Staffing giant Manpower hit by major data breach – around 145000 users affected here’s what we know – TechRadar
Published on: 2025-08-13
Intelligence Report: Staffing giant Manpower hit by major data breach – around 145000 users affected here’s what we know – TechRadar
1. BLUF (Bottom Line Up Front)
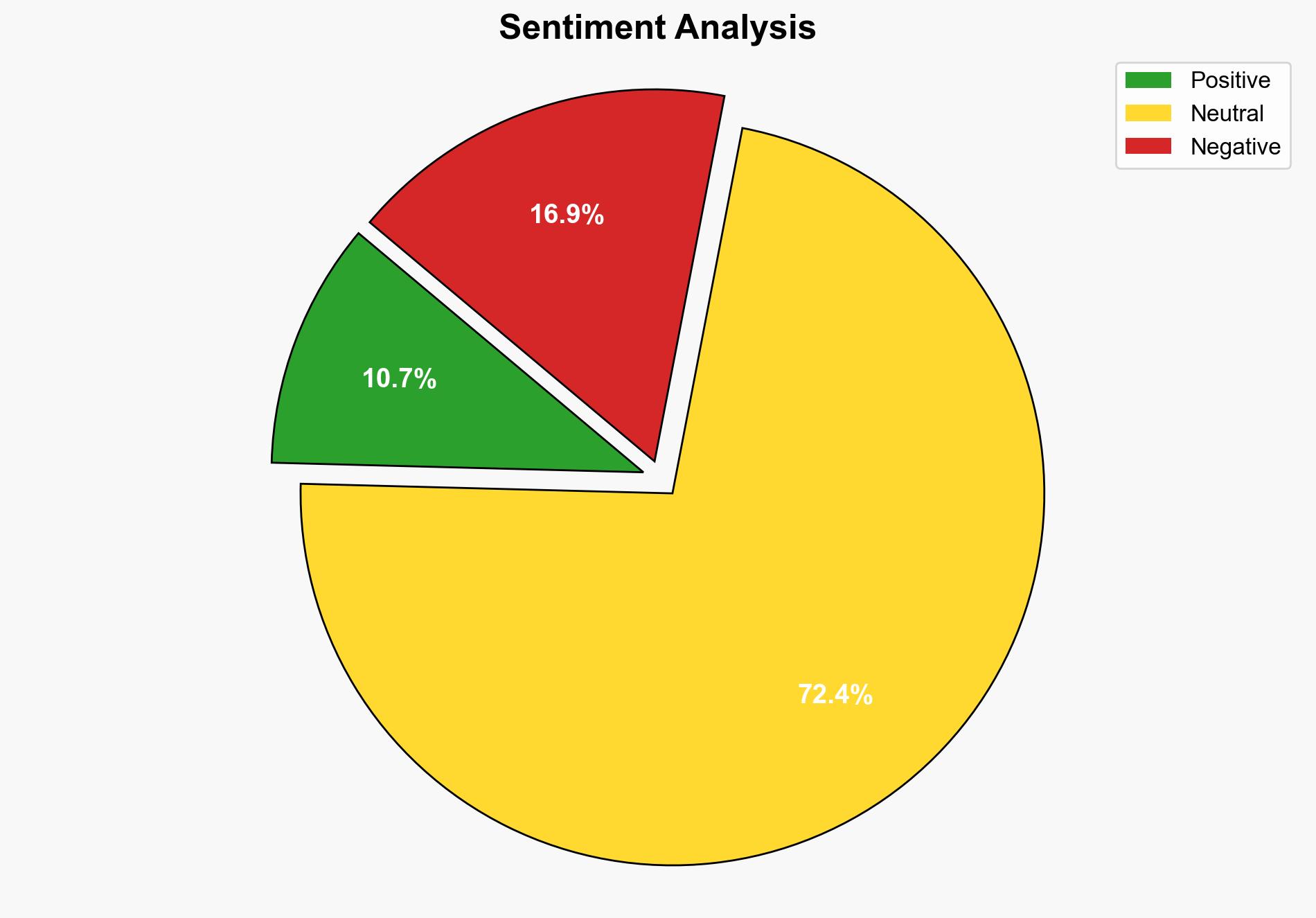
The data breach at Manpower, affecting approximately 145,000 users, is likely the result of a ransomware attack by the group known as Ransomhub. The most supported hypothesis is that the breach was financially motivated, with the attackers seeking ransom payments. Confidence in this assessment is moderate due to the removal of leaked data from the Ransomhub website, suggesting a possible ransom payment. Recommended actions include enhancing cybersecurity measures and providing affected users with identity theft protection.
2. Competing Hypotheses
Hypothesis 1: The breach was a financially motivated ransomware attack by Ransomhub, aiming to extort money from Manpower.
Hypothesis 2: The breach was a state-sponsored cyber-espionage operation disguised as a ransomware attack to exfiltrate sensitive data for strategic purposes.
Using ACH 2.0, Hypothesis 1 is better supported by the evidence, including the known modus operandi of Ransomhub and the removal of data from their site, which suggests a financial transaction. Hypothesis 2 lacks direct evidence linking state actors to the breach.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the removal of data from the Ransomhub site indicates a ransom payment. Another assumption is that Ransomhub operates independently without state sponsorship.
Red Flags: The absence of explicit confirmation of a ransom payment and the potential for data to be sold on the dark web if not paid. The timing of the breach during a period of heightened geopolitical tensions could indicate alternative motives.
4. Implications and Strategic Risks
The breach could lead to significant financial losses for Manpower and damage its reputation. There is a risk of identity theft and fraud for affected individuals. If state-sponsored, the breach could indicate broader cyber-espionage activities targeting sensitive corporate data. The incident underscores vulnerabilities in corporate cybersecurity defenses, potentially encouraging further attacks.
5. Recommendations and Outlook
- Enhance cybersecurity infrastructure and conduct regular security audits.
- Provide comprehensive identity theft protection services to affected users.
- Engage with law enforcement and cybersecurity experts to trace the origins of the attack.
- Scenario Projections:
- Best Case: Manpower successfully mitigates the breach impact, and no further data is compromised.
- Worst Case: Data is sold on the dark web, leading to widespread identity theft and financial losses.
- Most Likely: Manpower strengthens its cybersecurity, but faces short-term reputational damage and financial costs.
6. Key Individuals and Entities
Ransomhub (ransomware group), Manpower (affected entity), Equifax (identity theft protection provider).
7. Thematic Tags
national security threats, cybersecurity, data breach, ransomware, corporate espionage