State-sponsored phishing campaigns targeting military and journalist accounts on Signal, warns German authori…
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: State-backed phishing attacks targeting military officials and journalists on Signal
1. BLUF (Bottom Line Up Front)
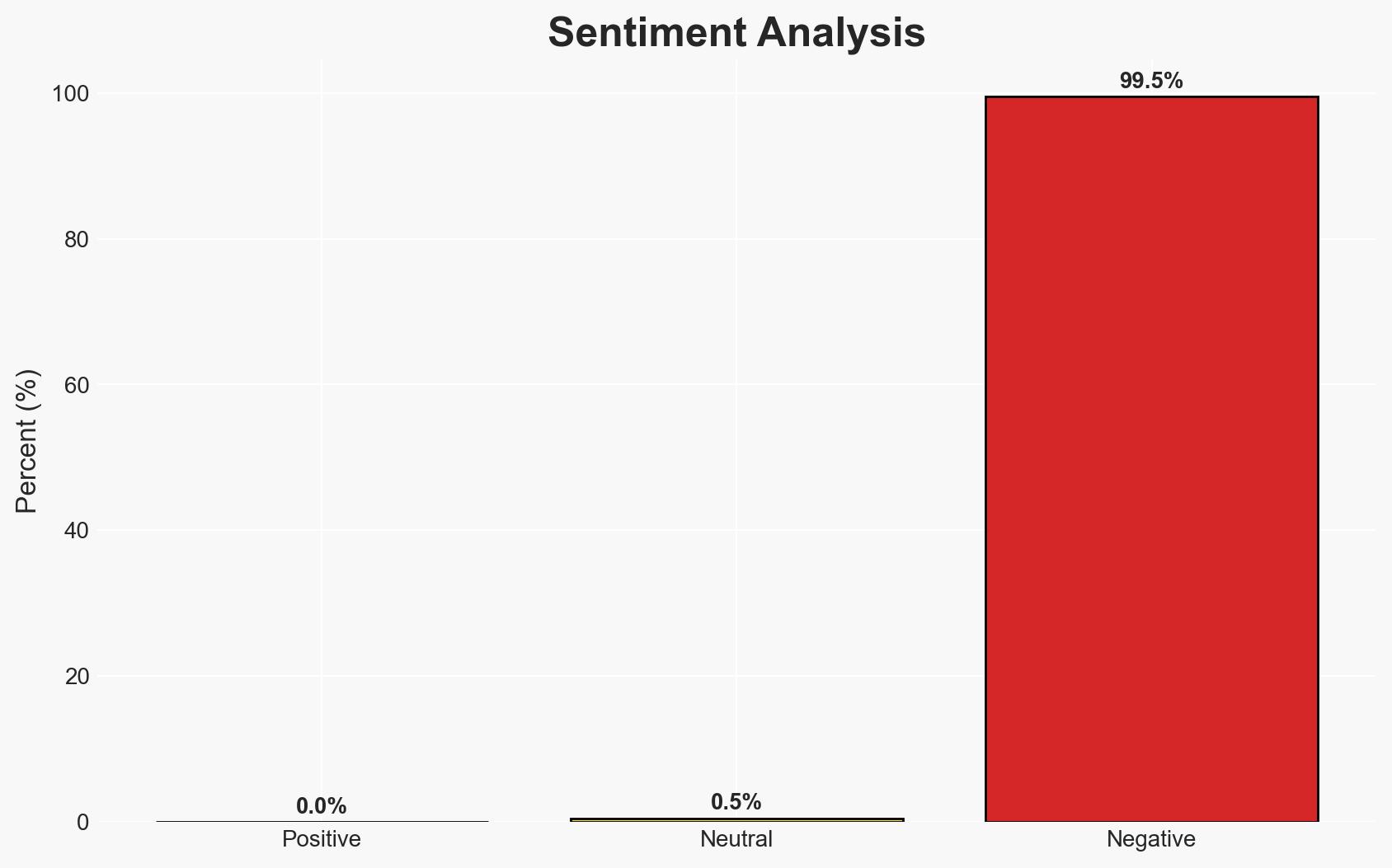
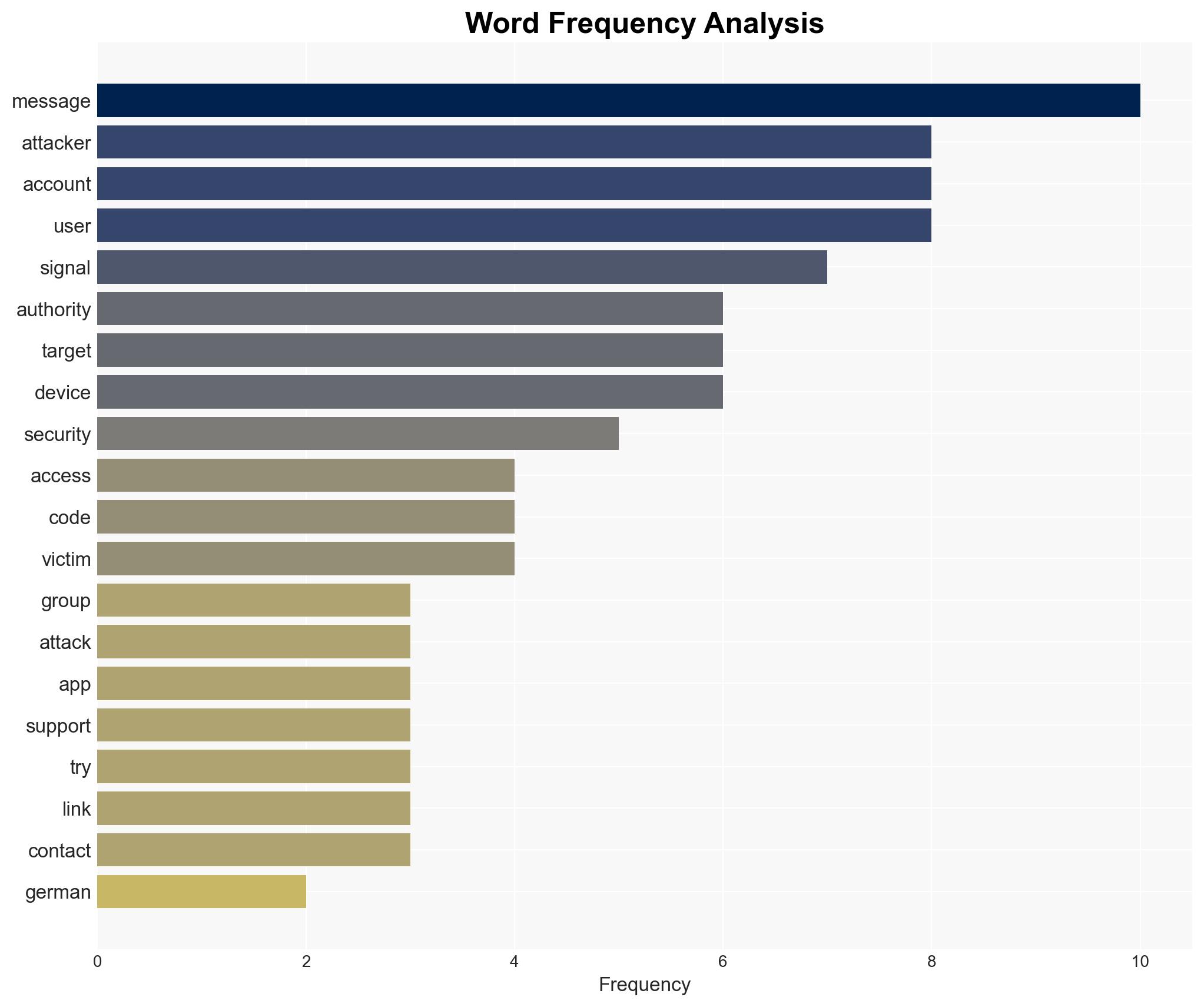
German security authorities have identified a likely state-backed cyber actor targeting military officials, diplomats, and journalists via Signal with phishing attacks. The primary objective appears to be account takeover for intelligence gathering. The assessment currently supports the hypothesis of state involvement, with moderate confidence, due to the sophistication and targeting of the attacks.
2. Competing Hypotheses
- Hypothesis A: The attacks are conducted by a state-backed actor aiming to gather intelligence from high-value targets. Evidence includes the sophisticated nature of the attacks and the strategic selection of targets. However, the lack of direct attribution to a specific state actor remains a key uncertainty.
- Hypothesis B: The attacks are perpetrated by non-state actors or financially motivated cybercriminals using similar techniques. This is supported by the possibility of non-state actors employing such methods, but the high-value target selection suggests a more strategic intent typical of state actors.
- Assessment: Hypothesis A is currently better supported due to the sophistication and strategic target selection indicative of state-backed operations. Indicators such as direct attribution or further technical analysis could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have the capability to execute sophisticated phishing operations; the targets are of strategic interest to a state actor; Signal’s security features are being effectively bypassed.
- Information Gaps: Lack of specific attribution to a nation-state; technical details on how the phishing methods were developed and deployed.
