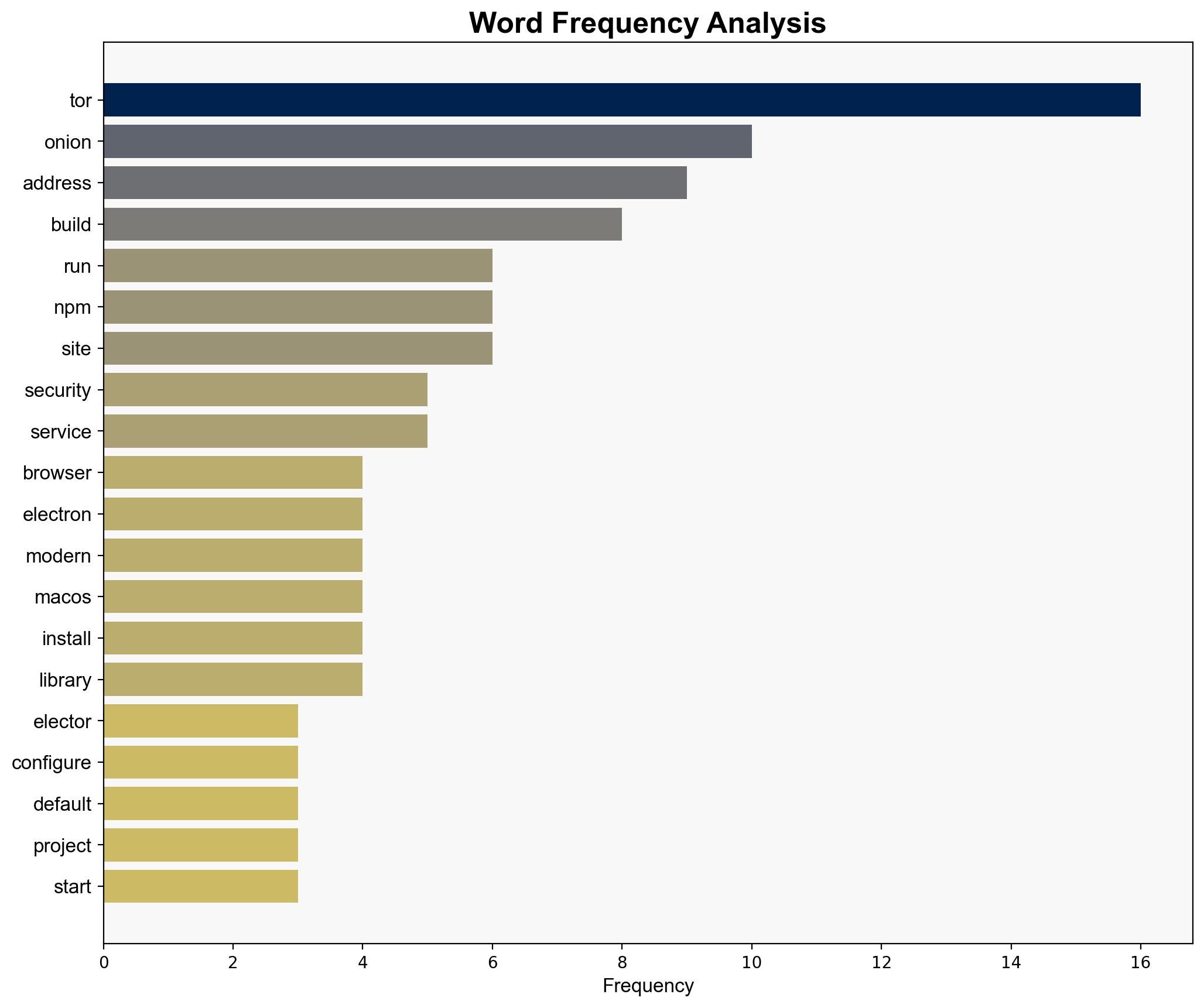
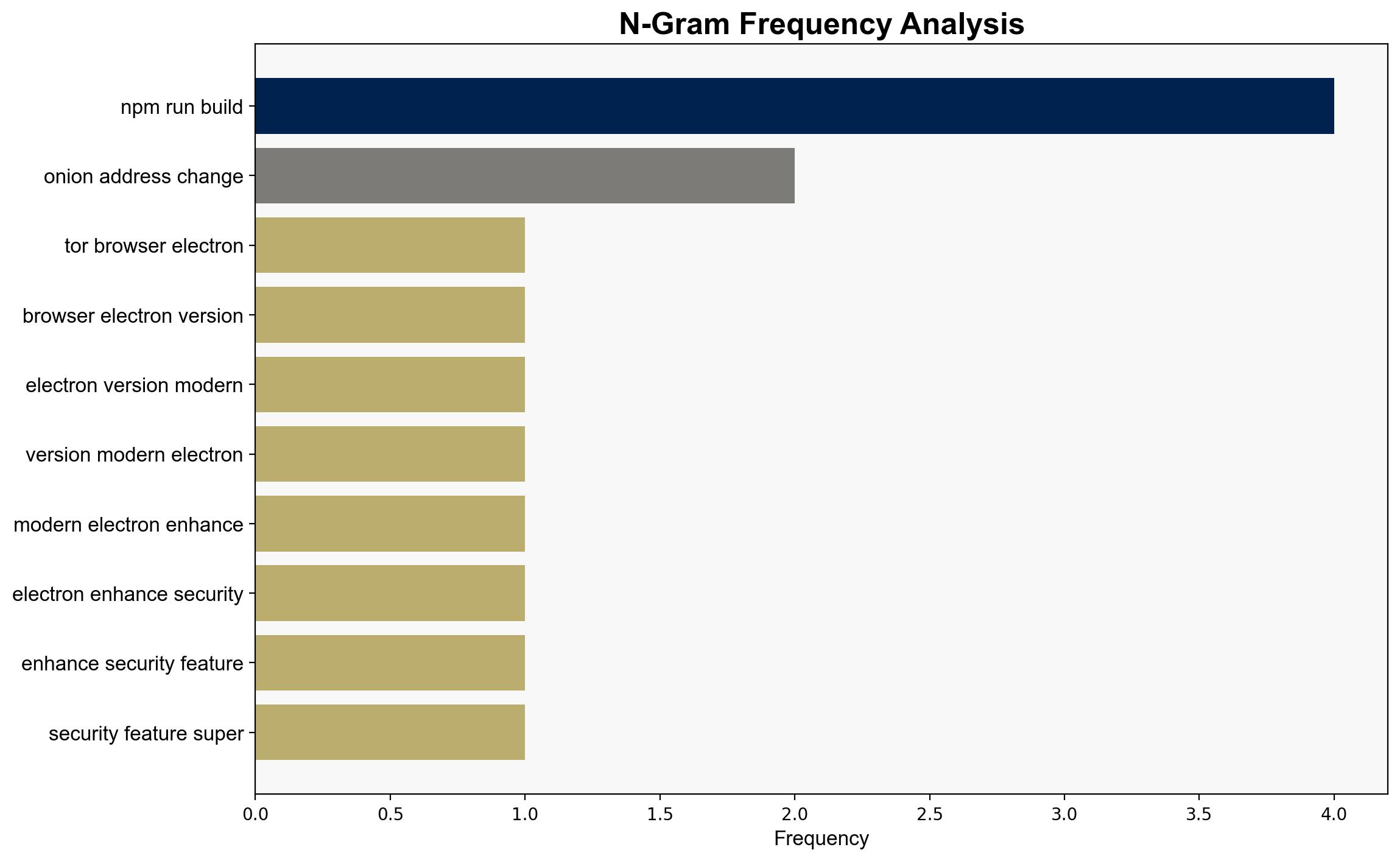
Show HN Elector A lightwight Tor browser in Electron – Github.com
Published on: 2025-10-04
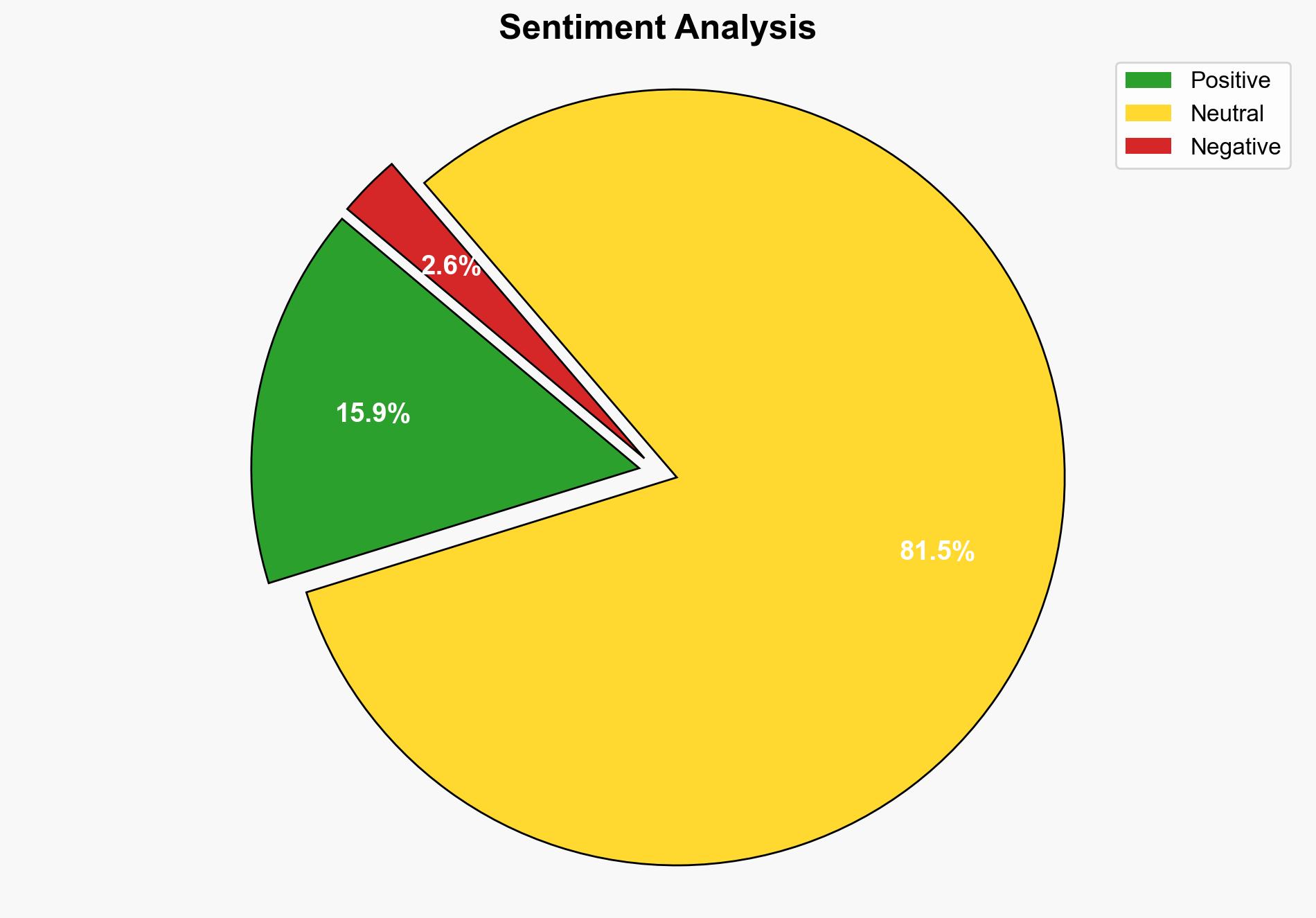
Intelligence Report: Show HN Elector A lightweight Tor browser in Electron – Github.com
1. BLUF (Bottom Line Up Front)
The development of Elector, a lightweight Tor browser using Electron, presents both opportunities and risks in cybersecurity. The most supported hypothesis is that Elector aims to enhance user privacy and security by leveraging modern web technologies. However, there is a moderate confidence level due to potential security vulnerabilities inherent in using Electron. It is recommended to closely monitor updates and community feedback to assess the browser’s security efficacy.
2. Competing Hypotheses
1. **Hypothesis A**: Elector is primarily designed to enhance user privacy and security by providing a lightweight, easy-to-use Tor browser that integrates modern security features.
2. **Hypothesis B**: Elector could inadvertently introduce security vulnerabilities due to its reliance on Electron, which may not be as secure as traditional Tor browser implementations.
