Spain detains 34 individuals linked to Black Axe in major cyber fraud crackdown across multiple cities
Published on: 2026-01-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Spain arrests 34 suspects linked to Black Axe cyber crime
1. BLUF (Bottom Line Up Front)
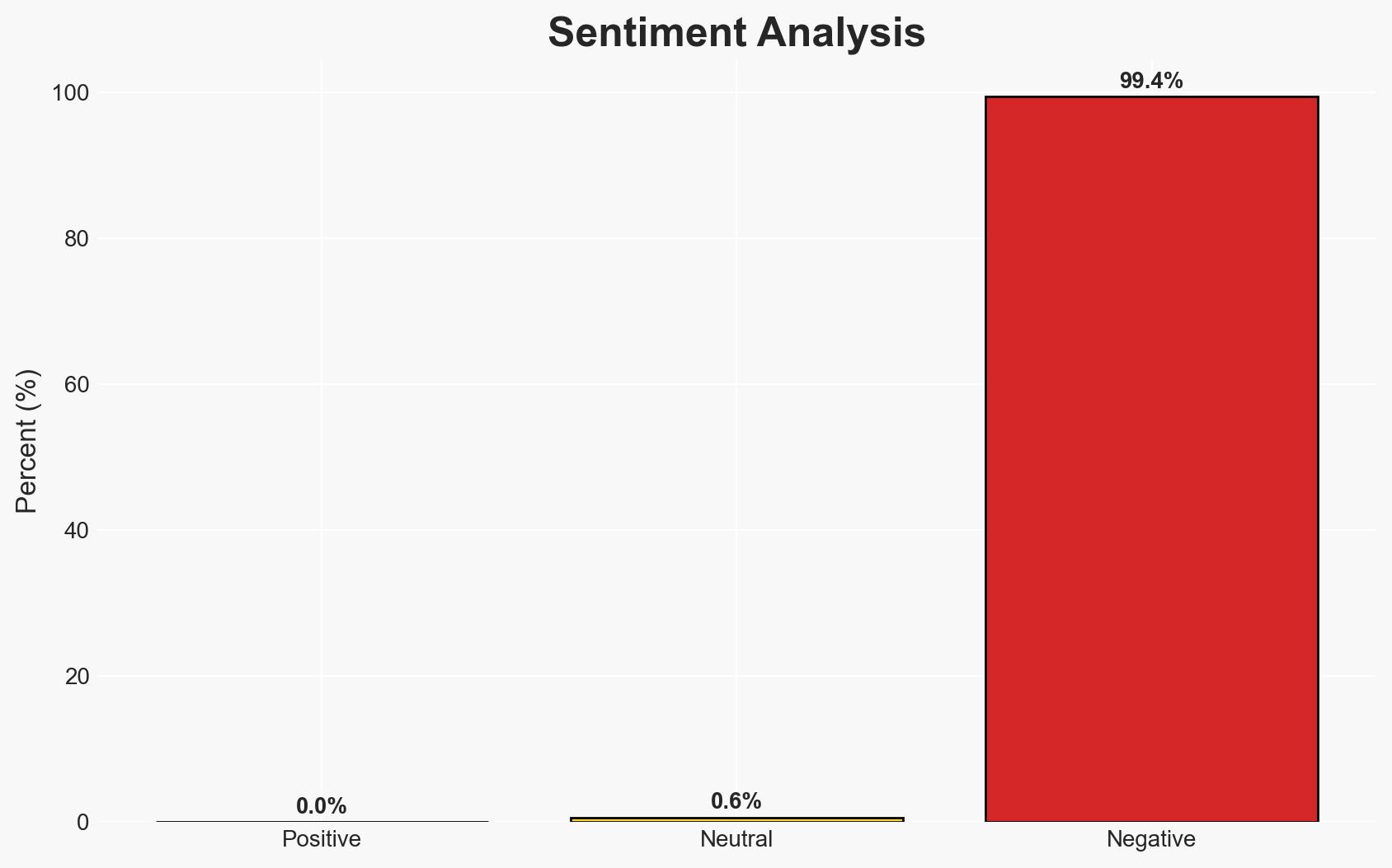
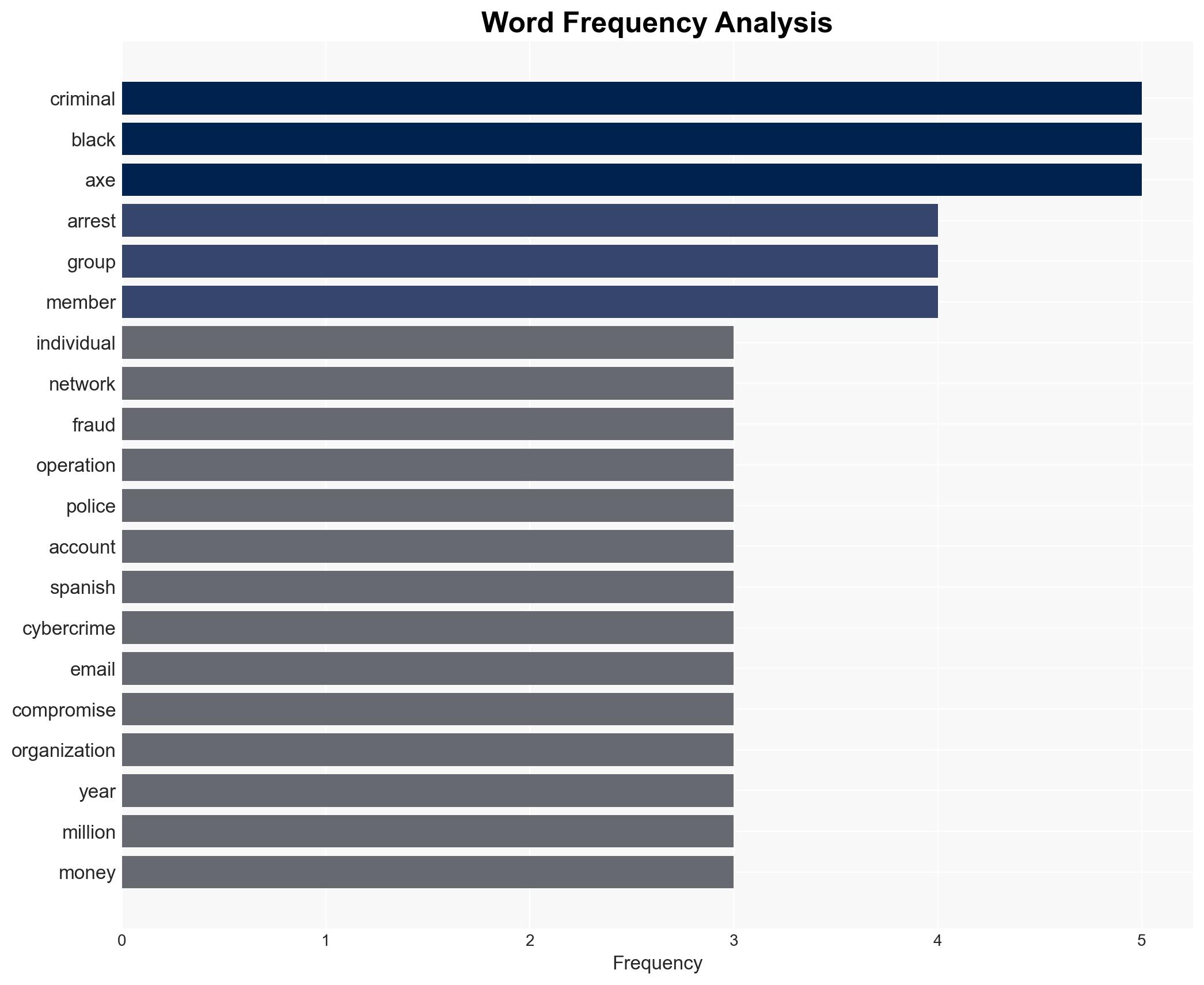
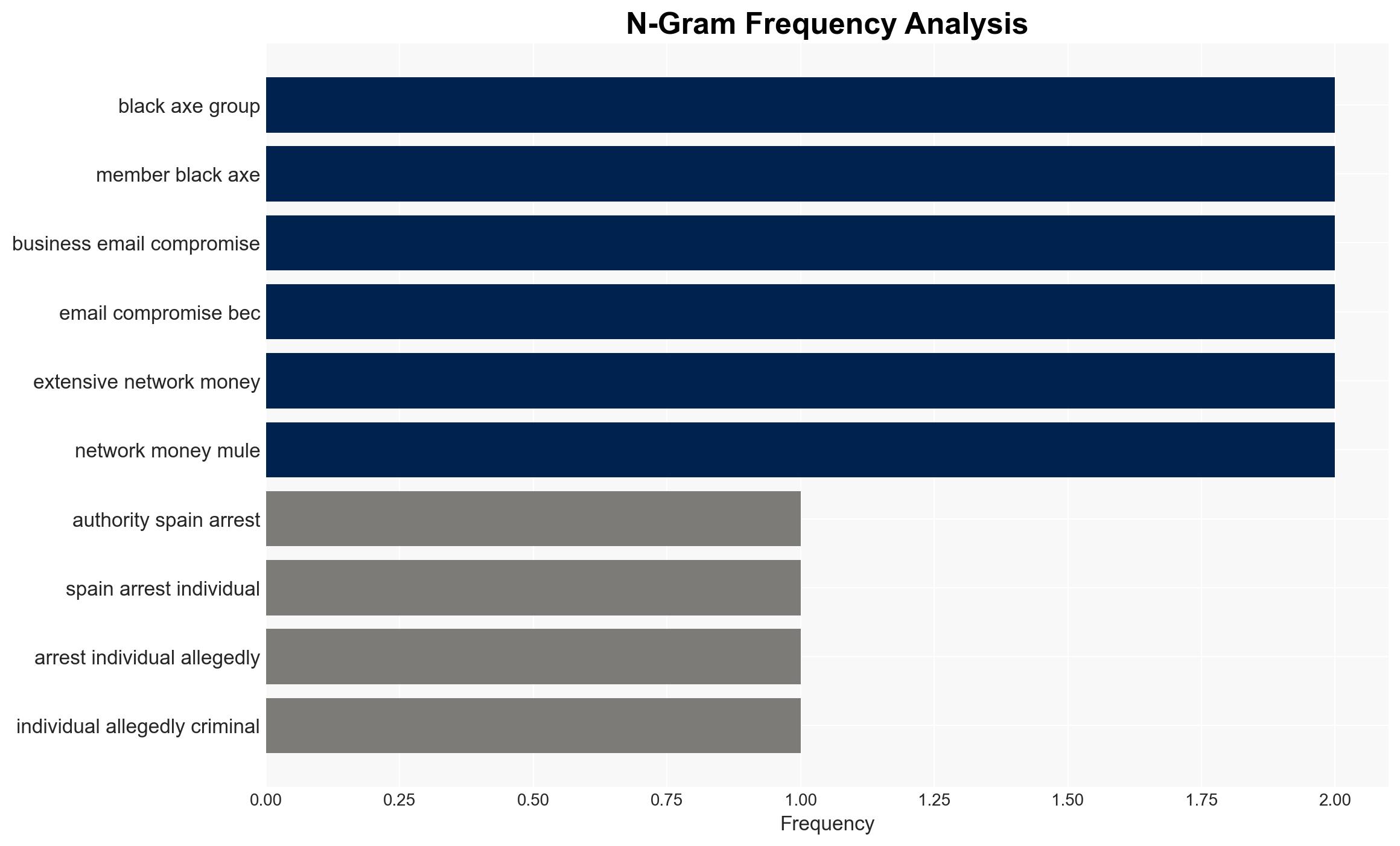
Spanish authorities have dismantled a significant cybercrime network linked to the Black Axe group, arresting 34 suspects involved in business email compromise (BEC) scams. This operation, supported by Europol and Bavarian police, highlights the transnational nature of cybercrime and the group’s extensive European operations. The arrests may disrupt Black Axe’s activities temporarily, but the group’s resilience and global reach suggest ongoing threats. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The arrests will significantly disrupt Black Axe’s operations in Europe, leading to a reduction in cybercrime activities. Supporting evidence includes the arrest of key suspects and seizure of assets. Contradicting evidence includes the group’s historical resilience and ability to adapt.
- Hypothesis B: The arrests will have limited long-term impact on Black Axe’s operations, as the group will quickly adapt and continue its activities. This is supported by Black Axe’s extensive network and history of global operations. Contradicting evidence includes the immediate disruption of their European operations.
