South Korea attributes Coupang data breach to management issues rather than advanced cyberattack techniques
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: South Korea blames Coupang data breach on management failure not sophisticated attack
1. BLUF (Bottom Line Up Front)
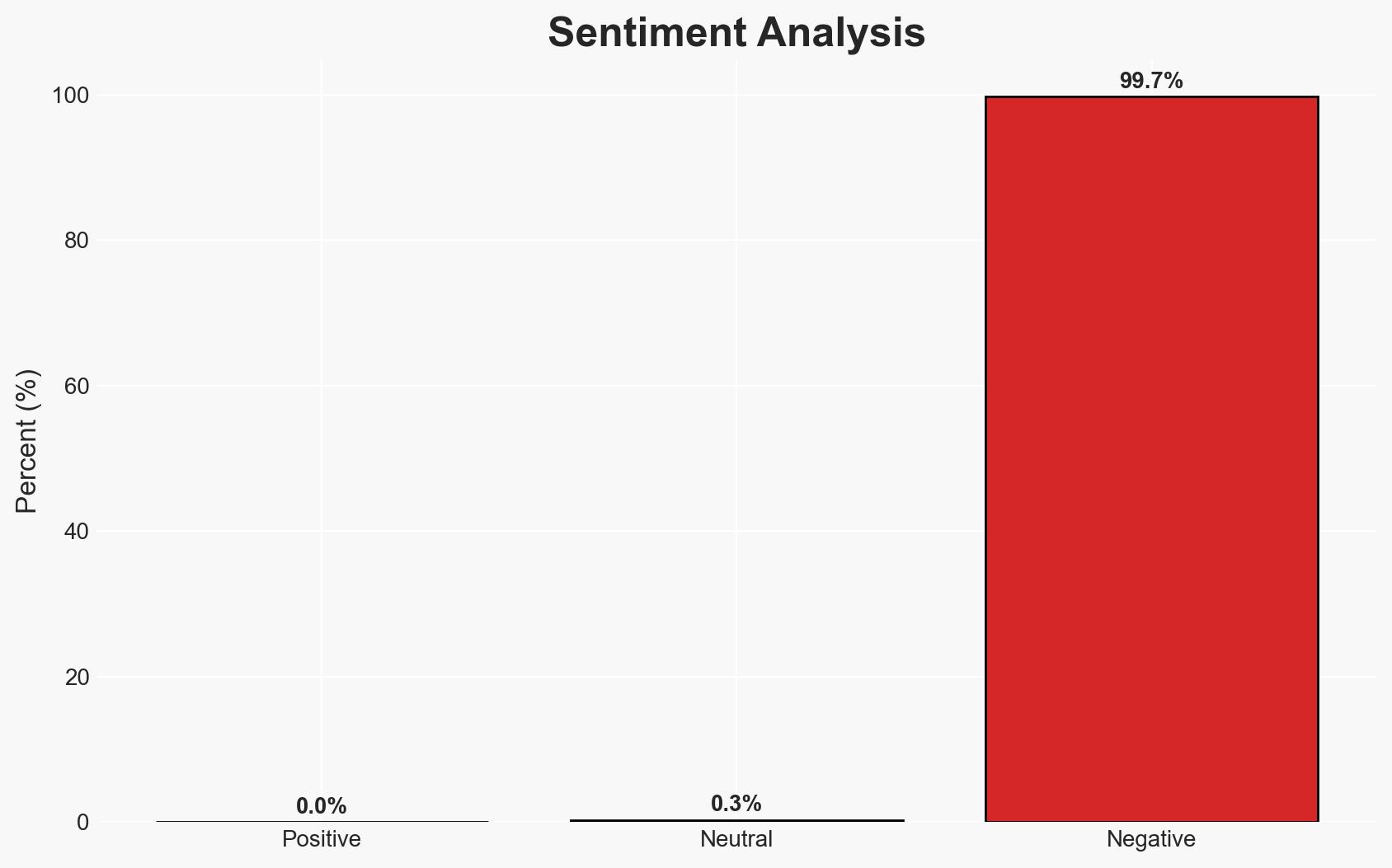
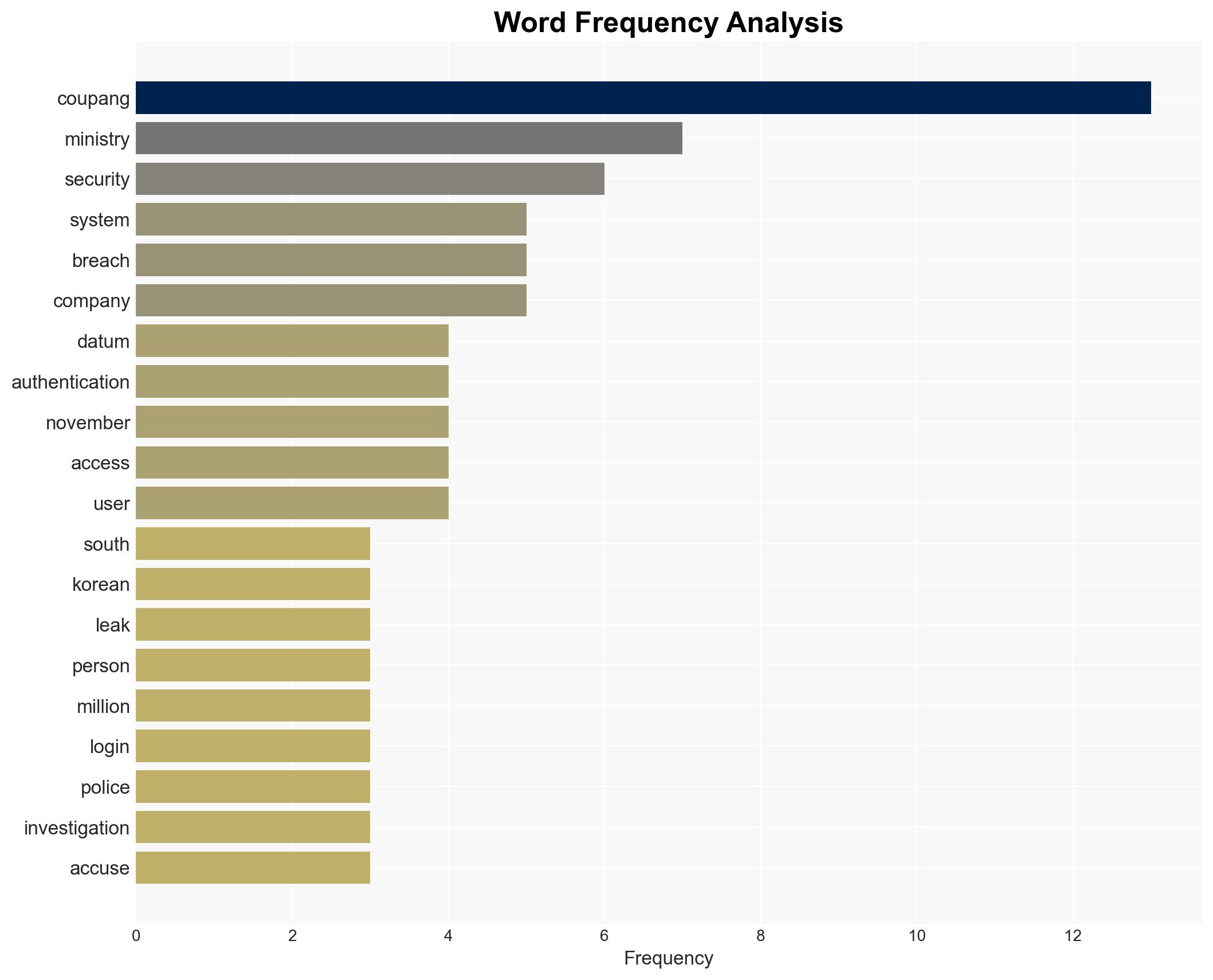
The South Korean government attributes the Coupang data breach to management failures rather than a sophisticated cyberattack, implicating internal security lapses. This incident affects Coupang’s operational integrity and its international relations, particularly with the U.S. We assess with moderate confidence that internal security oversight failures are the primary cause, though further investigation may reveal additional factors.
2. Competing Hypotheses
- Hypothesis A: The data breach resulted from internal management failures, specifically inadequate oversight of authentication systems and failure to revoke access keys. This is supported by the government’s findings and the involvement of a former employee with insider knowledge. However, uncertainties remain about the full extent of internal complicity.
- Hypothesis B: The breach was a sophisticated cyberattack disguised as a management failure, potentially involving external actors. This hypothesis is less supported due to the lack of evidence pointing to advanced external intrusion techniques.
- Assessment: Hypothesis A is currently better supported due to the detailed findings of the South Korean government and the specific identification of internal security lapses. Indicators that could shift this judgment include new evidence of external involvement or advanced intrusion methods.
3. Key Assumptions and Red Flags
- Assumptions: The breach was primarily due to internal failures; the former employee acted independently; no payment or login data was compromised.
