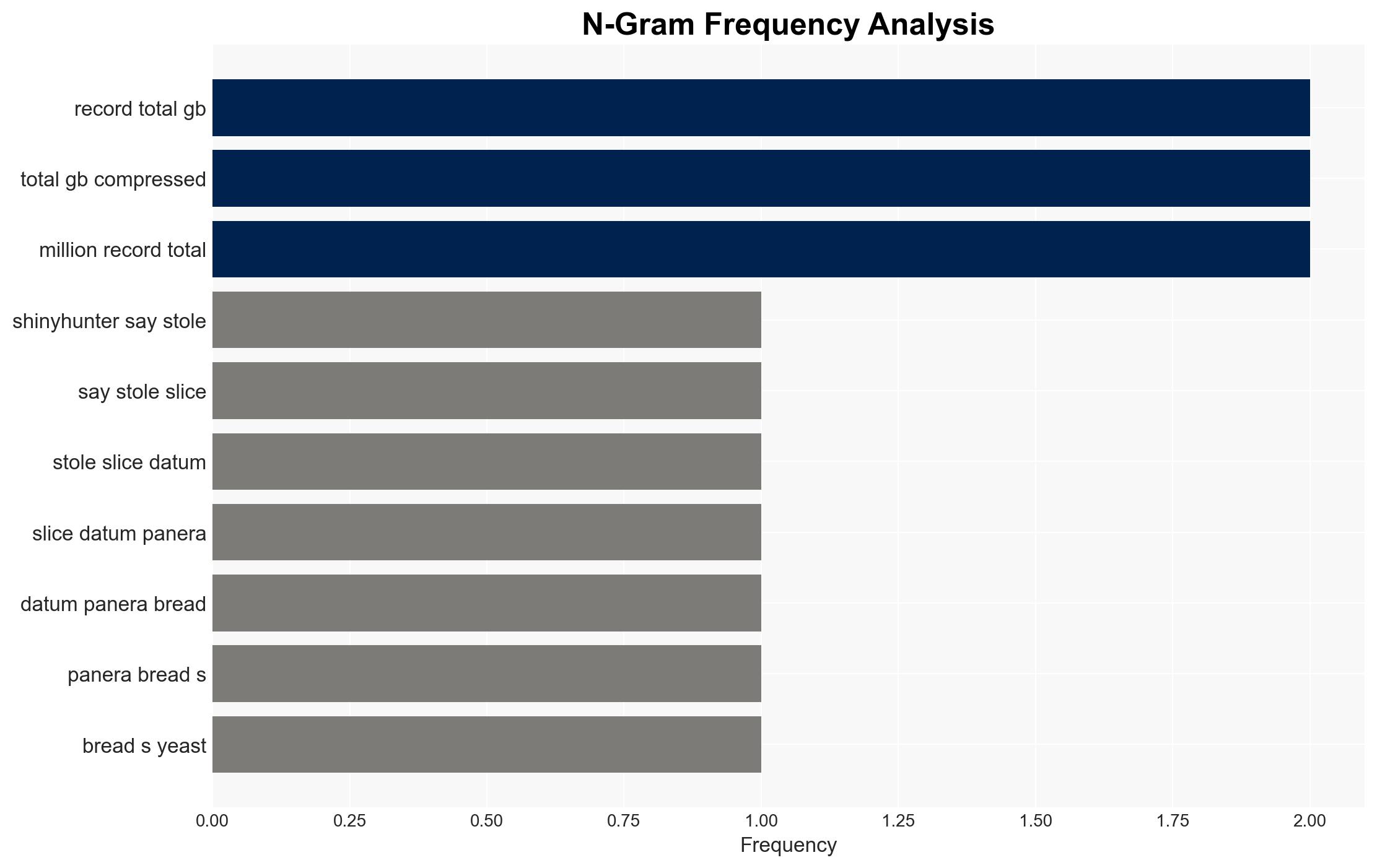
The ShinyHunters cybercriminal group claims to have stolen significant amounts of personally identifiable information (PII) from Panera Bread, CarMax, and Edmunds, among others. The breaches reportedly involve the exploitation of single-sign-on (SSO) systems through voice-phishing techniques. This development poses a moderate threat to the affected companies and their customers, with moderate confidence in the assessment due to the lack of immediate confirmation from the companies involved.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters successfully breached Panera Bread, CarMax, and Edmunds using SSO vulnerabilities and voice-phishing techniques. This is supported by the group’s claims and the method’s alignment with known tactics. However, the lack of confirmation from the companies introduces uncertainty.
- Hypothesis B: ShinyHunters is exaggerating or fabricating the breaches to enhance their reputation or for financial gain. The absence of responses from the affected companies and the potential for deception in cybercriminal claims support this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the detailed nature of the claims and the consistency with known attack vectors. Confirmation from the affected companies or further independent verification could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: ShinyHunters has the capability to execute sophisticated phishing attacks; the reported data breaches are genuine; the affected companies have not yet publicly acknowledged the breaches.
- Information Gaps: Confirmation from Panera Bread, CarMax, and Edmunds; specific details on how the breaches were executed; potential involvement of other threat actors.
- Bias & Deception Risks: Potential bias in relying on cybercriminals’ claims; risk of deception due to the lack of corroborating evidence from independent sources.
4. Implications and Strategic Risks
The alleged breaches, if confirmed, could have significant ramifications for the affected companies and their customers, potentially leading to increased regulatory scrutiny and reputational damage.
- Political / Geopolitical: Limited direct impact, but potential for increased regulatory actions on data protection.
- Security / Counter-Terrorism: Elevated threat environment for companies using SSO systems, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Potential for increased phishing and social engineering attacks targeting SSO vulnerabilities.
- Economic / Social: Possible financial losses for affected companies and erosion of consumer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage affected companies to confirm breaches and assess damage; enhance monitoring of SSO systems; alert customers to potential risks.
- Medium-Term Posture (1–12 months): Develop resilience measures against phishing attacks; strengthen partnerships with cybersecurity firms; invest in employee training on phishing awareness.
- Scenario Outlook: Best: Breaches are contained with minimal impact; Worst: Extensive data misuse and financial losses; Most-Likely: Moderate impact with increased security measures implemented.
6. Key Individuals and Entities
- ShinyHunters (cybercriminal group)
- Panera Bread (alleged victim)
- CarMax (alleged victim)
- Edmunds (alleged victim)
- Scattered Lapsus$ Hunters (associated group)
- Microsoft, Okta, Google (related to SSO vulnerabilities)
7. Thematic Tags
cybersecurity, data breach, phishing, single-sign-on, information security, cybercrime, personal data protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us