‘Significant’ threat to US networks after hackers stole F5 source code CISA warns – TechRadar
Published on: 2025-10-16
Intelligence Report: ‘Significant’ threat to US networks after hackers stole F5 source code CISA warns – TechRadar
1. BLUF (Bottom Line Up Front)
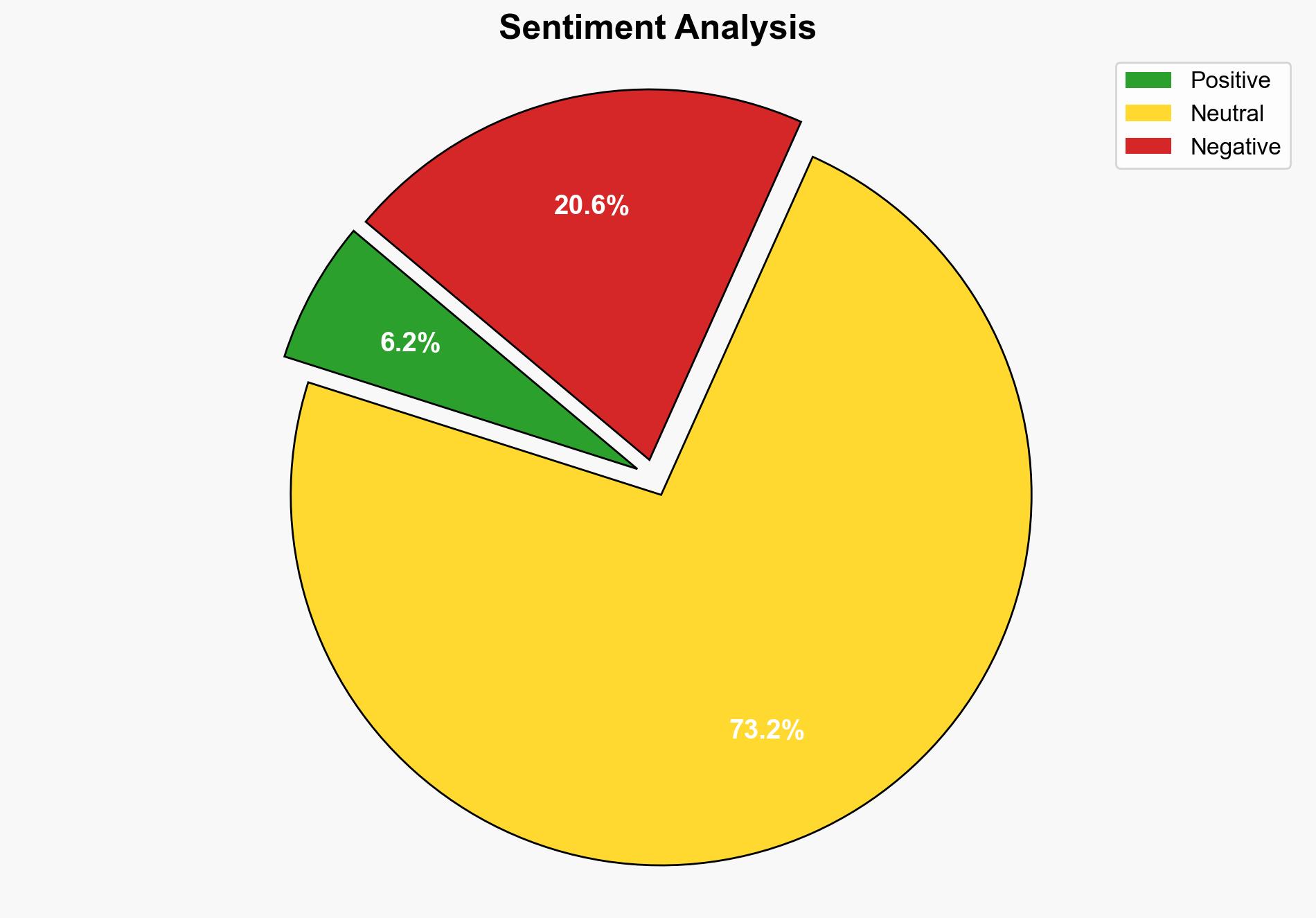
The theft of F5 source code represents a significant cybersecurity threat to US federal networks, with a high likelihood of exploitation by nation-state actors. The most supported hypothesis is that the breach will lead to the discovery and exploitation of zero-day vulnerabilities, necessitating immediate patching and network hardening. Confidence level: High. Recommended action: Urgent implementation of CISA directives and enhanced monitoring of network traffic.
2. Competing Hypotheses
1. **Hypothesis A**: The breach will lead to the discovery and exploitation of zero-day vulnerabilities in F5 products, resulting in significant security breaches across US federal networks.
2. **Hypothesis B**: The breach, while serious, will not result in immediate exploitation due to existing security measures and rapid patch deployment by affected agencies.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the history of nation-state actors exploiting similar vulnerabilities and the critical nature of the stolen source code.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that nation-state actors have the capability and intent to exploit the stolen source code. It is also assumed that the patches will be effective in mitigating the vulnerabilities.
– **Red Flags**: Lack of confirmation of the specific threat actor involved and the absence of evidence of exploitation in the wild are significant uncertainties.
– **Blind Spots**: Potential underestimation of the time required for adversaries to develop exploits from the stolen code.
4. Implications and Strategic Risks
The breach could lead to widespread exploitation of critical infrastructure, affecting national security and economic stability. The potential for cascading effects includes compromised data integrity, loss of public trust, and increased geopolitical tensions if a nation-state is confirmed as the perpetrator. The psychological impact on stakeholders and the public could also be significant, leading to increased demand for cybersecurity measures.
5. Recommendations and Outlook
- Immediate implementation of CISA’s emergency directives to patch and harden vulnerable systems.
- Enhance network monitoring to detect anomalous activities indicative of exploitation attempts.
- Develop contingency plans for potential data breaches and service disruptions.
- Scenario-based projections:
- Best Case: Rapid patch deployment prevents any significant exploitation (Low likelihood).
- Worst Case: Widespread exploitation leads to critical infrastructure failures (Moderate likelihood).
- Most Likely: Some exploitation occurs, but is contained through proactive measures (High likelihood).
6. Key Individuals and Entities
– F5 Networks (affected company)
– Cybersecurity and Infrastructure Security Agency (CISA)
– Nation-state actors (unidentified)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus