Survey Highlights Challenges for Hospital CISOs in Managing and Securing Network-Connected Medical Devices
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New Asimily Survey Reveals Hospital CISOs Struggling to See and Secure Complex Network-Connected Medical Devices
1. BLUF (Bottom Line Up Front)
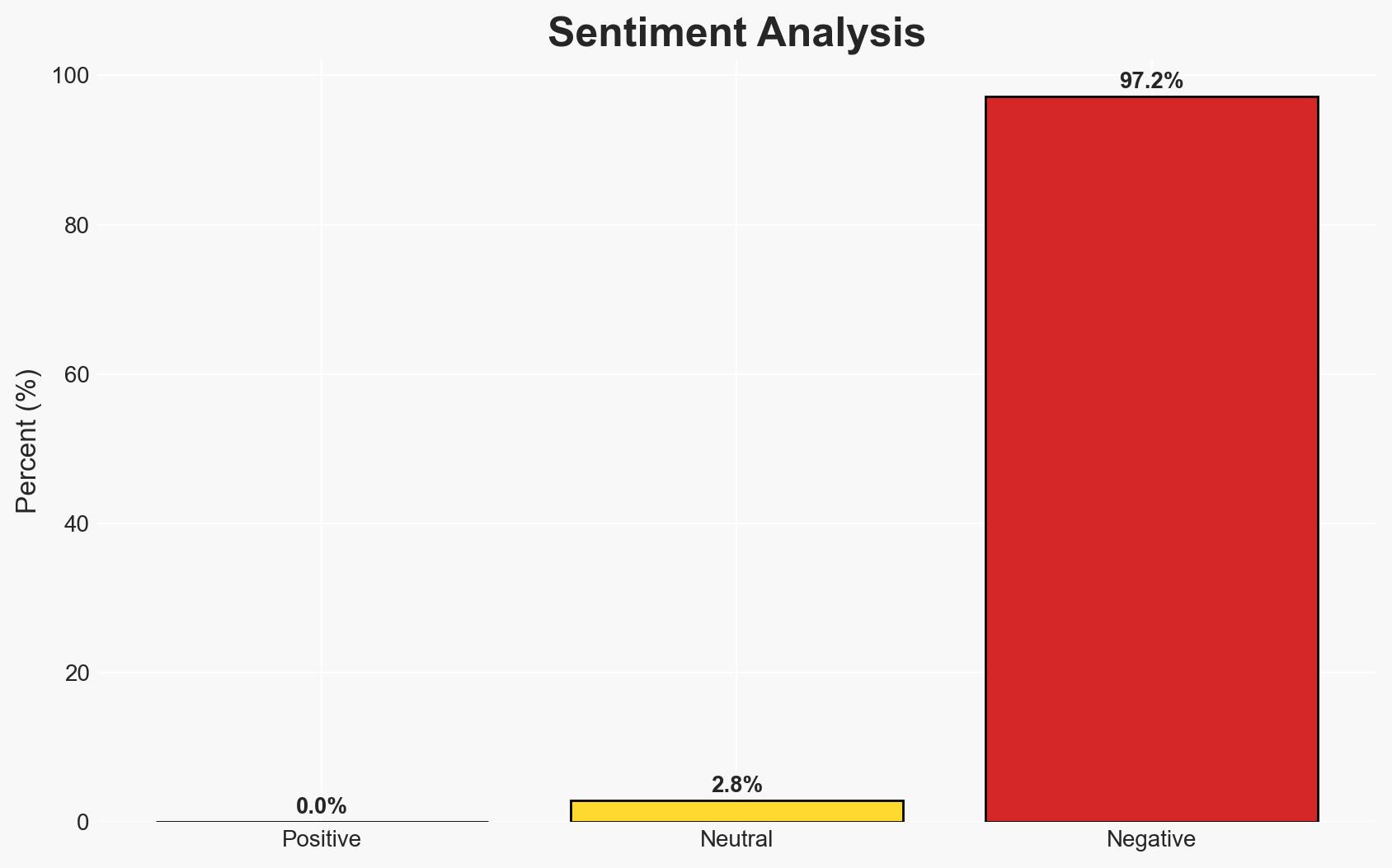
The Asimily survey highlights significant challenges faced by hospital CISOs in securing network-connected medical devices, primarily due to visibility gaps and internal process issues. This situation poses risks to operational continuity and patient care. The most likely hypothesis is that these challenges will persist without strategic changes in asset management and inter-departmental collaboration. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Hospital CISOs’ challenges in securing medical devices are primarily due to internal process breakdowns and lack of visibility. This is supported by survey data indicating that 43% of CISOs prioritize device visibility, and one-third cite internal process issues as barriers. However, the extent of these issues across different hospitals remains uncertain.
- Hypothesis B: The challenges are mainly due to external factors such as evolving cyber threats and insufficient technology solutions. While ransomware threat detection and compliance automation are concerns, the survey does not provide direct evidence that these are the primary issues.
- Assessment: Hypothesis A is currently better supported due to direct evidence from the survey regarding visibility and internal processes. Indicators such as increased cyber incidents or new technology deployments could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Hospital CISOs have adequate resources to address identified challenges; survey responses accurately reflect broader industry trends; internal process issues are resolvable with current technology.
- Information Gaps: Specific data on the effectiveness of current mitigation strategies; detailed breakdown of process issues by hospital size or type.
