Signal clone used by federal agencies hit in attacks targeting major flaws – CISA says patch immediately – TechRadar
Published on: 2025-07-03
Intelligence Report: Signal Clone Used by Federal Agencies Hit in Attacks Targeting Major Flaws – CISA Says Patch Immediately – TechRadar
1. BLUF (Bottom Line Up Front)
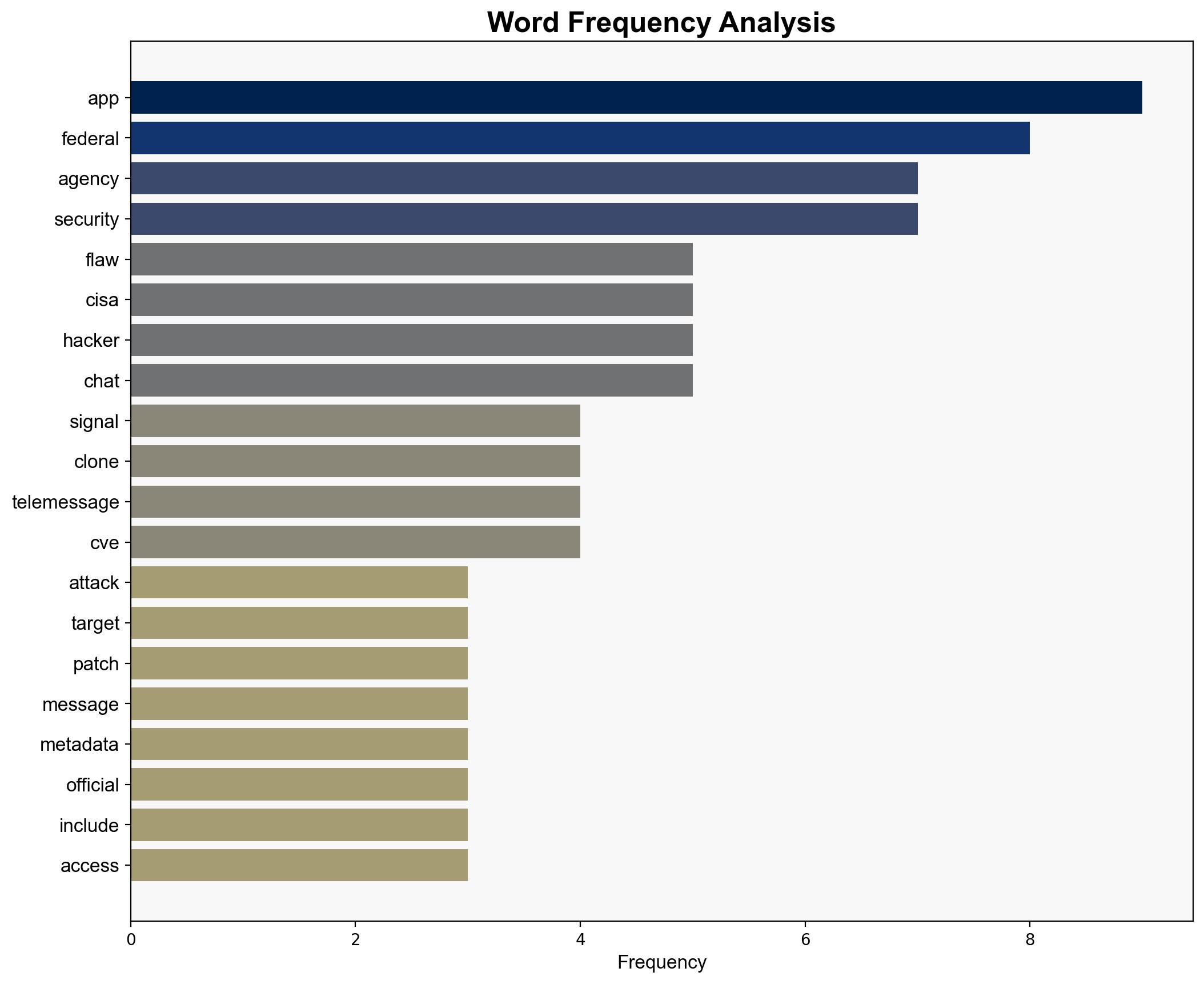
A Signal messaging app clone, used by federal agencies, has been compromised due to major security flaws. Hackers have exploited these vulnerabilities to access chat logs and metadata of government officials. The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent directive for federal agencies to apply patches by July. Immediate action is required to prevent further unauthorized access and data breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases in the assessment were identified and mitigated through structured challenges, ensuring a balanced analysis of the threat landscape.
Bayesian Scenario Modeling
Probabilistic forecasting was used to assess the likelihood of further exploitation of these vulnerabilities, indicating a high risk of continued attacks if patches are not applied promptly.
Network Influence Mapping
The influence of state and non-state actors involved in the exploitation of these vulnerabilities was mapped, highlighting potential geopolitical implications.
3. Implications and Strategic Risks
The breach exposes systemic vulnerabilities in federal communication systems, potentially undermining national security. The unauthorized access to sensitive government communications could lead to significant political and diplomatic fallout. Additionally, the exploitation of these flaws may embolden other threat actors to target similar vulnerabilities, increasing the risk of widespread cyberattacks.
4. Recommendations and Outlook
- Immediately apply the CISA-recommended patches to mitigate current vulnerabilities.
- Conduct a comprehensive security audit of all communication systems to identify and address potential weaknesses.
- Enhance training and awareness programs for government officials to prevent accidental data exposure.
- Scenario-based projections suggest that failure to act could lead to further breaches (worst case), while timely patching and audits could restore system integrity (best case).
5. Key Individuals and Entities
Mike Waltz, Jeffrey Goldberg
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus