Surge in ShinyHunters vishing attacks targets major firms, exploiting SSO and MFA vulnerabilities
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Wave of ShinyHunters vishing attacks spreading fast
1. BLUF (Bottom Line Up Front)
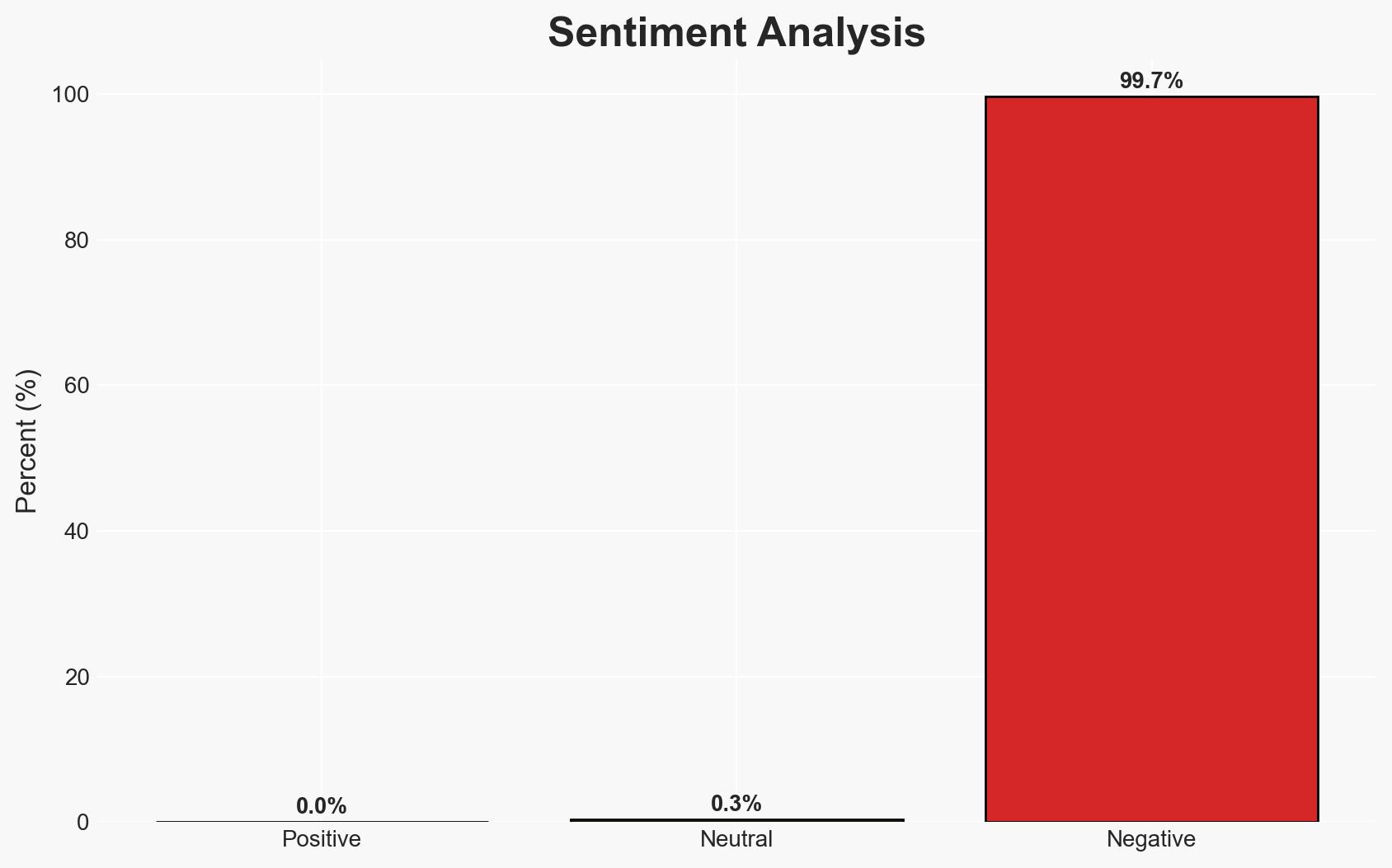
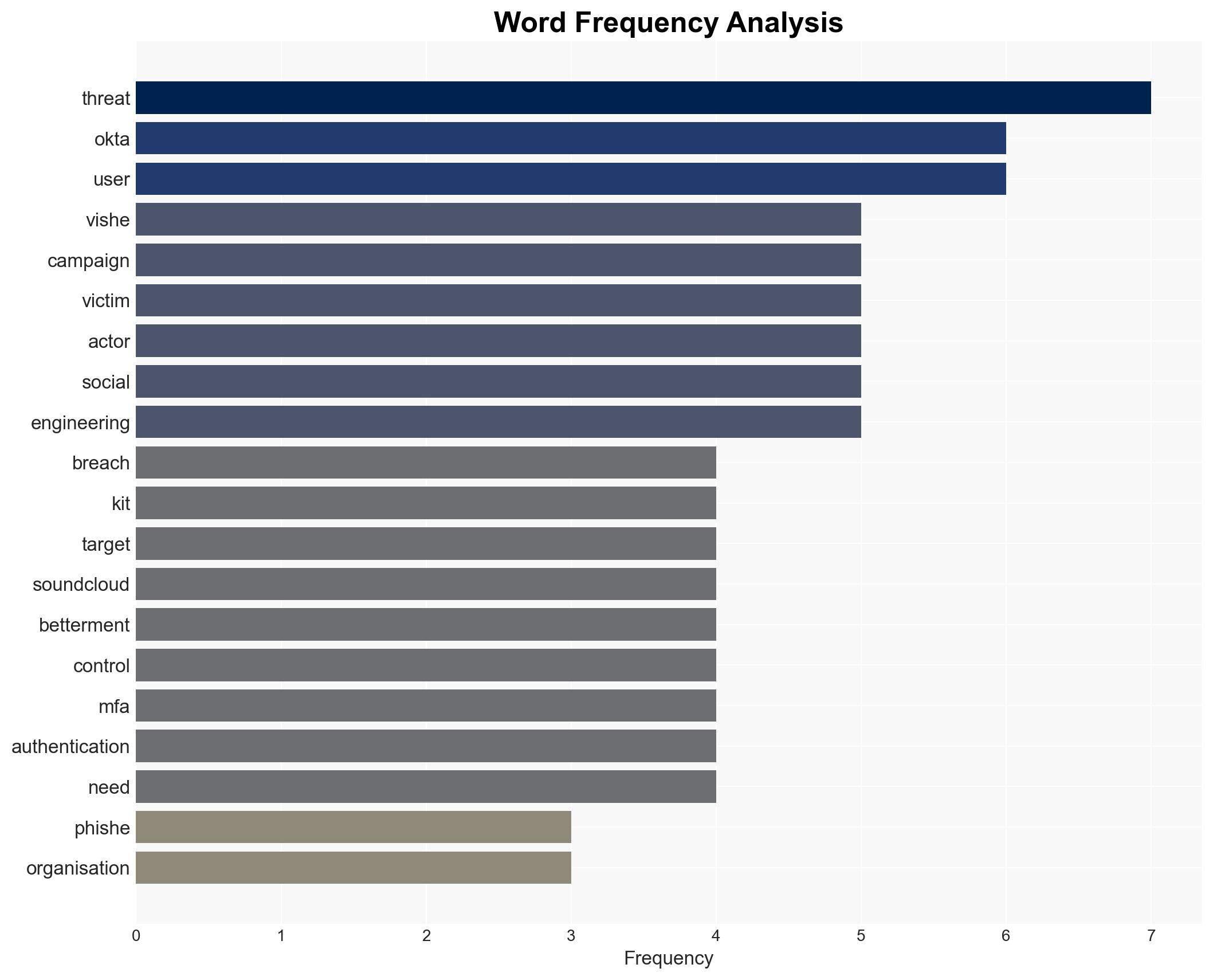
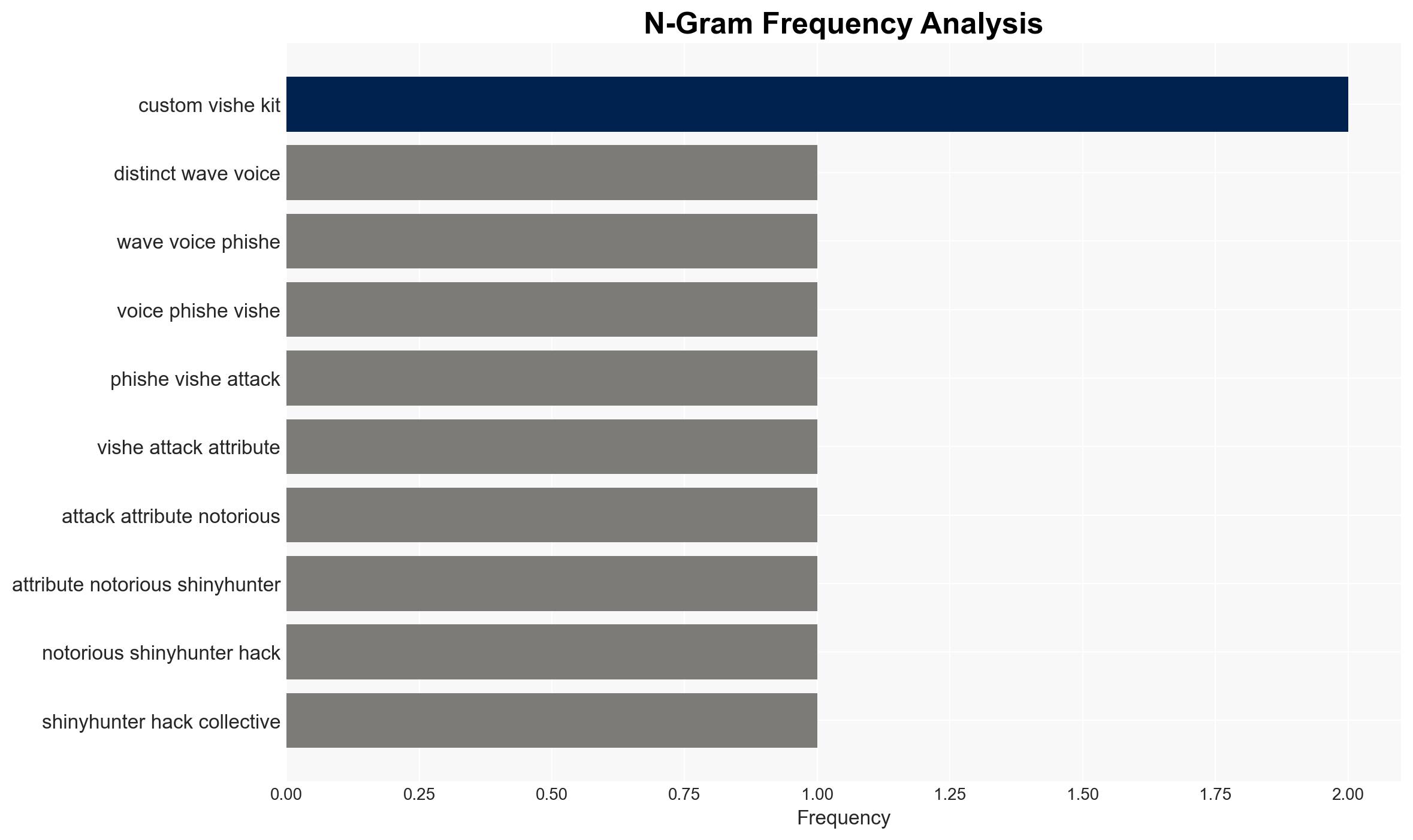
The ShinyHunters hacking collective is conducting a widespread vishing campaign targeting major organizations, exploiting vulnerabilities in single sign-on (SSO) and multi-factor authentication (MFA) processes. The campaign has affected companies like Crunchbase, SoundCloud, and Betterment. The overall confidence level in this assessment is moderate due to the evolving nature of the threat and incomplete information on the full scope of the campaign.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters is primarily motivated by financial gain through extortion and data theft. This is supported by evidence of extortion demands and data exfiltration. However, the full extent of their financial motivations remains uncertain.
- Hypothesis B: The campaign is part of a broader strategy to undermine trust in digital authentication systems, possibly with state-sponsored backing. This is less supported due to the lack of direct evidence linking the campaign to state actors, and the focus on financial extortion suggests a primary financial motive.
