Somalia’s e-visa platform exposed to security vulnerabilities, risking sensitive personal data of thousands
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New Somalia e-visa security flaw puts personal data of thousands at risk
1. BLUF (Bottom Line Up Front)
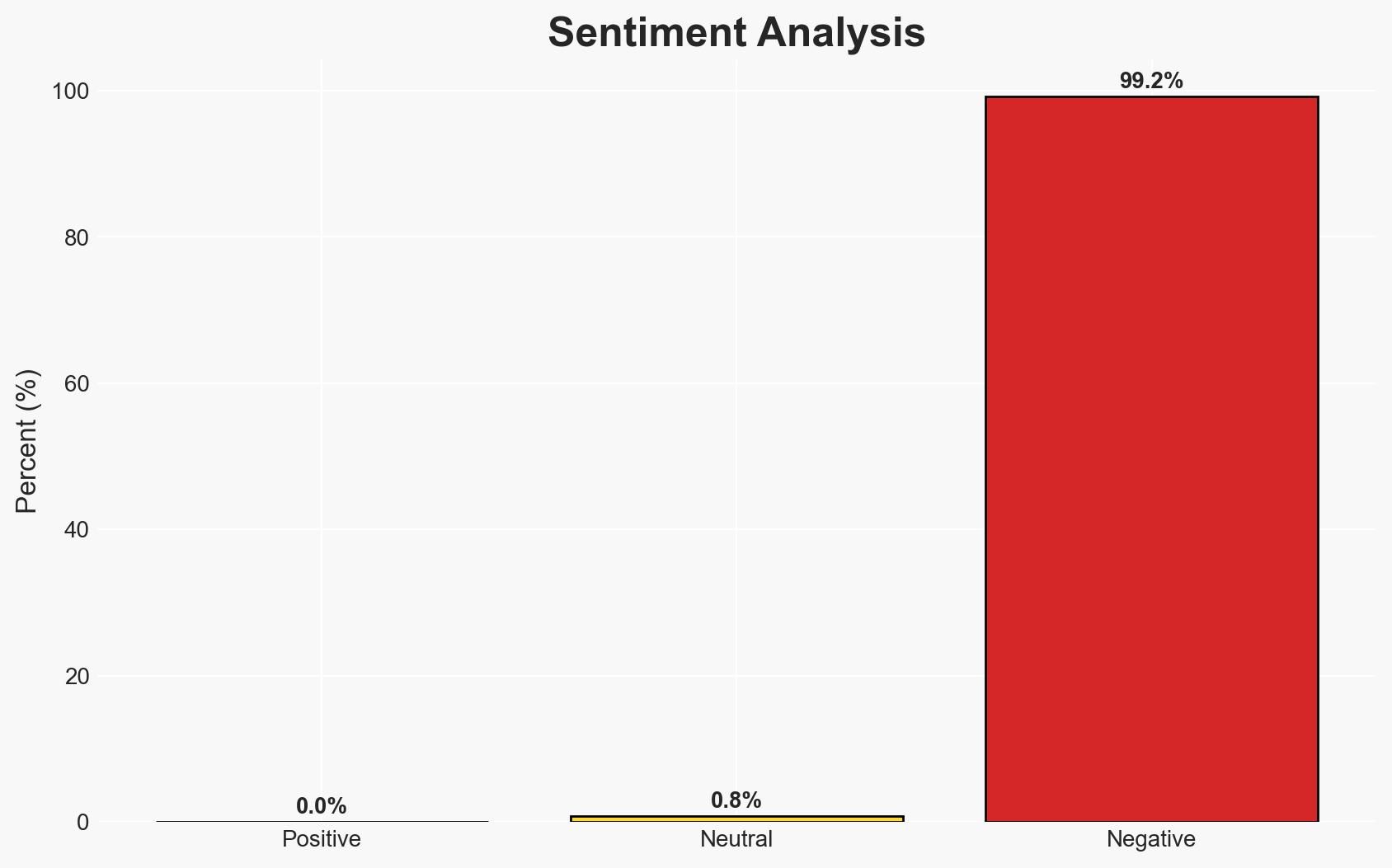
The Somalia e-visa system has a significant security vulnerability that exposes personal data of thousands, posing risks of identity theft and intelligence gathering. The Somali government’s lack of response exacerbates the threat. This issue affects individuals from multiple countries, increasing geopolitical complexity. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The security flaw is due to inadequate cybersecurity measures and oversight by Somali authorities. Evidence includes the recent breach and lack of government response. Uncertainties involve the extent of technical deficiencies and internal government priorities.
- Hypothesis B: The vulnerability is a result of intentional sabotage or insider threat, possibly by actors seeking to exploit the system for intelligence or financial gain. Supporting evidence is limited; contradictions include the lack of direct indicators of sabotage.
- Assessment: Hypothesis A is currently better supported due to the systemic nature of the flaws and historical context of inadequate cybersecurity practices. Indicators such as insider access logs or whistleblower testimony could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The Somali government lacks adequate cybersecurity resources; the vulnerability is not yet exploited by major threat actors; international cooperation on data protection is limited.
- Information Gaps: Detailed technical analysis of the vulnerability; Somali government’s internal communications and response plans; extent of data already compromised.
- Bias & Deception Risks: Potential bias from sources with vested interests in highlighting government failures; risk of deception by actors exaggerating the threat for political gain.
4. Implications and Strategic Risks
This development could undermine trust in Somalia’s digital infrastructure, affecting international relations and investment. If unaddressed, it may lead to increased cyber threats and exploitation by malicious actors.
- Political / Geopolitical: Strained diplomatic relations with affected countries; pressure on Somalia to improve cybersecurity.
- Security / Counter-Terrorism: Potential exploitation by terrorist groups for intelligence gathering or financial fraud.
- Cyber / Information Space: Increased cyber threat activity targeting Somali digital systems; potential for misinformation campaigns.
- Economic / Social: Reduced foreign investment and tourism; public distrust in government digital initiatives.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of the e-visa system; engage international cybersecurity experts; issue public advisories to affected individuals.
- Medium-Term Posture (1–12 months): Develop a national cybersecurity strategy; establish partnerships with international cybersecurity organizations; enhance data protection laws.
- Scenario Outlook: Best: Vulnerability is quickly patched, restoring trust. Worst: Major data breach exploited by threat actors, leading to international fallout. Most-Likely: Gradual improvements with ongoing risks of minor breaches.
6. Key Individuals and Entities
- Somali government (data controller)
- Al Jazeera (reporting entity)
- Bridget Andere, Access Now (commentator)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data protection, international relations, identity theft, digital infrastructure, Somalia, e-visa system
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us