- Bias & Deception Risks: Potential bias in survey responses due to self-reporting; Asimily’s vested interest in promoting its platform may influence interpretation of results.
4. Implications and Strategic Risks
The persistent challenges in securing medical devices could lead to increased vulnerability to cyberattacks, impacting patient safety and hospital operations. Over time, this may necessitate regulatory changes and increased investment in cybersecurity infrastructure.
- Political / Geopolitical: Potential for increased regulatory scrutiny and policy changes affecting healthcare cybersecurity standards.
- Security / Counter-Terrorism: Elevated risk of cyberattacks targeting healthcare infrastructure, potentially exploited by malicious actors.
- Cyber / Information Space: Increased focus on developing integrated cybersecurity solutions for healthcare IoMT devices.
- Economic / Social: Financial strain on healthcare institutions to upgrade security measures; potential public concern over patient safety.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive audits of device visibility and internal processes; enhance inter-departmental communication and collaboration.
- Medium-Term Posture (1–12 months): Invest in unified cybersecurity platforms; develop training programs for staff on cybersecurity best practices.
- Scenario Outlook:
- Best Case: Improved visibility and processes lead to reduced cyber incidents.
- Worst Case: Continued challenges result in significant cyber breaches affecting patient care.
- Most Likely: Gradual improvements with ongoing challenges in visibility and process integration.
6. Key Individuals and Entities
- Shankar Somasundaram, CEO, Asimily
- Hospital CISOs (not individually identified)
7. Thematic Tags
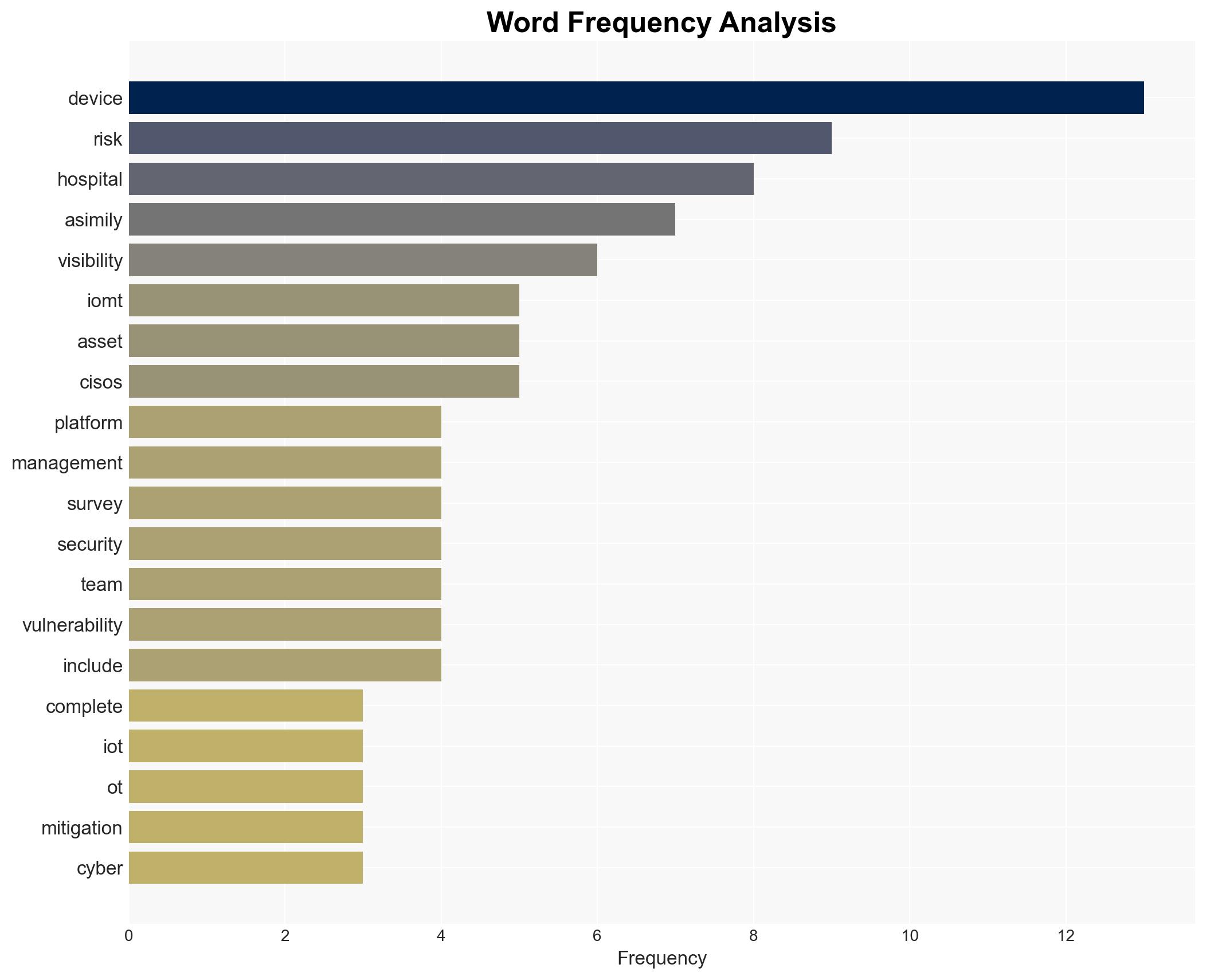
cybersecurity, healthcare, IoMT, risk management, hospital operations, device visibility, internal processes
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us