Step Finance suffers $27M treasury hack, causing STEP token to plummet over 90%
Published on: 2026-02-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Step Finance treasury breach leads to 27M in losses STEP crashes 90
1. BLUF (Bottom Line Up Front)
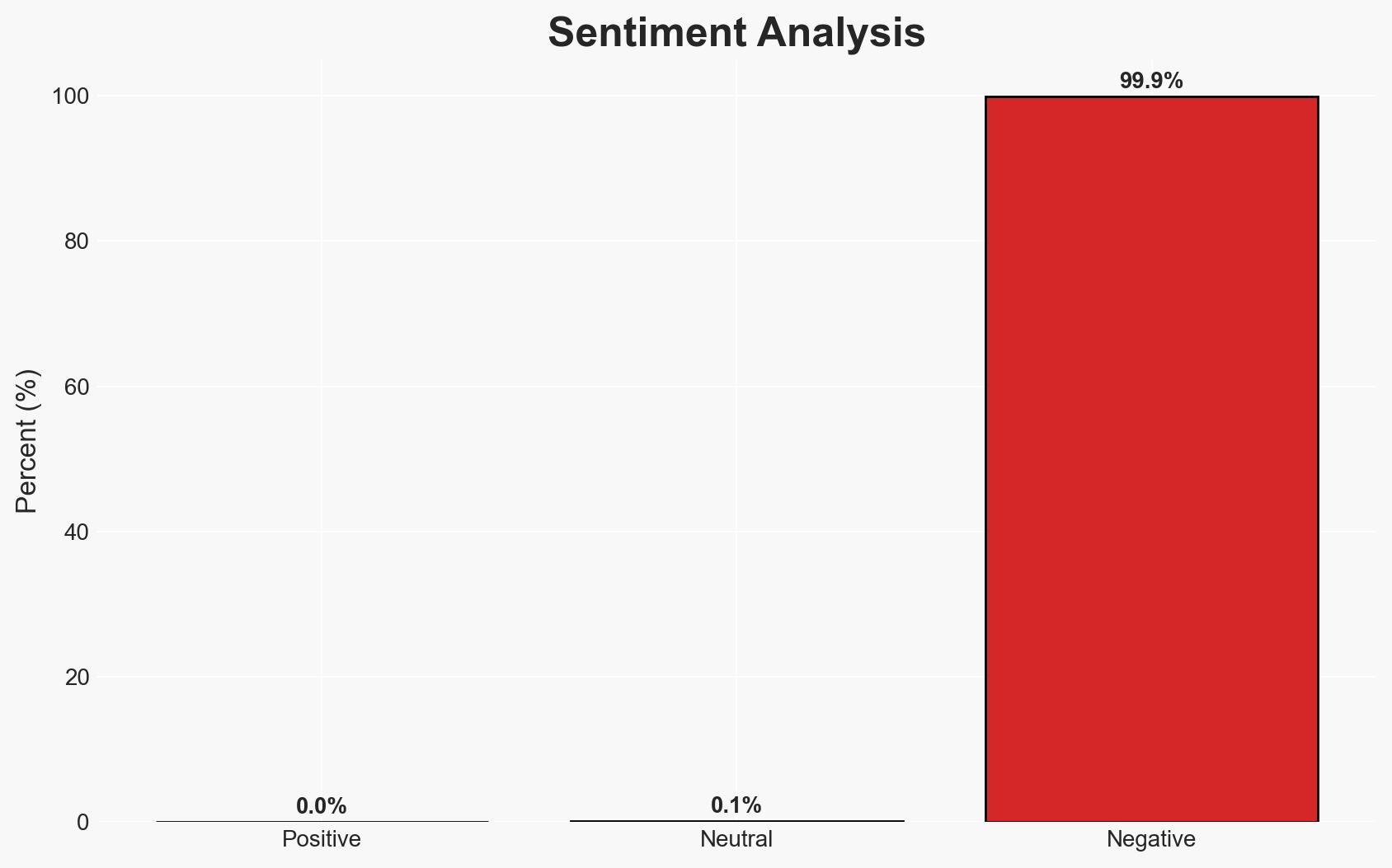
The breach of Step Finance’s treasury wallets has resulted in significant financial losses and a drastic decline in the value of its governance token, STEP. The incident highlights vulnerabilities in decentralized finance (DeFi) platforms and could lead to long-term reputational damage. The most likely hypothesis is that the breach was executed through a known attack vector, although the specifics remain unclear. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was facilitated through a known attack vector, possibly involving compromised keys or a smart contract flaw. Supporting evidence includes the platform’s acknowledgment of a “well-known attack vector” and the sophistication of the attack. Key uncertainties include the exact method of compromise and whether internal access issues contributed.
- Hypothesis B: The breach resulted from an internal security failure or insider threat. Contradicting evidence includes the lack of disclosure on internal failures and the absence of any specific indicators pointing to insider involvement. However, the lack of transparency from Step Finance leaves this possibility open.
- Assessment: Hypothesis A is currently better supported due to the platform’s reference to a known attack vector and the involvement of a sophisticated actor. Indicators that could shift this judgment include new evidence of internal security lapses or insider involvement.
3. Key Assumptions and Red Flags
- Assumptions: The breach was executed by an external actor; the attack vector was previously known to cybersecurity professionals; Step Finance’s response will impact its recovery potential; user funds were not significantly affected.
- Information Gaps: Specific details of the attack vector used; confirmation of whether user funds were affected; internal security protocols of Step Finance.
