South Korean crypto operator sentenced to four years for facilitating Bitcoin trade linked to North Korean es…
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: South Korean crypto employee gets 4-year sentence for Bitcoin spy ring aiding North Korea
1. BLUF (Bottom Line Up Front)
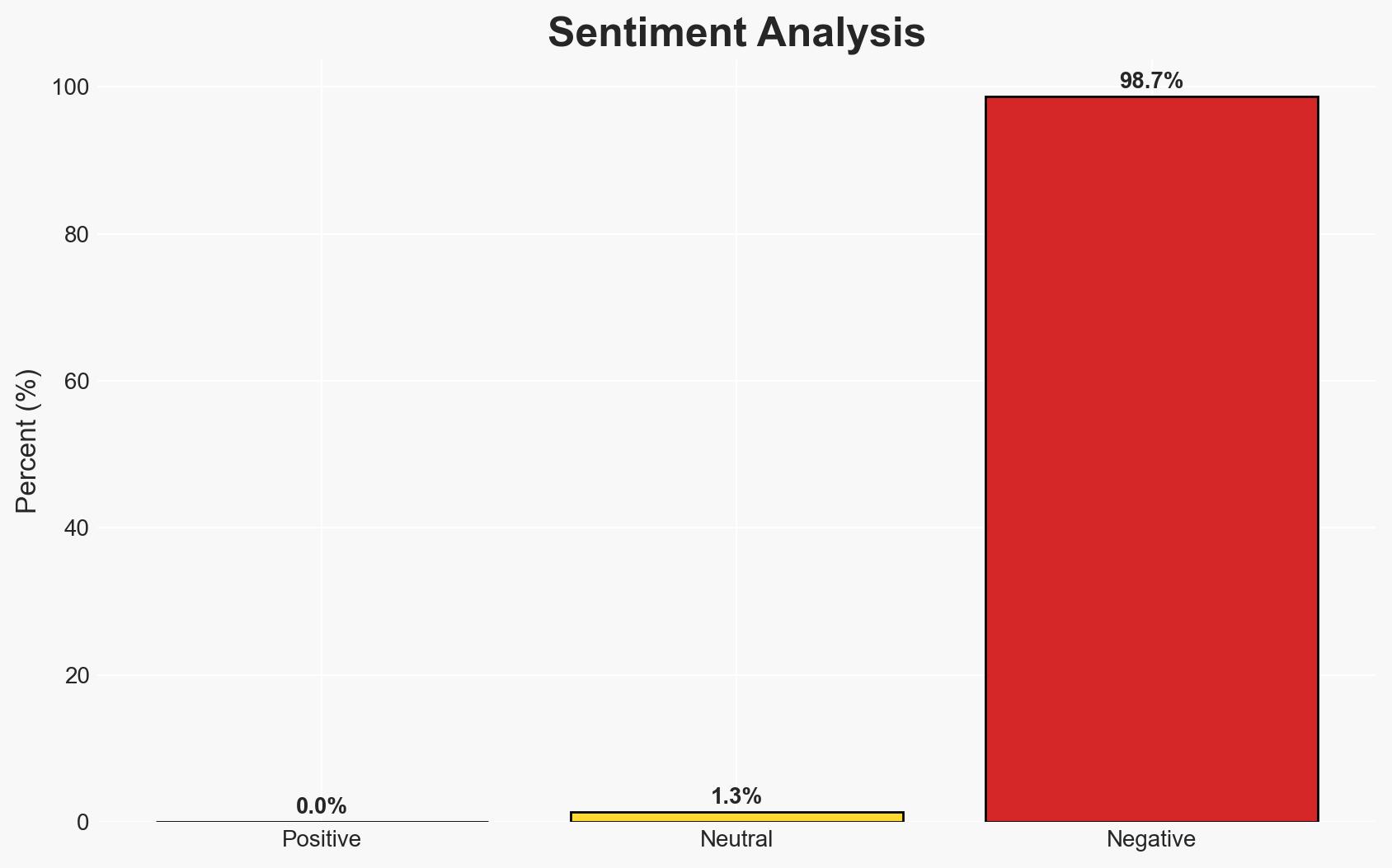
The sentencing of a South Korean crypto exchange operator for espionage activities highlights the exploitation of digital currencies by North Korea to fund its military programs. This case underscores the vulnerability of digital assets to state-sponsored cyber operations. The most likely hypothesis is that North Korea is systematically using cryptocurrency to bypass international sanctions. Overall confidence in this assessment is moderate due to limited visibility into North Korean operations.
2. Competing Hypotheses
- Hypothesis A: North Korea is actively recruiting individuals in foreign countries to exploit cryptocurrency for espionage and funding its weapons programs. Supporting evidence includes the recruitment of a South Korean army captain and previous reports of North Korean cyber thefts. Key uncertainties involve the full extent of North Korea’s network and operations.
- Hypothesis B: The incident is an isolated case of opportunistic crime by individuals seeking financial gain, with limited direct involvement from North Korean state actors. Contradicting evidence includes the structured nature of the operation and previous patterns of North Korean cyber activities.
