Silver Fox Exploits Signed Drivers to Deploy ValleyRAT Backdoor – Infosecurity Magazine
Published on: 2025-09-01
Intelligence Report: Silver Fox Exploits Signed Drivers to Deploy ValleyRAT Backdoor – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
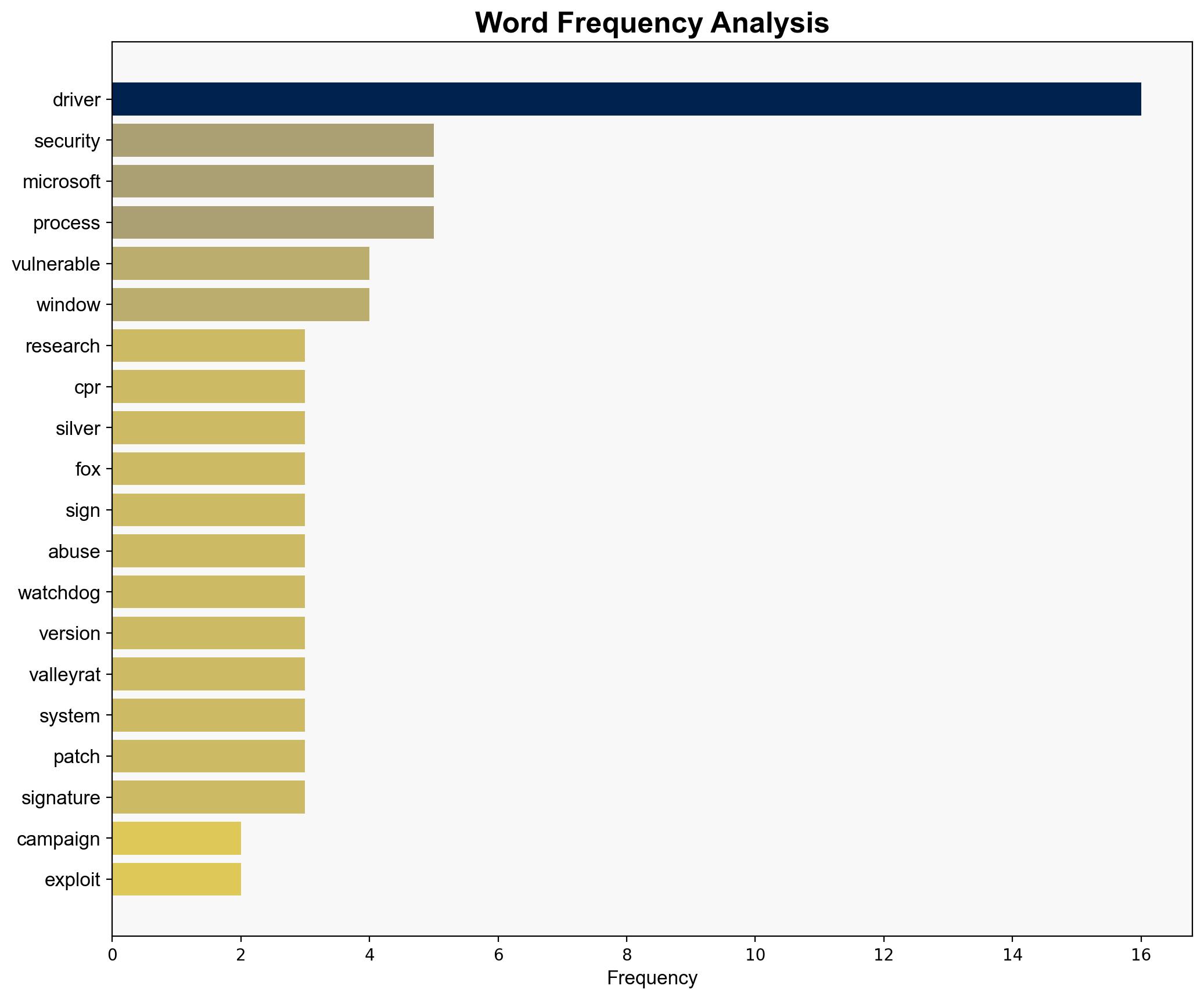
The Silver Fox APT group is exploiting vulnerabilities in signed Windows drivers to deploy the ValleyRAT backdoor, posing significant risks to cybersecurity. The most supported hypothesis is that Silver Fox is leveraging these vulnerabilities to target entities in East Asia, potentially for espionage purposes. Confidence in this assessment is moderate due to the evolving nature of the campaign and limited attribution data. Immediate action is recommended to strengthen driver security protocols and enhance monitoring for abnormal driver activities.
2. Competing Hypotheses
1. **Hypothesis A**: Silver Fox is primarily targeting East Asian entities for espionage, using the ValleyRAT backdoor to gather intelligence.
– **Supporting Evidence**: The malware configurations specifically target security products popular in East Asia, and the infrastructure traces back to servers in China.
2. **Hypothesis B**: Silver Fox is conducting a broader campaign aimed at global disruption, using ValleyRAT to disable security systems and deploy further attacks.
– **Supporting Evidence**: The campaign involves exploiting widely trusted Microsoft-signed drivers, suggesting a potential for broader application beyond East Asia.
Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported due to the specific targeting of East Asian security products and infrastructure links to China. However, the potential for broader application remains a concern.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the targeting of East Asian security products indicates a regional focus. The infrastructure’s link to China is presumed to be intentional and not a false flag.
– **Red Flags**: The rapid evolution of the campaign and the use of legitimate drivers suggest potential deception or misdirection. The reliance on previously vulnerable drivers could indicate overlooked security patches or updates.
– **Blind Spots**: Limited information on the full scope of Silver Fox’s capabilities and intentions. Potential underestimation of the group’s ability to adapt and expand its operations globally.
4. Implications and Strategic Risks
The exploitation of signed drivers by Silver Fox could lead to increased vulnerabilities in Windows systems globally, especially if similar techniques are adopted by other threat actors. The focus on East Asia suggests geopolitical motivations, potentially escalating tensions in the region. Economically, compromised systems could lead to significant financial losses and disrupt critical infrastructure.
5. Recommendations and Outlook
- Implement Microsoft’s latest driver blocklist and enhance YARA detection rules to mitigate risks.
- Increase monitoring for abnormal driver activities and ensure timely patching of known vulnerabilities.
- Scenario Projections:
- **Best Case**: Enhanced security measures prevent further exploitation, and Silver Fox’s activities are curtailed.
- **Worst Case**: Silver Fox expands its campaign globally, leading to widespread system compromises and geopolitical tensions.
- **Most Likely**: Continued targeting of East Asia with potential for gradual expansion if vulnerabilities remain unaddressed.
6. Key Individuals and Entities
No specific individuals are identified in the intelligence. The Silver Fox APT group and Microsoft are the primary entities involved.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus