Sydney Attack Linked to ISIS Radicalization, Australian Officials Investigate Suspects’ Background
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ISIS Gunmen
1. BLUF (Bottom Line Up Front)
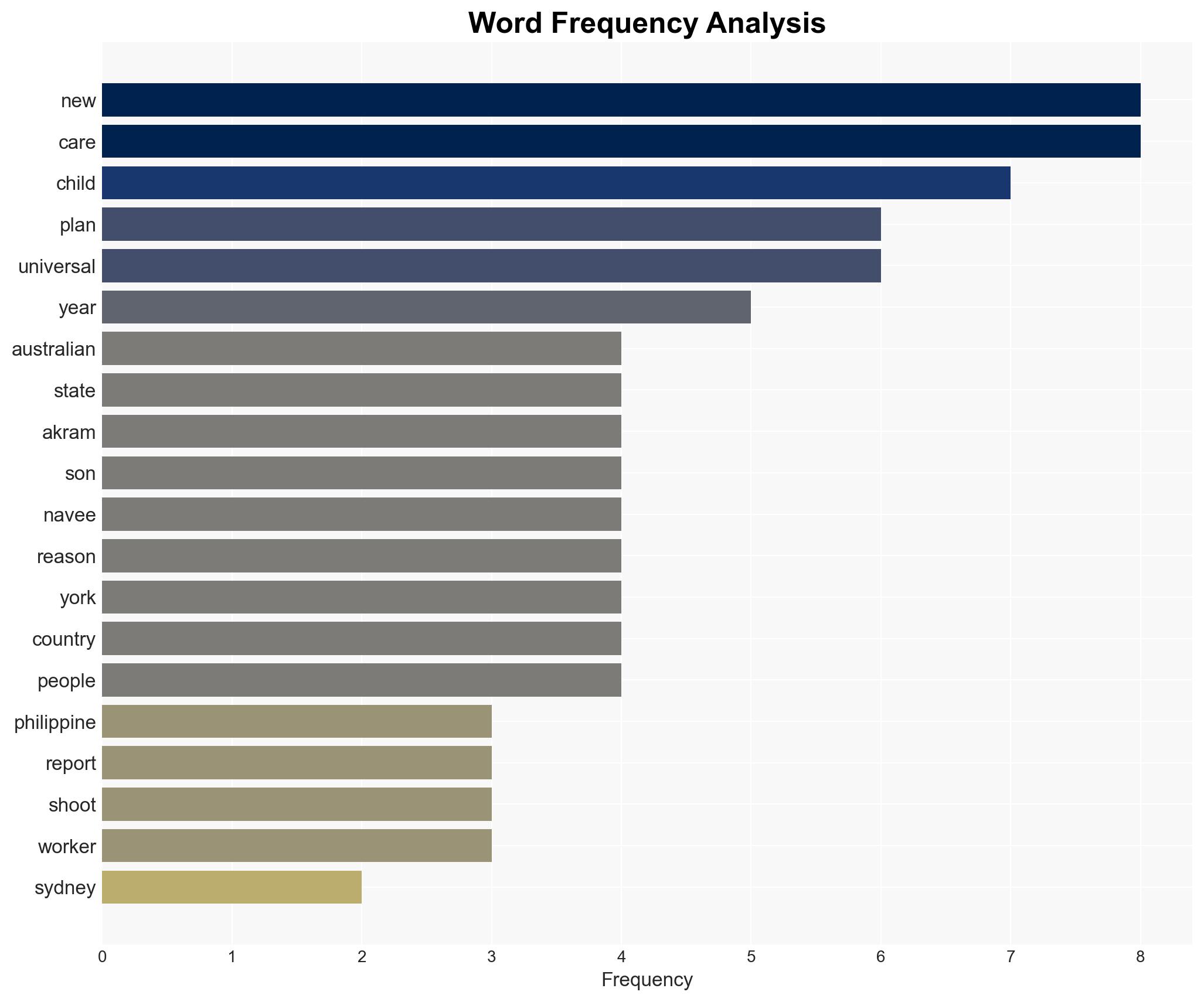
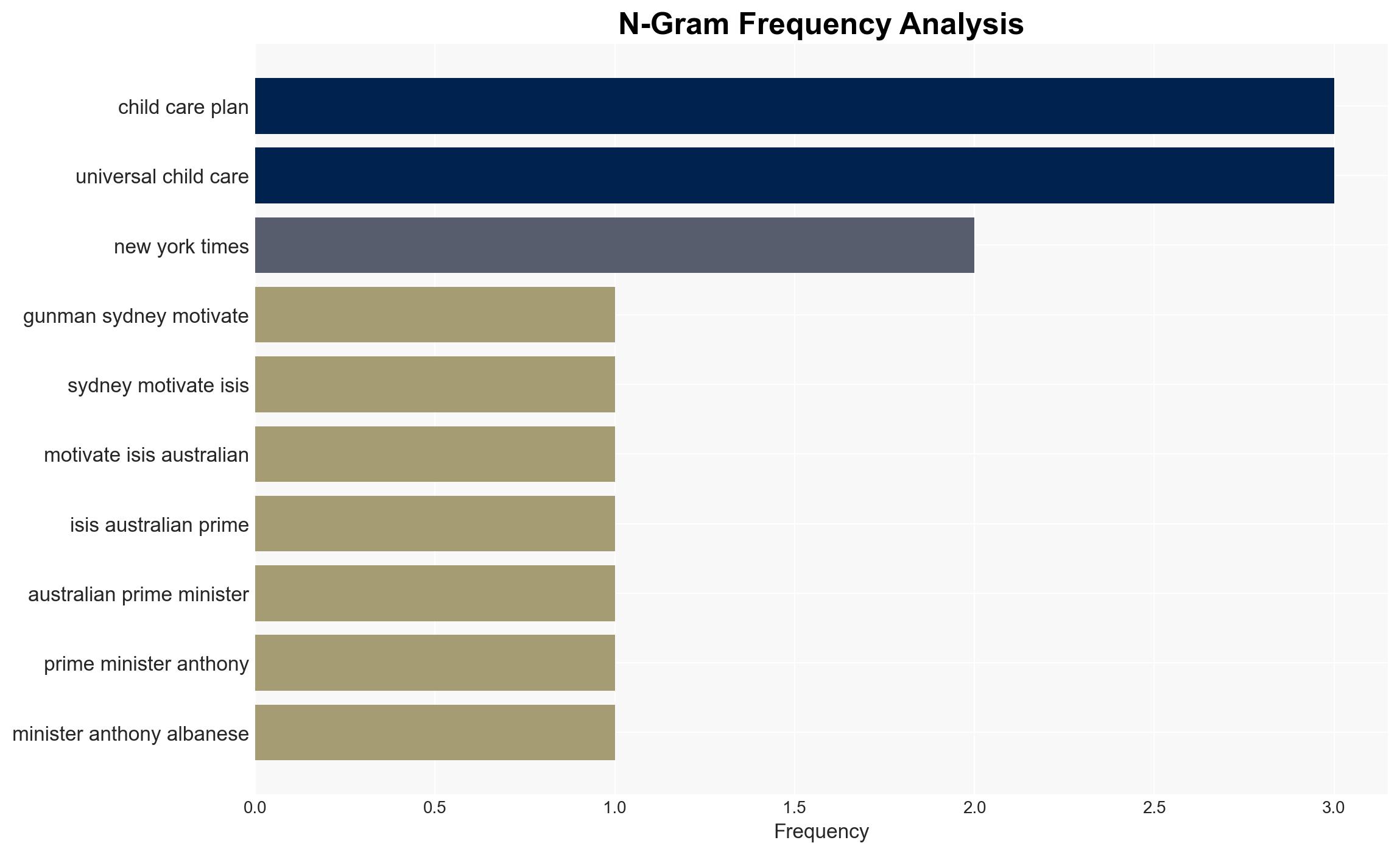
The recent attack in Sydney by gunmen motivated by ISIS highlights a significant security threat posed by radicalized individuals. The involvement of Sajid and Naveed Akram, who had connections to known ISIS operatives, underscores the potential for domestic terrorism influenced by international extremist networks. This assessment is made with moderate confidence, given the available evidence and ongoing investigations.
2. Competing Hypotheses
- Hypothesis A: The attack was directly orchestrated by ISIS, with Sajid and Naveed Akram acting as operatives following orders from the group. This is supported by their possession of ISIS flags and improvised explosive devices, but contradicted by the lack of direct communication evidence with ISIS leadership.
- Hypothesis B: The attack was independently planned by Sajid and Naveed Akram, inspired by ISIS ideology but not directly controlled by the group. This is supported by their previous connections to local ISIS sympathizers and their travel to the Philippines, a known hotspot for ISIS activity.
- Assessment: Hypothesis B is currently better supported due to the lack of direct evidence linking the attackers to ISIS command structures. Key indicators that could shift this judgment include intercepted communications or financial transactions linking them to ISIS leadership.
3. Key Assumptions and Red Flags
- Assumptions: The attackers were primarily motivated by ISIS ideology; the trip to the Philippines was related to their radicalization; local ISIS cells have limited operational capabilities.
- Information Gaps: Details on the attackers’ communications and financial transactions; the exact nature of their activities in the Philippines; potential local support networks.
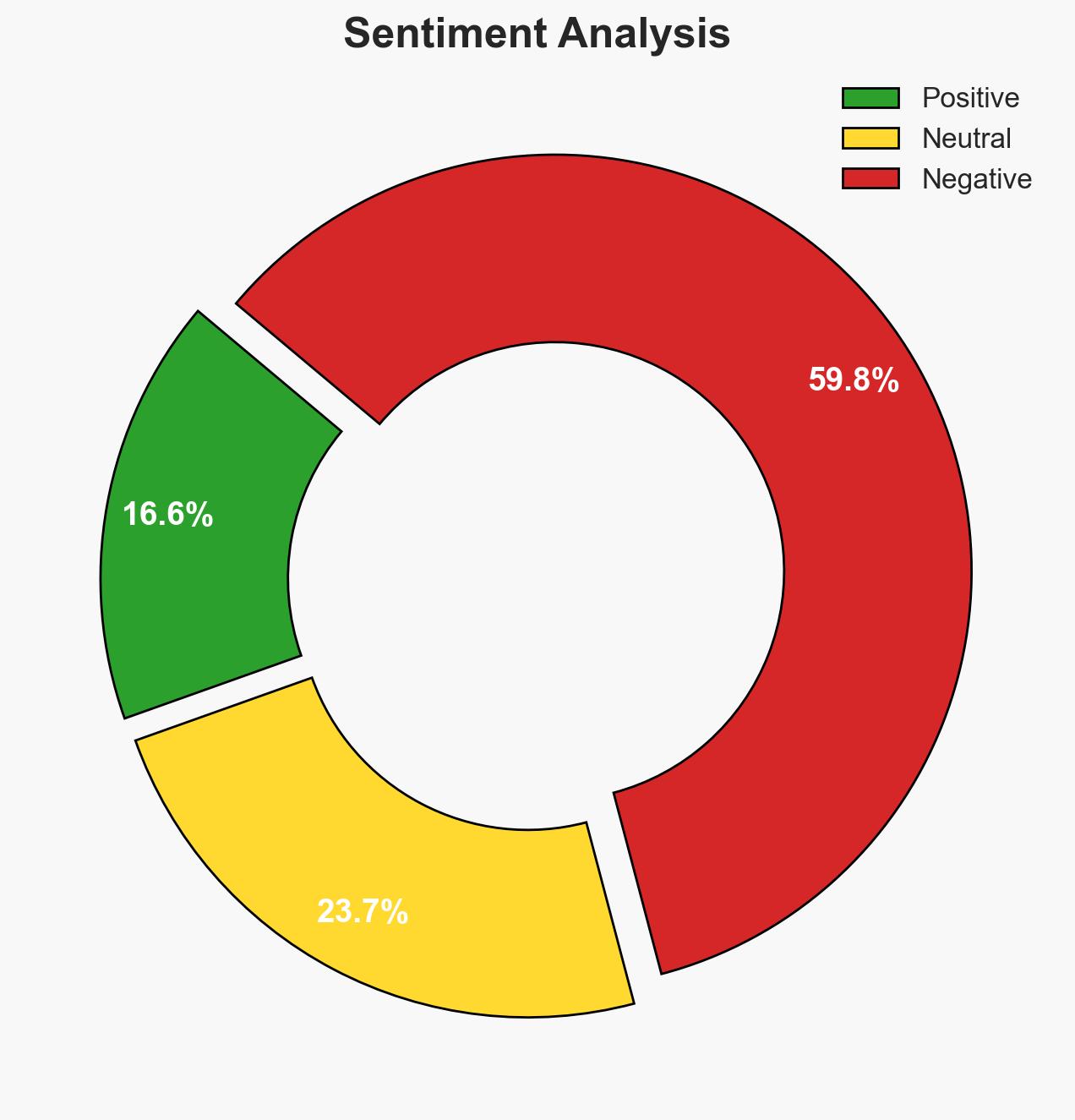
- Bias & Deception Risks: Confirmation bias in linking all Islamist attacks to ISIS; potential misinformation from sources with vested interests in exaggerating the ISIS threat.
4. Implications and Strategic Risks
This development could lead to increased domestic security measures and heightened public fear of terrorism, potentially influencing political discourse and policy. It may also embolden other radicalized individuals or groups to conduct similar attacks.
- Political / Geopolitical: Potential strain on Australia-Philippines relations; increased scrutiny on immigration and travel policies.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to monitor and disrupt potential threats.
- Cyber / Information Space: Possible increase in online radicalization efforts and propaganda dissemination by ISIS sympathizers.
- Economic / Social: Potential negative impact on tourism and community relations, particularly affecting Muslim communities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing with regional partners; increase monitoring of known radicalization hotspots; conduct community outreach to prevent backlash against Muslim communities.
- Medium-Term Posture (1–12 months): Develop resilience measures through counter-radicalization programs; strengthen partnerships with Southeast Asian countries to combat transnational terrorism.
- Scenario Outlook:
- Best: Successful disruption of local ISIS networks, reducing the threat level.
- Worst: Additional attacks inspired by this event, leading to increased casualties and societal division.
- Most-Likely: Continued isolated incidents with gradual improvements in counter-terrorism capabilities.
6. Key Individuals and Entities
- Sajid Akram
- Naveed Akram
- Isaac El Matari
- Anthony Albanese (Australian Prime Minister)
- The Philippine Bureau of Immigration
7. Thematic Tags
Counter-Terrorism, radicalization, ISIS, domestic security, international relations, Southeast Asia, community relations
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us