ShinyHunters Release Data Breach of Millions from SoundCloud, Crunchbase, and Betterment After Extortion Fail…
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ShinyHunters Leak Alleged Data of Millions From SoundCloud Crunchbase and Betterment
1. BLUF (Bottom Line Up Front)
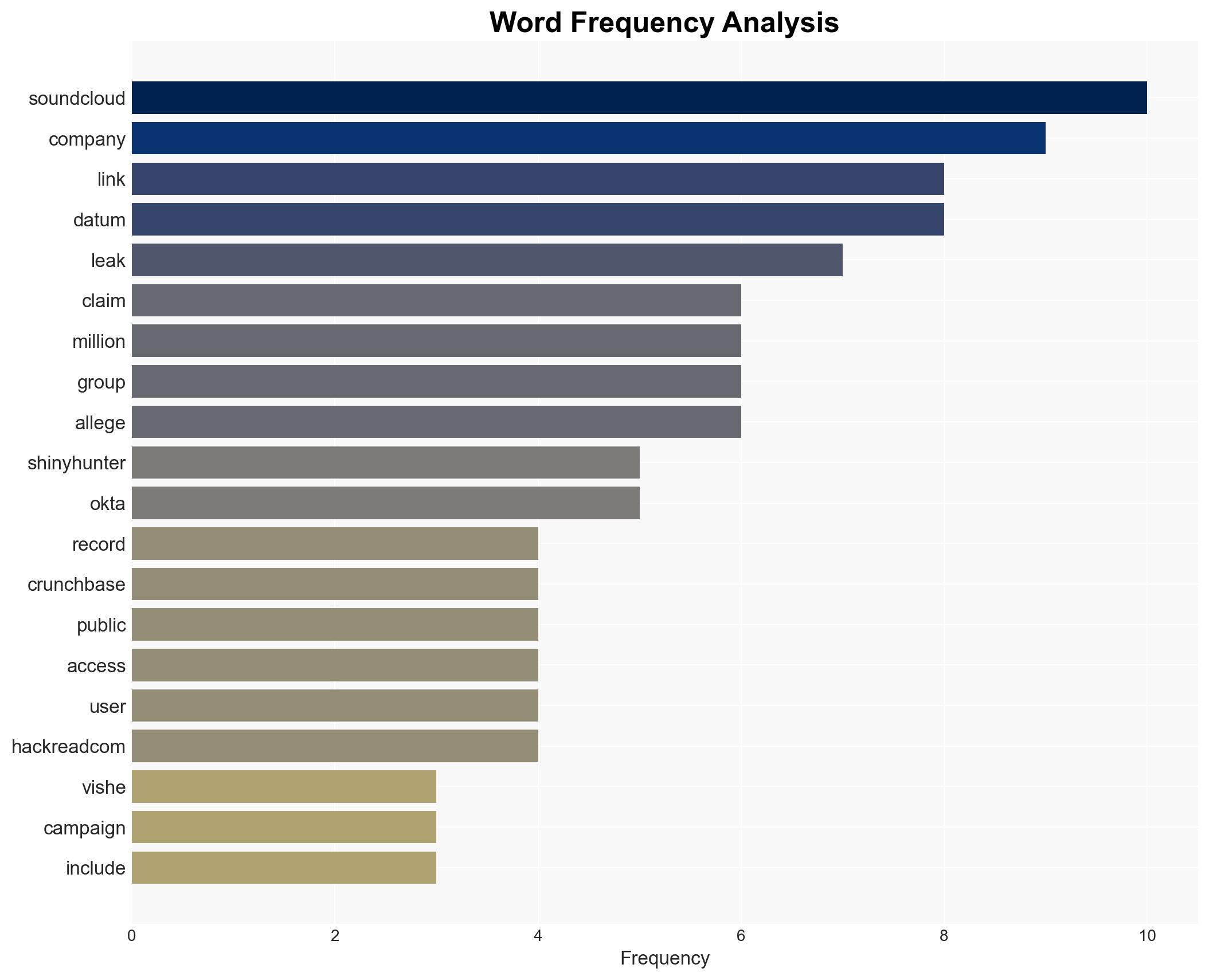
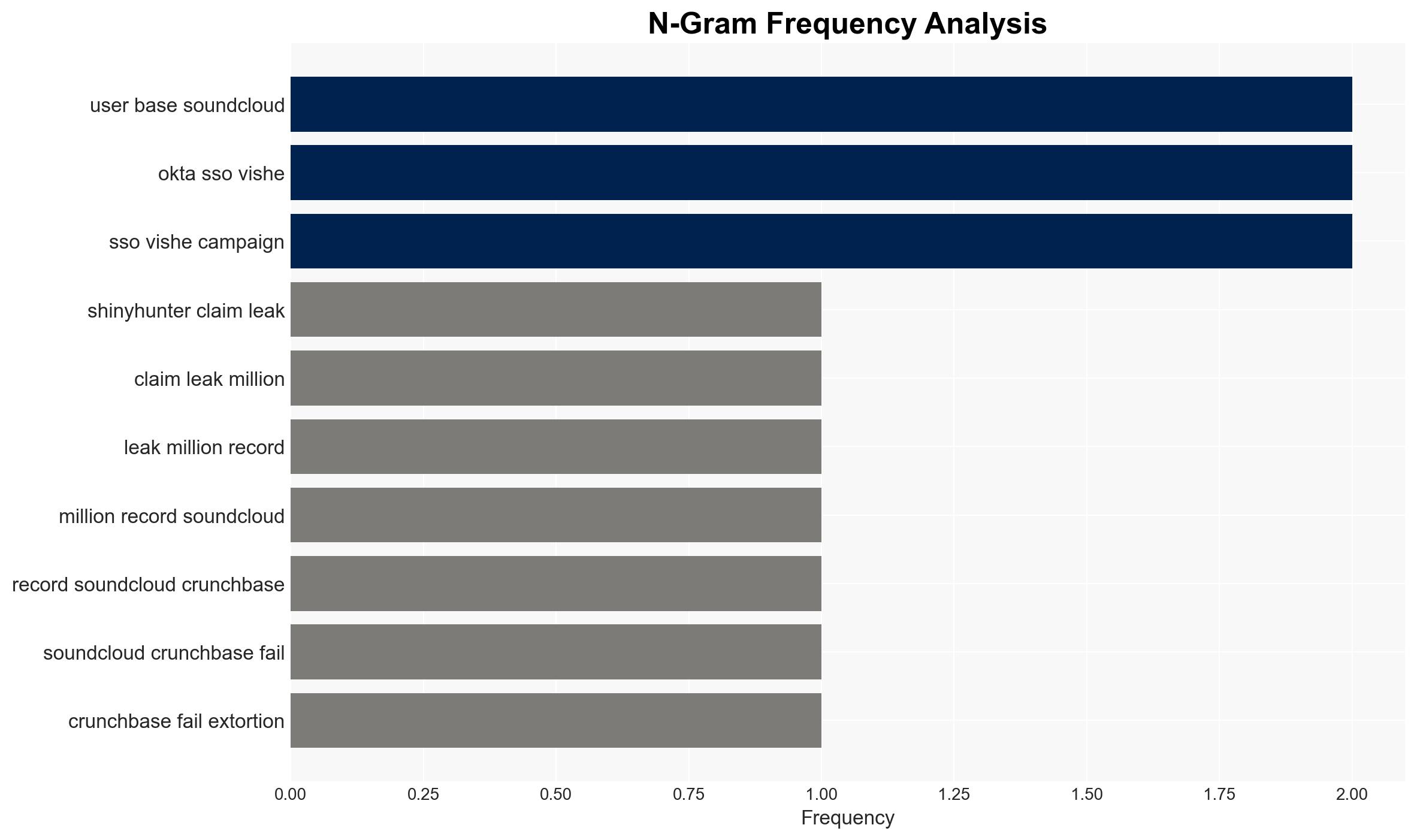
The ShinyHunters group claims responsibility for leaking millions of records from SoundCloud, Crunchbase, and Betterment following unsuccessful extortion attempts. This incident potentially links to an Okta vishing campaign, suggesting a coordinated cyber threat. The affected entities face significant data exposure risks. Overall, there is moderate confidence in the assessment due to existing information gaps and potential deception by ShinyHunters.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters successfully breached SoundCloud, Crunchbase, and Betterment independently, leveraging their own capabilities. Supporting evidence includes the group’s history of data breaches and the timing of the leaks. However, the exact method of breach remains uncertain, and the connection to the Okta vishing campaign is not fully substantiated.
- Hypothesis B: The breaches are interconnected through a broader campaign involving Okta’s compromised systems, with ShinyHunters exploiting these vulnerabilities. This is supported by the group’s claim of involvement in the Okta vishing campaign. Contradicting evidence includes the lack of direct confirmation from Okta or the affected companies.
- Assessment: Hypothesis A is currently better supported due to ShinyHunters’ established pattern of targeting companies for data breaches. However, further confirmation of the Okta link could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: ShinyHunters has the technical capability to execute these breaches independently; the data leaked is authentic; the Okta vishing campaign is related to the breaches.
- Information Gaps: Verification of the authenticity of the leaked data; confirmation of the link between the breaches and the Okta vishing campaign; detailed breach methodologies.
