Stealthy Attackers Employ Advanced Techniques for Data Exfiltration and Extortion, Warns Picus Security
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Digital Parasite Warning as Attackers Favor Stealth for Extortion
1. BLUF (Bottom Line Up Front)
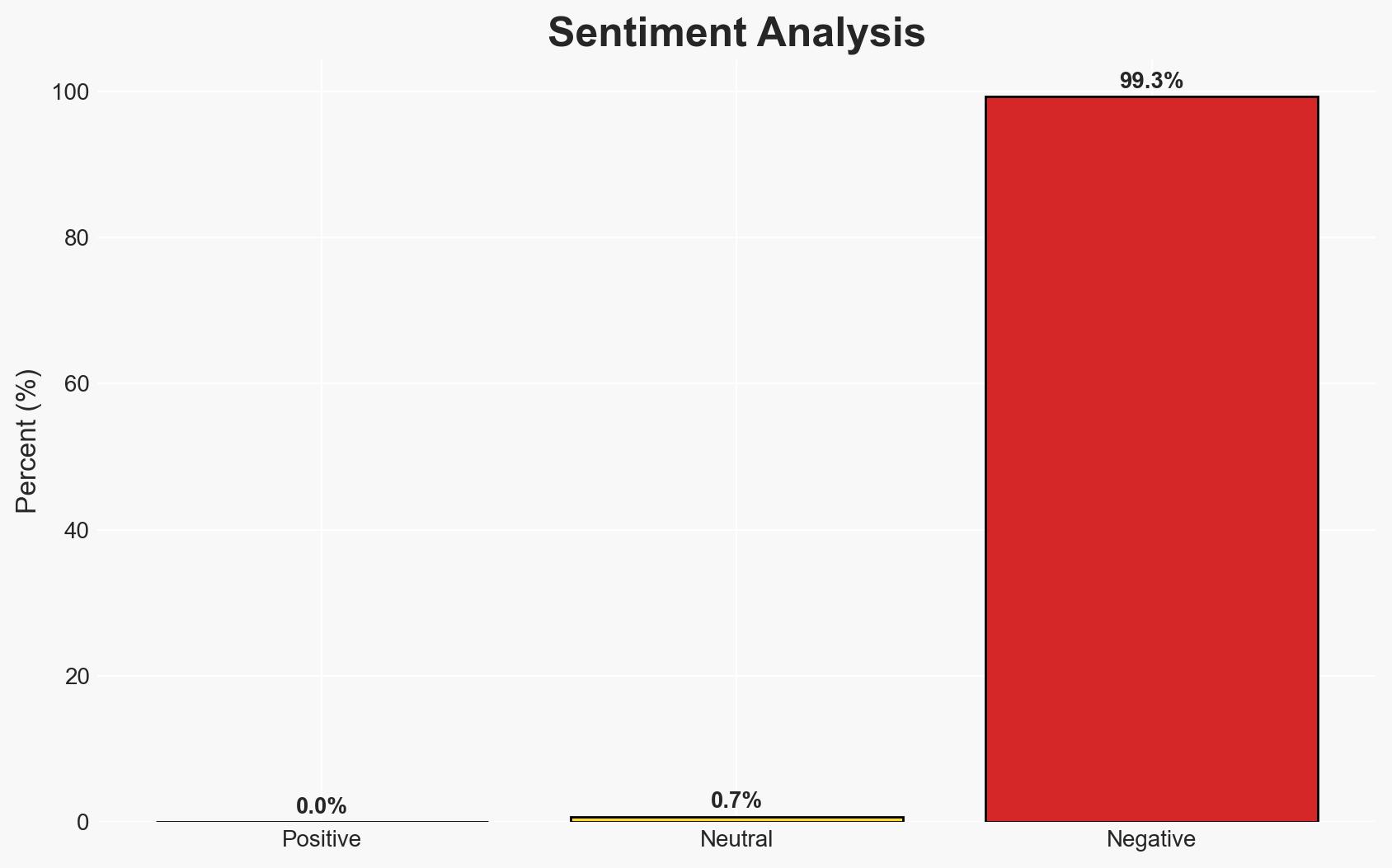
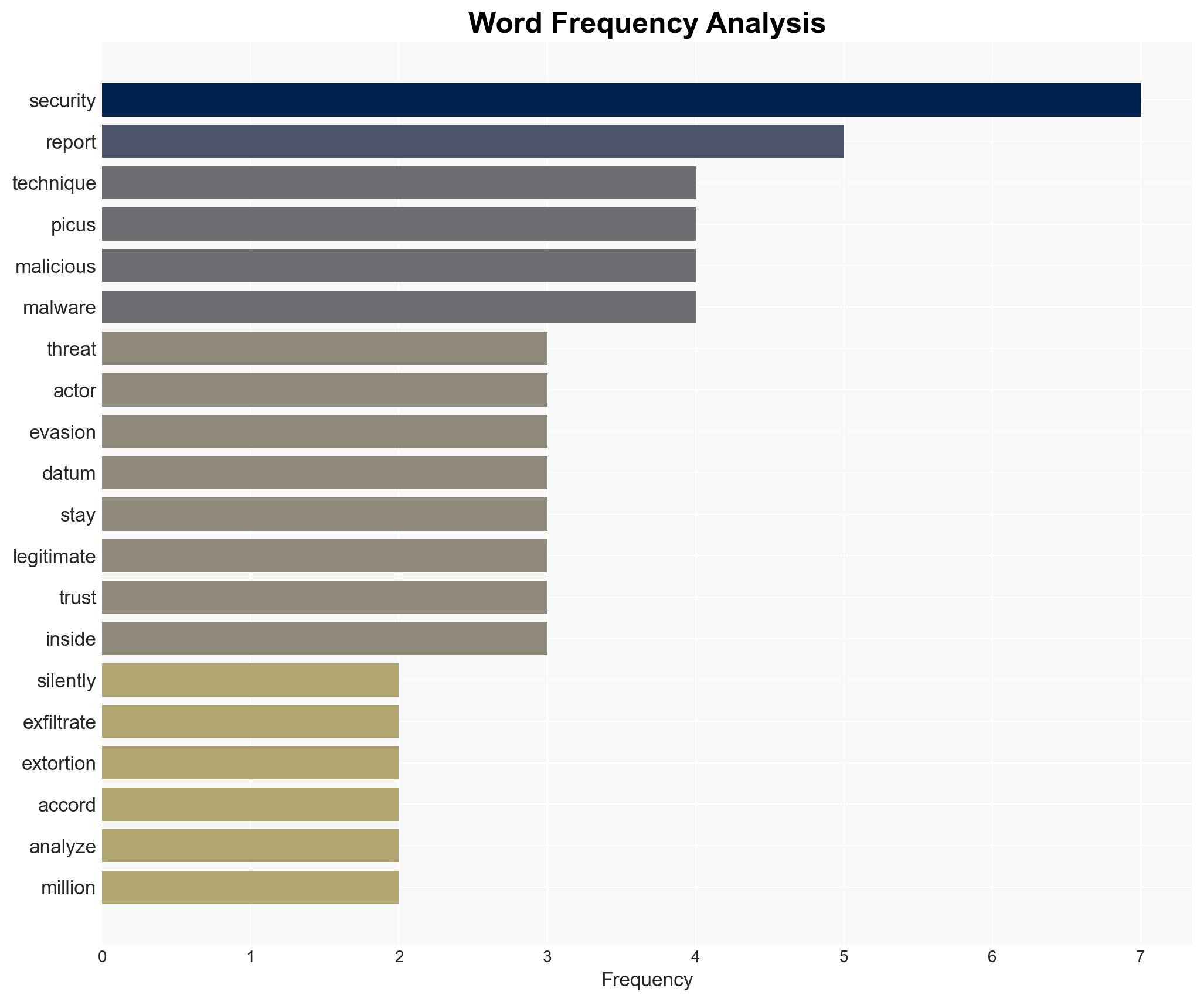
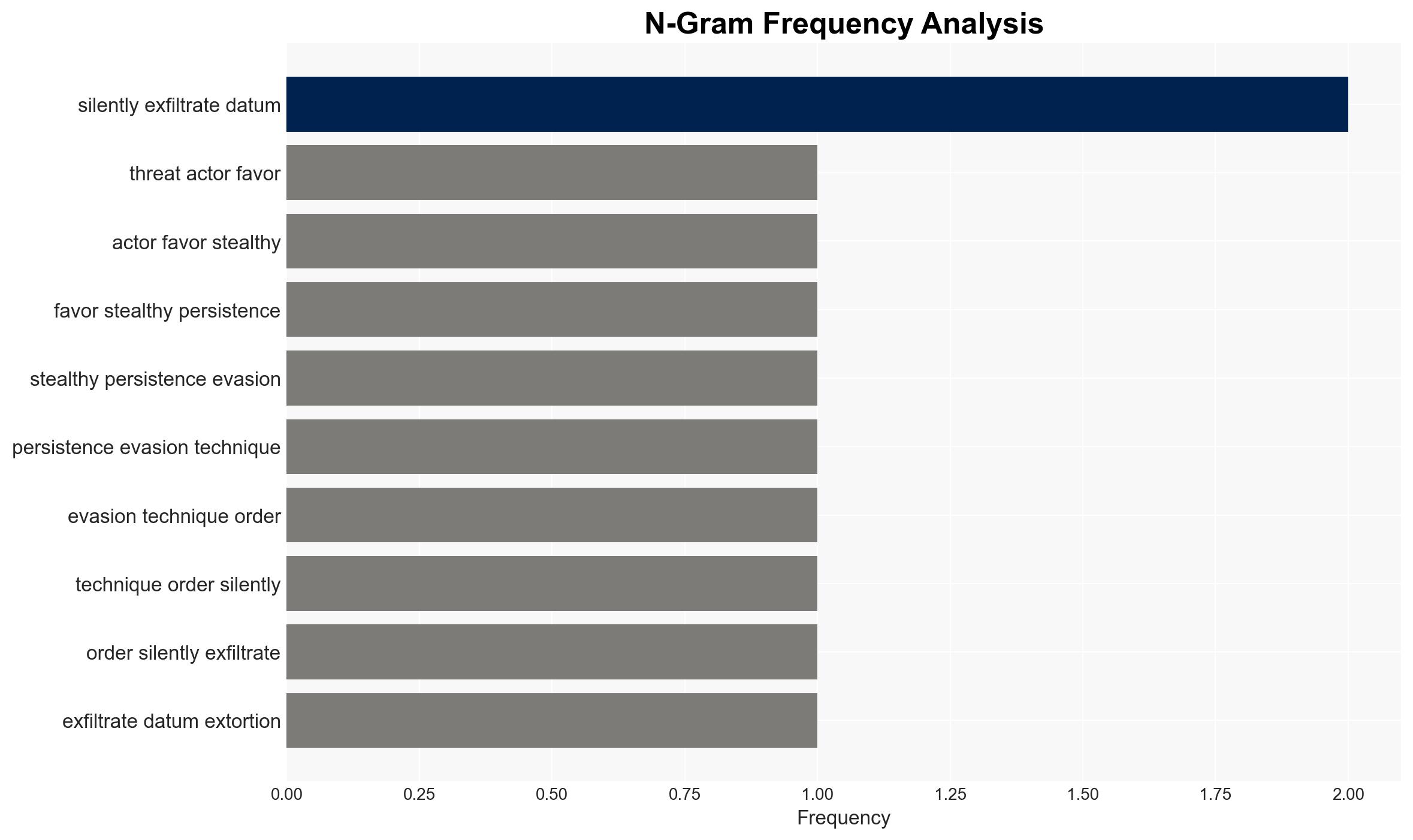
Threat actors are increasingly using stealthy techniques to exfiltrate data for extortion, favoring persistence and evasion over encryption. This shift complicates detection and defense mechanisms, posing significant risks to organizations reliant on traditional security measures. The most likely hypothesis is that these methods will continue to evolve, increasing the sophistication of cyber threats. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Threat actors are primarily motivated by the increased profitability of data extortion over traditional ransomware attacks. Supporting evidence includes the reported decrease in encryption-based attacks and the increased use of stealth techniques. Key uncertainties include the potential for changes in threat actor motivations or external pressures that could alter current trends.