- Assessment: Hypothesis A is currently better supported due to the direct evidence of extortion and data theft. Indicators that could shift this judgment include evidence of state sponsorship or a shift in target selection towards more politically sensitive entities.
3. Key Assumptions and Red Flags
- Assumptions: The ShinyHunters group is acting independently without state sponsorship; the primary motivation is financial gain; current defenses against vishing are insufficient.
- Information Gaps: Full scope of affected organizations; detailed technical methods used in the vishing kits; potential involvement of other threat actors.
- Bias & Deception Risks: Potential bias in attributing all activities to ShinyHunters without considering other actors; risk of deception in the reported motivations of the group.
4. Implications and Strategic Risks
The ShinyHunters campaign could lead to increased scrutiny of digital authentication systems and drive a shift towards more secure MFA solutions. The campaign’s success may embolden other threat actors to adopt similar tactics, potentially increasing the frequency and sophistication of vishing attacks.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and practices.
- Security / Counter-Terrorism: Heightened threat environment for organizations relying on SSO and MFA systems.
- Cyber / Information Space: Increased focus on securing digital authentication processes and potential rise in cyber insurance claims.
- Economic / Social: Possible economic impact on affected companies and erosion of consumer trust in digital platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement phishing-resistant MFA solutions, enhance monitoring of SSO and MFA systems, and conduct security awareness training for employees.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing, invest in advanced threat detection technologies, and review and update incident response plans.
- Scenario Outlook:
- Best Case: Rapid adoption of secure MFA solutions mitigates the threat, and ShinyHunters’ activities are curtailed.
- Worst Case: The campaign expands, affecting more critical infrastructure and leading to significant economic and reputational damage.
- Most-Likely Scenario: Continued targeted attacks with gradual improvements in organizational defenses over time.
6. Key Individuals and Entities
- Charles Carmakal, Chief Technology Officer at Google Cloud’s Mandiant
- Rafe Pilling, CTU Threat Intel Director at Sophos
- ShinyHunters hacking collective
- Organizations affected: Crunchbase, SoundCloud, Betterment
7. Thematic Tags
cybersecurity, vishing, ShinyHunters, multi-factor authentication, data breach, extortion, digital authentication
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us