- Assessment: Hypothesis B is currently better supported due to Black Axe’s demonstrated adaptability and global reach. Indicators such as continued cybercrime incidents linked to Black Axe would reinforce this judgment, while a sustained decrease in such activities could shift it towards Hypothesis A.
3. Key Assumptions and Red Flags
- Assumptions: The arrested individuals are key operatives within Black Axe; the group’s operations are significantly centralized; Europol’s intelligence on Black Axe is comprehensive.
- Information Gaps: Details on the full extent of Black Axe’s European network; potential undiscovered cybercrime operations; the group’s adaptive strategies post-arrests.
- Bias & Deception Risks: Potential over-reliance on Europol and Spanish police sources; risk of underestimating Black Axe’s resilience and adaptability.
4. Implications and Strategic Risks
The arrests could temporarily disrupt Black Axe’s operations but may also prompt the group to adapt and evolve its tactics. This development could influence broader cybercrime dynamics in Europe and beyond.
- Political / Geopolitical: Potential for increased international cooperation against transnational cybercrime; possible diplomatic tensions if operations extend into other jurisdictions.
- Security / Counter-Terrorism: Short-term reduction in BEC scams; potential for retaliatory cyber activities by Black Axe.
- Cyber / Information Space: Increased focus on cybersecurity measures by targeted companies; potential shifts in cybercrime tactics.
- Economic / Social: Temporary relief for businesses affected by BEC scams; potential social unrest if Black Axe shifts to more aggressive criminal activities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cybercrime activities linked to Black Axe; strengthen international law enforcement collaboration.
- Medium-Term Posture (1–12 months): Develop resilience measures for businesses against BEC scams; invest in intelligence capabilities to track Black Axe’s adaptations.
- Scenario Outlook:
- Best: Sustained disruption of Black Axe operations, leading to a significant reduction in cybercrime.
- Worst: Black Axe adapts and escalates its activities, leading to increased cybercrime incidents.
- Most-Likely: Temporary disruption with gradual resumption of Black Axe’s operations in Europe.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cybercrime, Black Axe, international cooperation, business email compromise, Europol, transnational crime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us