- Bias & Deception Risks: Potential bias in Step Finance’s public communications to downplay internal failures; possible deception by the attacker to mislead attribution efforts.
4. Implications and Strategic Risks
This breach could undermine confidence in DeFi platforms, particularly those based on Solana, and may prompt increased scrutiny from regulators. The incident may also encourage further attacks on similar platforms, exploiting known vulnerabilities.
- Political / Geopolitical: Increased regulatory attention on DeFi platforms, potentially leading to stricter compliance requirements.
- Security / Counter-Terrorism: Heightened threat environment for DeFi platforms, necessitating improved security measures.
- Cyber / Information Space: Potential for increased cyber-attacks on blockchain platforms, exploiting similar vulnerabilities.
- Economic / Social: Loss of investor confidence in DeFi projects, leading to reduced liquidity and potential market instability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation to determine the breach’s specifics; enhance security protocols; communicate transparently with stakeholders.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for ongoing threat monitoring; implement robust crisis management frameworks; engage with regulators to align on compliance expectations.
- Scenario Outlook:
- Best: Successful identification and mitigation of vulnerabilities, restoring stakeholder confidence.
- Worst: Continued breaches and loss of user trust, leading to project failure.
- Most-Likely: Partial recovery with ongoing reputational challenges and increased regulatory oversight.
6. Key Individuals and Entities
- Step Finance
- CertiK (Blockchain security firm)
- Immunefi (Web3 security executives)
- Kerberus (CEO Alex Katz)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
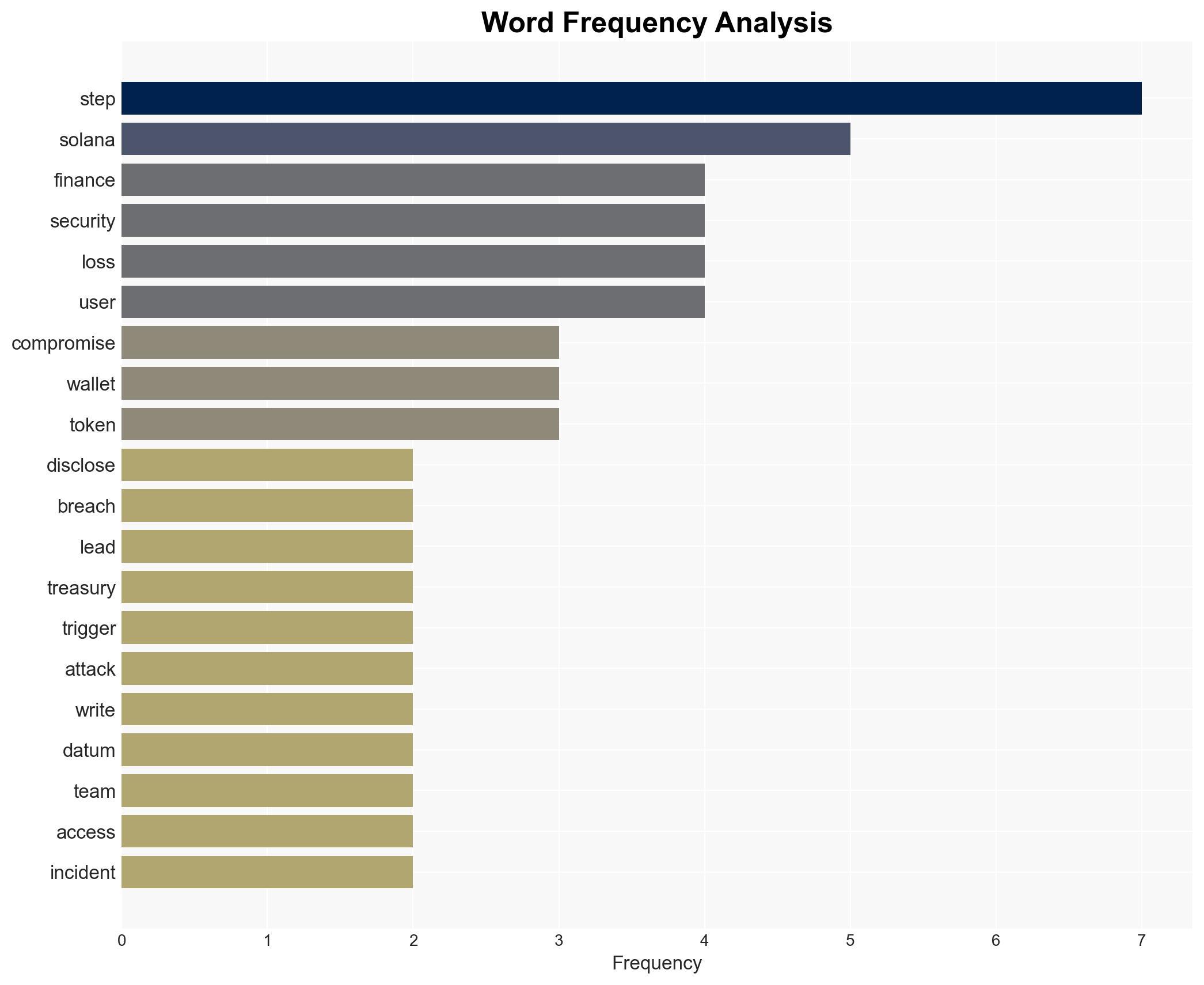
cybersecurity, decentralized finance, blockchain, financial crime, regulatory compliance, crisis management, reputational risk
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us