- Bias & Deception Risks: Potential confirmation bias towards state actor involvement; possibility of false flag operations by non-state actors to mislead attribution efforts.
4. Implications and Strategic Risks
This development could lead to increased tensions between states if attribution is confirmed, potentially escalating cyber operations. It may also prompt enhanced security measures and international cooperation in cyber defense.
- Political / Geopolitical: Potential diplomatic strains if a specific state is identified; increased scrutiny on state-sponsored cyber activities.
- Security / Counter-Terrorism: Heightened threat environment for targeted sectors; potential for broader cyber espionage campaigns.
- Cyber / Information Space: Increased focus on securing communication platforms; potential for similar attacks on other messaging services.
- Economic / Social: Possible impacts on public trust in secure communication platforms; increased demand for cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing activities; advise potential targets on security best practices; collaborate with international partners for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for communication platforms; strengthen public-private partnerships in cybersecurity; invest in capability development for threat detection and response.
- Scenario Outlook:
- Best: Increased security measures deter further attacks, and international cooperation leads to attribution and diplomatic resolution.
- Worst: Escalation of cyber operations leads to broader geopolitical tensions and widespread disruption of communication networks.
- Most-Likely: Continued phishing attempts with gradual improvements in detection and response, but without clear attribution.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, state-sponsored attacks, phishing, intelligence gathering, Signal security, information security, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us