- Hypothesis B: The shift towards stealthy techniques is driven by improved defensive capabilities that make traditional ransomware attacks less effective. This is supported by the increasing complexity and sophistication of evasion techniques. Contradicting evidence includes the continued success of some ransomware attacks, suggesting that defenses are not uniformly effective.
- Assessment: Hypothesis A is currently better supported due to the clear trend towards data exfiltration and stealth, as evidenced by the decrease in encryption-based attacks. Indicators that could shift this judgment include significant advancements in defensive technologies or a resurgence in successful ransomware campaigns.
3. Key Assumptions and Red Flags
- Assumptions: Threat actors prioritize profitability; current detection methods are insufficient against stealth techniques; threat actors have the capability to adapt quickly to defensive measures.
- Information Gaps: Detailed data on the success rates of stealth techniques versus traditional ransomware; insights into the decision-making processes of threat actors.
- Bias & Deception Risks: Potential bias in the data due to reliance on a single security vendor’s report; risk of deception by threat actors to mislead defenders about their true capabilities and intentions.
4. Implications and Strategic Risks
The evolution towards stealthy data exfiltration techniques could lead to prolonged undetected breaches, increasing the potential for significant data loss and extortion. This development may also drive a shift in cybersecurity strategies and investments.
- Political / Geopolitical: Potential for increased tensions as state actors may exploit these techniques for espionage.
- Security / Counter-Terrorism: Heightened threat environment requiring enhanced detection and response capabilities.
- Cyber / Information Space: Increased complexity in cyber defense operations, necessitating advanced threat intelligence and monitoring.
- Economic / Social: Potential economic impact from data breaches and extortion demands, affecting business continuity and public trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring for stealth techniques, prioritize threat intelligence sharing, and review incident response plans.
- Medium-Term Posture (1–12 months): Invest in advanced detection technologies, foster public-private partnerships for cybersecurity, and develop adaptive defense strategies.
- Scenario Outlook: Best: Effective countermeasures reduce threat actor success; Worst: Proliferation of stealth techniques overwhelms defenses; Most-Likely: Continued evolution of threat tactics with periodic successful breaches.
6. Key Individuals and Entities
- Picus Security, Süleyman Özarslan (Co-founder of Picus Security)
7. Thematic Tags
cybersecurity, data exfiltration, threat actors, stealth techniques, ransomware evolution, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us