- Assessment: Hypothesis A is currently better supported due to the structured and strategic nature of the operation, consistent with known North Korean tactics. Indicators such as increased cyber activity targeting cryptocurrency exchanges could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: North Korea continues to prioritize cyber operations for economic gain; digital currencies remain a viable tool for sanctions evasion; South Korean military systems are a high-value target for North Korean intelligence.
- Information Gaps: Detailed understanding of North Korea’s cyber capabilities and network; the extent of cryptocurrency use in North Korean operations; potential involvement of other state actors.
- Bias & Deception Risks: Potential confirmation bias due to historical North Korean cyber activities; source bias from reliance on court documents and official statements; possible deception by North Korean operatives to mislead investigations.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and regulation of cryptocurrency exchanges globally, impacting their operations and market stability. It may also prompt enhanced cybersecurity measures in military and financial sectors.
- Political / Geopolitical: Potential escalation in tensions between North and South Korea and increased diplomatic pressure on North Korea.
- Security / Counter-Terrorism: Heightened threat environment with increased focus on protecting military and critical infrastructure from cyber threats.
- Cyber / Information Space: Potential for increased cyber operations targeting cryptocurrency exchanges and financial institutions.
- Economic / Social: Possible destabilization of cryptocurrency markets and increased public concern over digital asset security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of cryptocurrency transactions linked to North Korea; enhance cybersecurity protocols in military and financial sectors; engage with international partners to share intelligence.
- Medium-Term Posture (1–12 months): Develop resilience measures for cryptocurrency exchanges; strengthen international partnerships to counter cyber threats; invest in capability development for cyber defense.
- Scenario Outlook:
- Best: Successful international collaboration leads to significant disruption of North Korean cyber operations.
- Worst: Escalation of cyber attacks on critical infrastructure, leading to significant economic and security impacts.
- Most-Likely: Continued low-level cyber operations by North Korea with periodic disruptions and increased international regulatory measures.
6. Key Individuals and Entities
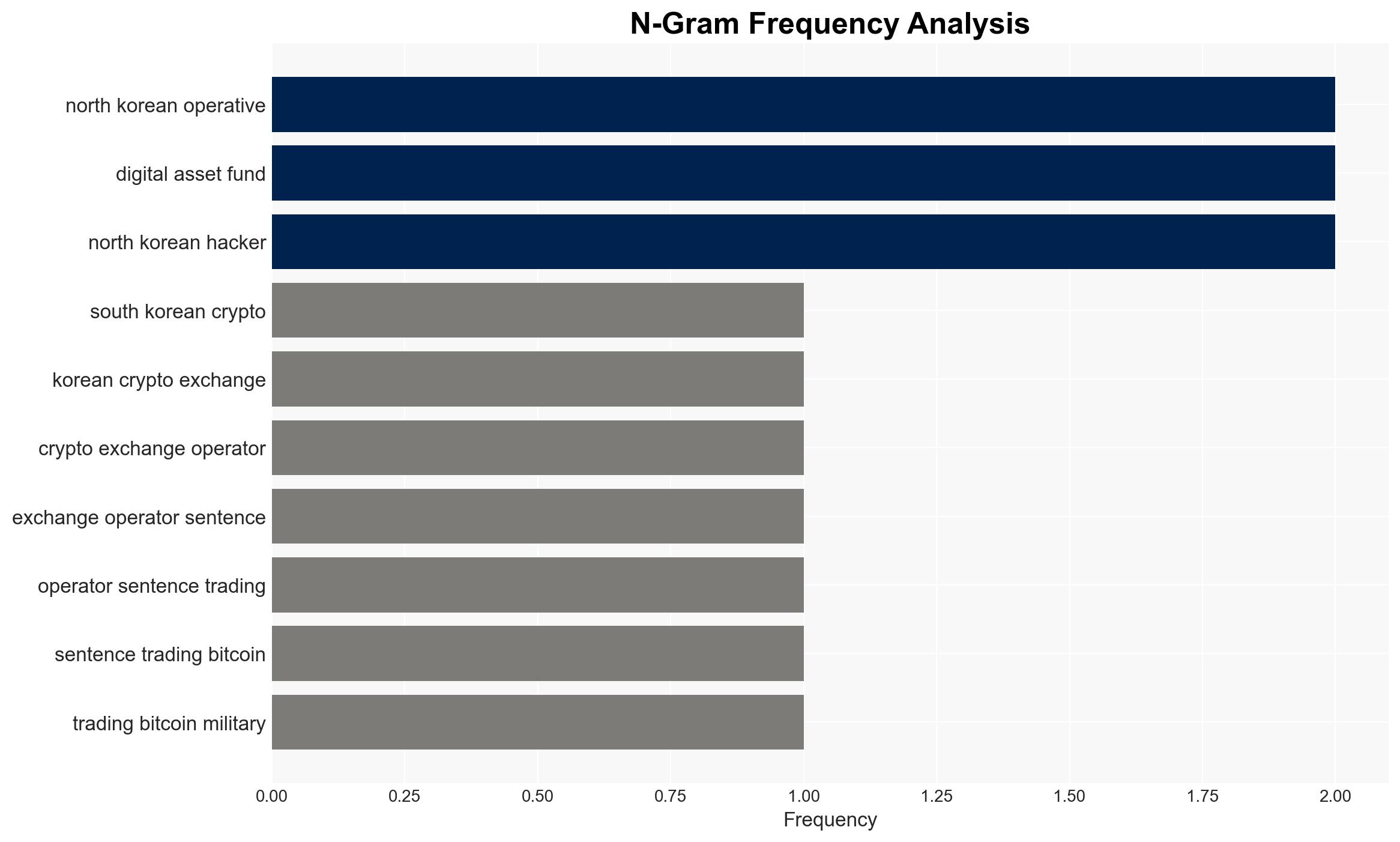
- Lee (South Korean crypto exchange operator)
- Captain Kim (South Korean army captain)
- Boris (North Korean operative)
- U.S. Treasury Department
- FBI
7. Thematic Tags
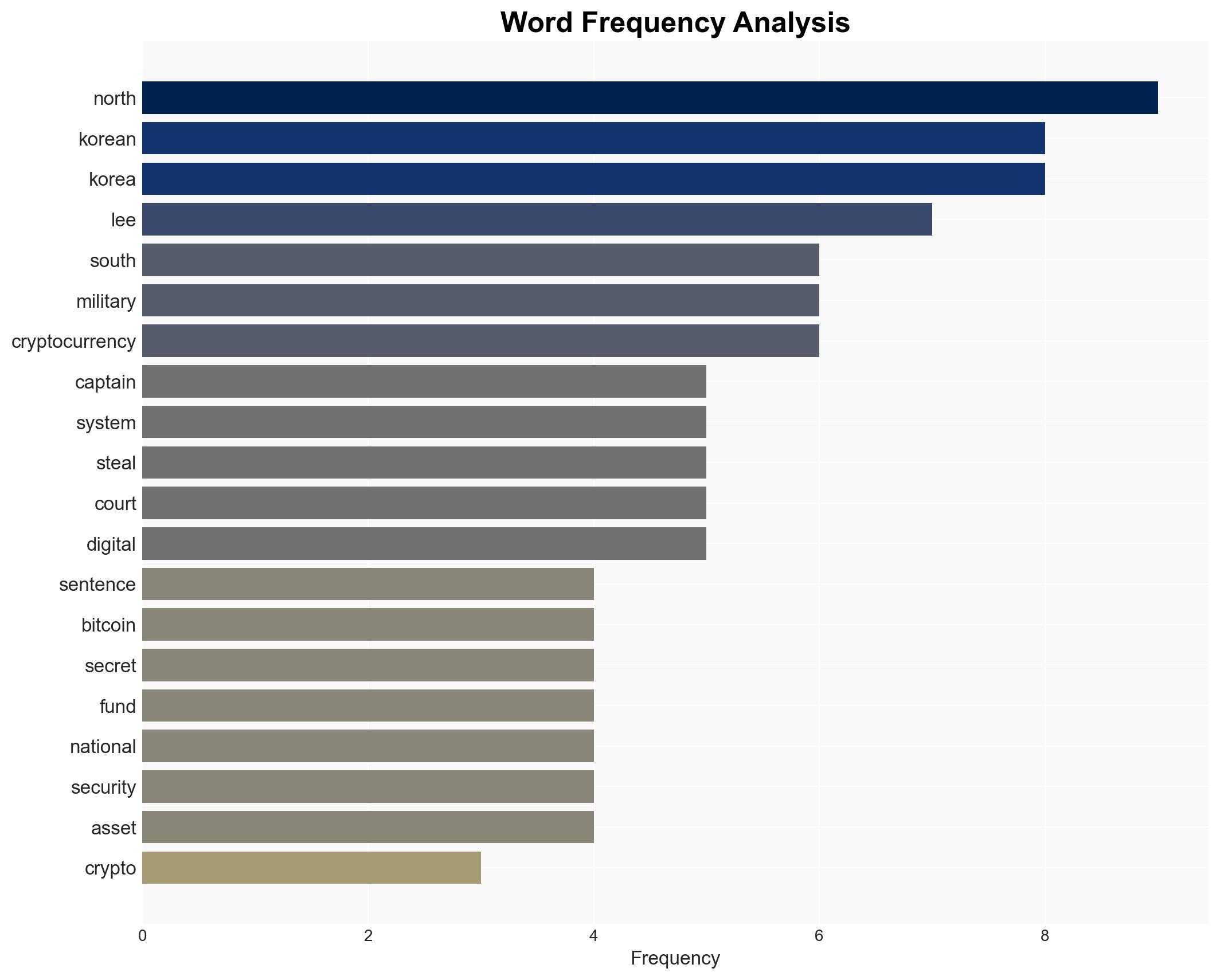
cybersecurity, cyber-espionage, cryptocurrency, North Korea, sanctions evasion, military intelligence, cyber defense, national security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us