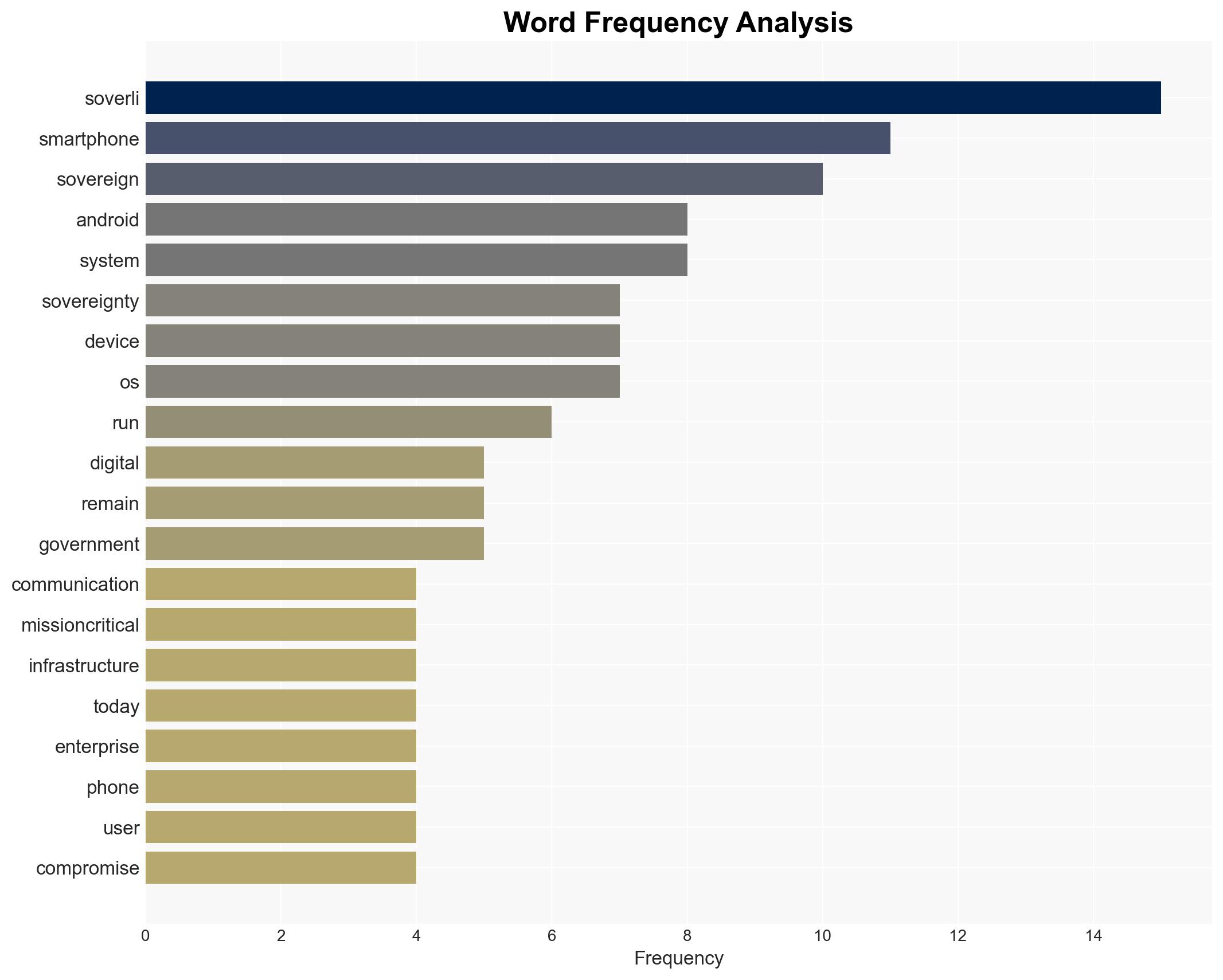
Soverli Secures $2.6 Million Pre-Seed Funding to Enhance Digital Sovereignty for Smartphones
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Soverli Raises 26M Pre-Seed to Bring Secure and Convenient Digital Freedom to Every Smartphone
1. BLUF (Bottom Line Up Front)
Soverli’s development of a sovereign smartphone architecture represents a significant advancement in digital sovereignty, potentially impacting OEMs, enterprises, governments, and consumers by enhancing security without sacrificing usability. The initiative aligns with Europe’s strategic priorities, suggesting a moderate confidence level in its potential to reshape the digital landscape, contingent on broader adoption and integration challenges.
2. Competing Hypotheses
- Hypothesis A: Soverli’s technology will successfully enhance digital sovereignty by allowing secure and convenient dual-OS functionality on smartphones. Supporting evidence includes the patent-pending methodology and the ability to run a sovereign OS alongside Android without hardware modifications. Key uncertainties involve market adoption and integration with existing systems.
- Hypothesis B: Soverli’s technology may face significant adoption barriers, limiting its impact on digital sovereignty. Contradicting evidence includes potential resistance from major OS providers and user reluctance to adopt new systems. The success of this hypothesis depends on the competitive response from established tech companies.
- Assessment: Hypothesis A is currently better supported due to the unique technological capabilities and strategic alignment with European priorities. Indicators such as increased investment and partnerships could further validate this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The technology will function as described without significant technical flaws; market demand for digital sovereignty solutions will grow; Soverli will secure necessary regulatory approvals.
- Information Gaps: Details on the scalability of Soverli’s technology and its integration with existing infrastructure are lacking.
- Bias & Deception Risks: Potential bias from investors and stakeholders with vested interests; risk of overstatement of technological capabilities by Soverli.
4. Implications and Strategic Risks
This development could significantly influence the digital sovereignty landscape, potentially altering power dynamics in the tech industry and affecting national security strategies.
- Political / Geopolitical: Could strengthen Europe’s position in tech sovereignty, potentially leading to tensions with non-European tech giants.
- Security / Counter-Terrorism: Enhanced security features may reduce vulnerabilities in critical infrastructure and communications.
- Cyber / Information Space: May lead to a shift in cyber defense strategies, focusing on sovereign infrastructure.
- Economic / Social: Could drive innovation and competition in the smartphone market, impacting consumer choice and economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Soverli’s market entry strategies and partnerships; assess regulatory developments in digital sovereignty.
- Medium-Term Posture (1–12 months): Develop partnerships with Soverli for secure communications; invest in complementary technologies and capabilities.
- Scenario Outlook: Best: Widespread adoption enhances security and sovereignty. Worst: Technological or market failures limit impact. Most-Likely: Gradual adoption with incremental security improvements.
6. Key Individuals and Entities
- Founderful
- ETH Zurich Foundation
- Venture Kick
- Soverli
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, digital sovereignty, smartphone technology, European tech policy, dual-OS architecture, market adoption, regulatory challenges
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us