Using ACH 2.0, Hypothesis A is better supported by the integration of modern security practices, such as sandboxing and context isolation. However, Hypothesis B remains plausible due to historical security concerns with Electron-based applications.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the developers have fully implemented the latest security patches and best practices in Electron. It is also assumed that users will configure the browser correctly to maximize security.
– **Red Flags**: The use of Electron, which has had security vulnerabilities in the past, could be a potential weak point. The lack of detailed security audits or third-party reviews is a concern.
– **Blind Spots**: The intelligence does not provide information on the developers’ background or their commitment to long-term maintenance and updates.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: If Elector has undiscovered vulnerabilities, it could be exploited by malicious actors, undermining user privacy.
– **Geopolitical Risks**: Increased use of Tor for anonymity could attract attention from governments seeking to control or monitor internet usage.
– **Economic Risks**: Potential misuse of Elector for illicit activities could lead to regulatory scrutiny and impact the broader tech ecosystem.
5. Recommendations and Outlook
- Encourage independent security audits of Elector to identify and mitigate potential vulnerabilities.
- Monitor user feedback and community discussions for emerging security concerns.
- Scenario Projections:
- **Best Case**: Elector becomes a trusted tool for secure browsing, enhancing user privacy without significant vulnerabilities.
- **Worst Case**: Security flaws lead to breaches, damaging user trust and leading to regulatory actions.
- **Most Likely**: Elector gains moderate adoption with ongoing scrutiny and updates to address security issues.
6. Key Individuals and Entities
No specific individuals are mentioned in the source material. The project is hosted on Github, indicating a collaborative development effort.
7. Thematic Tags
national security threats, cybersecurity, privacy, open-source software, internet anonymity