ShinyHunters claims to have leaked 600K Canada Goose customer records; company denies any breach occurred
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ShinyHunters leaked 600K Canada Goose customer records but the firm denies it was breached
1. BLUF (Bottom Line Up Front)
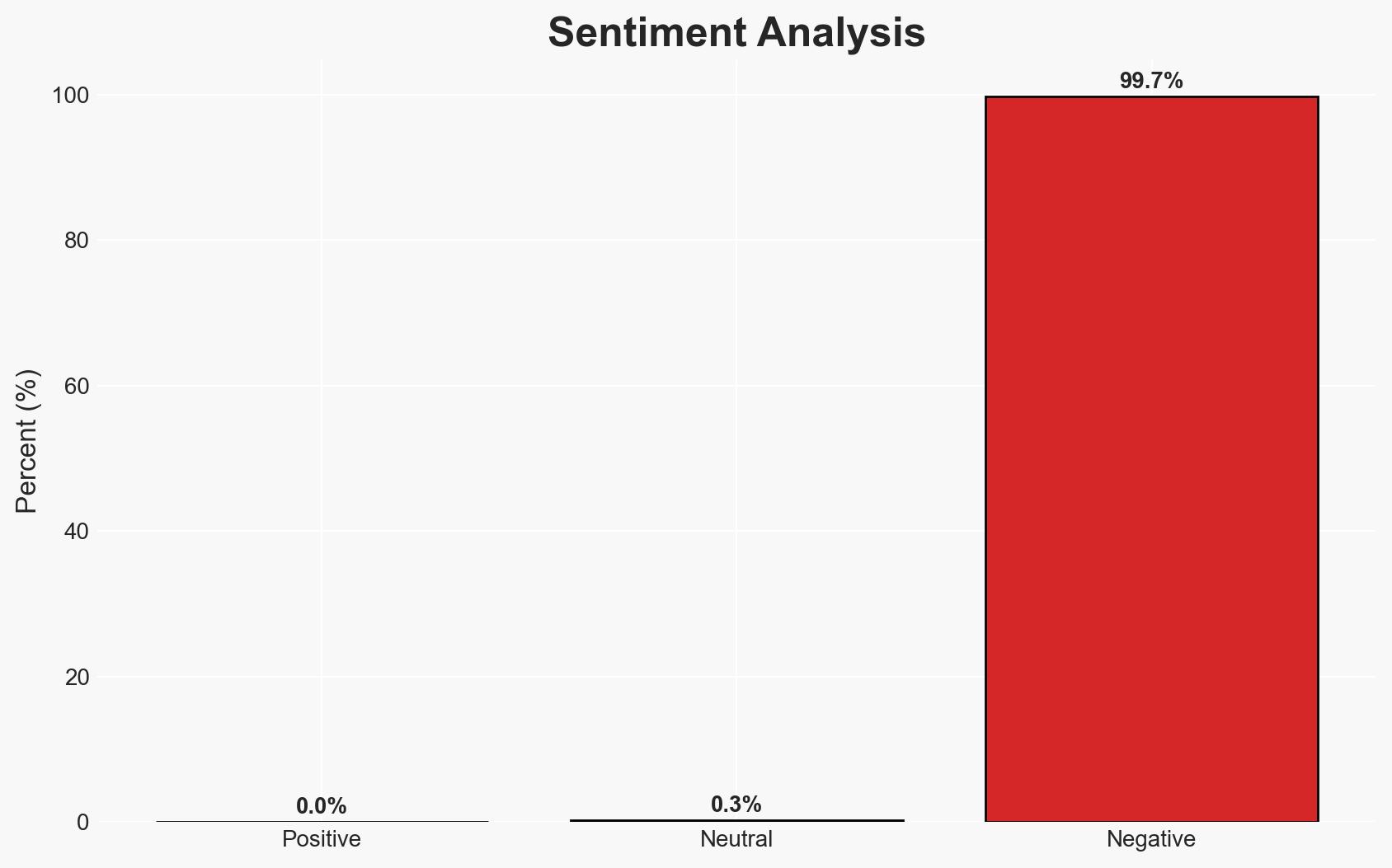
The ShinyHunters cybercrime group claims to have leaked over 600,000 Canada Goose customer records, but the company denies any breach of its systems. The most likely hypothesis is that the data originates from a third-party compromise rather than Canada Goose’s direct systems. This incident affects Canada Goose’s reputation and potentially its customers’ data security. Overall confidence in this assessment is moderate due to limited direct evidence of a breach.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters obtained the data through a breach of Canada Goose’s internal systems. Supporting evidence includes the volume and specificity of the data. Contradicting evidence is Canada Goose’s denial and lack of internal breach indicators. Key uncertainties include the source of the data.
- Hypothesis B: The data was obtained from a third-party source, possibly a partner or vendor. Supporting evidence includes the company’s statement and the nature of the data, which could be from past transactions. Contradicting evidence includes the public claim by ShinyHunters of a direct breach.
- Assessment: Hypothesis B is currently better supported given Canada Goose’s denial of a breach and the possibility of third-party data exposure. Indicators that could shift this judgment include new evidence of a direct breach or confirmation from third-party sources.
3. Key Assumptions and Red Flags
- Assumptions: Canada Goose’s internal systems are secure; ShinyHunters’ claims may be exaggerated; third-party data handling practices are less secure.
- Information Gaps: Specific source of the data leak; confirmation of third-party involvement; full scope and impact of the data exposure.
- Bias & Deception Risks: Potential bias in Canada Goose’s public statements to protect reputation; ShinyHunters may exaggerate claims to enhance credibility.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of Canada Goose’s data protection practices and potential regulatory actions. It may also embolden cybercriminal groups to target similar companies.
- Political / Geopolitical: Potential for increased regulatory focus on data protection standards in Canada.
- Security / Counter-Terrorism: Heightened awareness and preparedness against cyber extortion threats.
- Cyber / Information Space: Possible increase in cybercrime activity targeting luxury brands; reputational damage to Canada Goose.
- Economic / Social: Potential loss of consumer trust and financial impact on Canada Goose; broader implications for consumer data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation; engage with third-party vendors to assess data security; enhance monitoring of dark web for further leaks.
- Medium-Term Posture (1–12 months): Strengthen data protection policies; establish partnerships with cybersecurity firms; conduct regular security audits.
- Scenario Outlook: Best: No further data exposure and improved security posture. Worst: Confirmation of a direct breach leading to significant reputational and financial damage. Most-Likely: Identification of a third-party source with moderate impact on reputation.
6. Key Individuals and Entities
- ShinyHunters (cybercrime group)
- Canada Goose (luxury outerwear company)
- Figure Technology Solutions, Inc. (recently breached company)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, cybercrime, luxury brands, data protection, third-party risk, extortion
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us