- Information Gaps: The full scope of the breach and potential involvement of other insiders or external actors remain unclear.
- Bias & Deception Risks: Potential bias in South Korean authorities’ portrayal of the incident due to geopolitical tensions; possible deception by Coupang in data handling and breach reporting.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on data security practices in South Korea and affect international business relations.
- Political / Geopolitical: Potential strain on South Korea-U.S. trade relations due to perceived regulatory overreach.
- Security / Counter-Terrorism: Heightened awareness and potential policy changes in cybersecurity practices.
- Cyber / Information Space: Increased focus on internal security measures and potential regulatory changes in data protection.
- Economic / Social: Possible impact on consumer trust in Coupang and other e-commerce platforms, affecting market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough internal audits of authentication systems, enhance monitoring of insider threats, and engage with South Korean authorities for compliance.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to strengthen defenses, implement advanced threat detection systems, and improve employee training on data security.
- Scenario Outlook:
- Best: Improved security measures restore consumer trust and stabilize international relations.
- Worst: Further breaches occur, leading to significant financial and reputational damage.
- Most-Likely: Gradual improvement in security practices with ongoing regulatory scrutiny.
6. Key Individuals and Entities
- Choi Woo-hyuk, Deputy Minister for Cyber Security and Network Policy
- Coupang Inc
- South Korean Science Ministry
- Not clearly identifiable from open sources in this snippet: Former Coupang employee involved in the breach
7. Thematic Tags
cybersecurity, data breach, insider threat, e-commerce, South Korea, U.S.-Korea relations, regulatory compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us