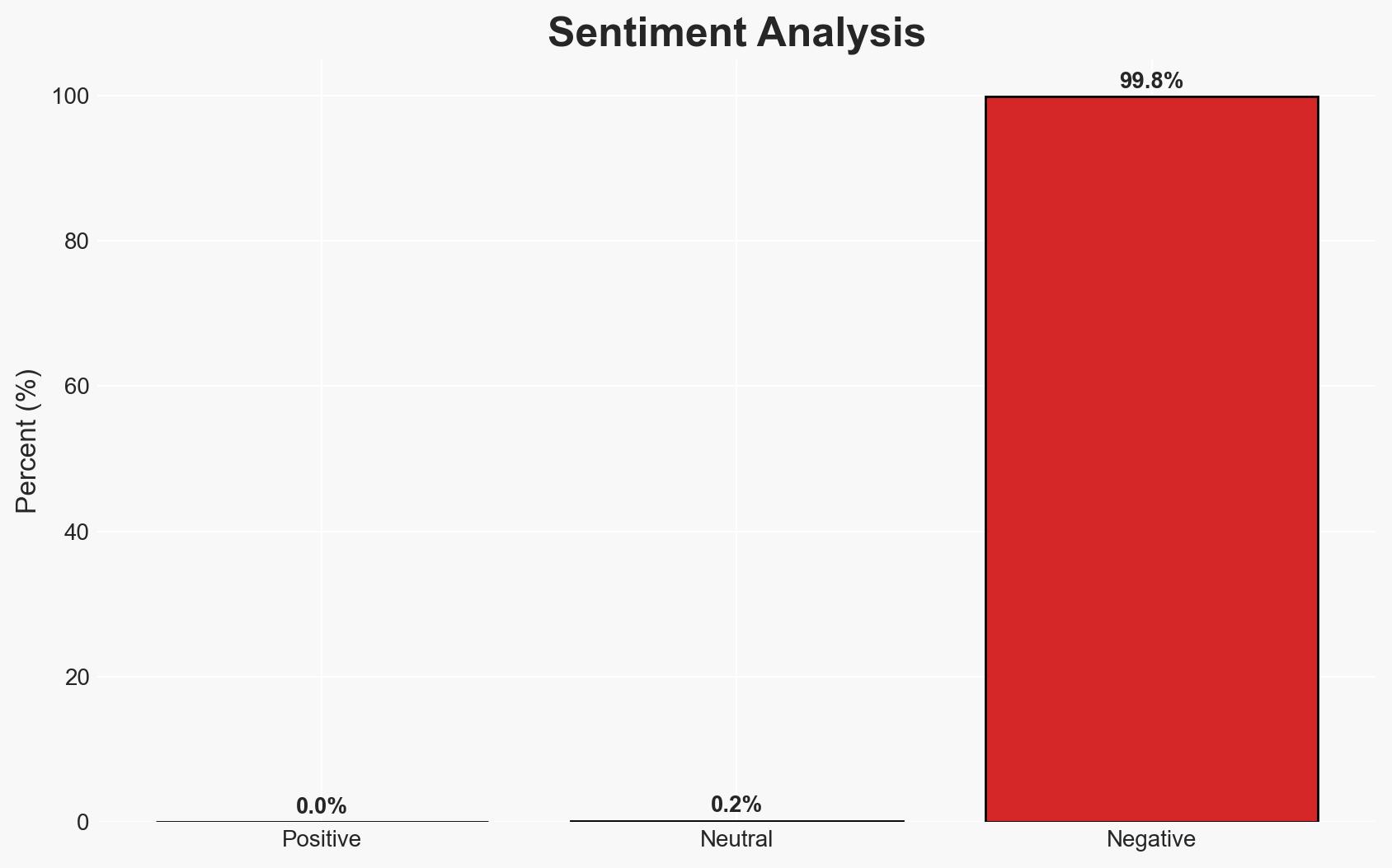
- Bias & Deception Risks: Potential exaggeration by ShinyHunters to amplify their perceived threat; reliance on ShinyHunters’ claims without independent verification may introduce bias.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of corporate cybersecurity practices and potential regulatory actions. The interconnected nature of cyber threats may prompt broader industry collaboration to mitigate risks.
- Political / Geopolitical: Escalation in cyber tensions could lead to diplomatic strains if state actors are suspected of involvement.
- Security / Counter-Terrorism: Increased risk of further cyber-attacks on other entities, potentially targeting critical infrastructure.
- Cyber / Information Space: Heightened awareness and potential for increased cyber defense measures across industries.
- Economic / Social: Potential financial losses for affected companies and erosion of consumer trust in digital platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough forensic investigations to confirm breach details; enhance monitoring of cyber threat intelligence; engage with affected companies for coordinated response.
- Medium-Term Posture (1–12 months): Develop resilience measures including enhanced cybersecurity protocols; foster industry partnerships for shared threat intelligence; invest in employee cybersecurity training.
- Scenario Outlook:
- Best: Breach impact is contained, leading to improved cybersecurity practices.
- Worst: Further breaches occur, causing widespread economic and reputational damage.
- Most-Likely: Incremental improvements in cybersecurity posture with ongoing threat of similar attacks.
6. Key Individuals and Entities
- ShinyHunters (hacker group)
- SoundCloud (audio streaming platform)
- Crunchbase (business data platform)
- Betterment (financial advisory company)
- Okta (Identity and Access Management service)
- Alon Gal (Hudson Rock cybersecurity firm)
7. Thematic Tags
cybersecurity, data breach, extortion, cybercrime, information security, corporate risk, digital threats
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us