Syria gunman who killed U.S. troops identified as likely ISIS infiltrator, sources report
Published on: 2025-12-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Gunman in Syria who targeted US troops believed to be ISIS infiltrator sources say
1. BLUF (Bottom Line Up Front)
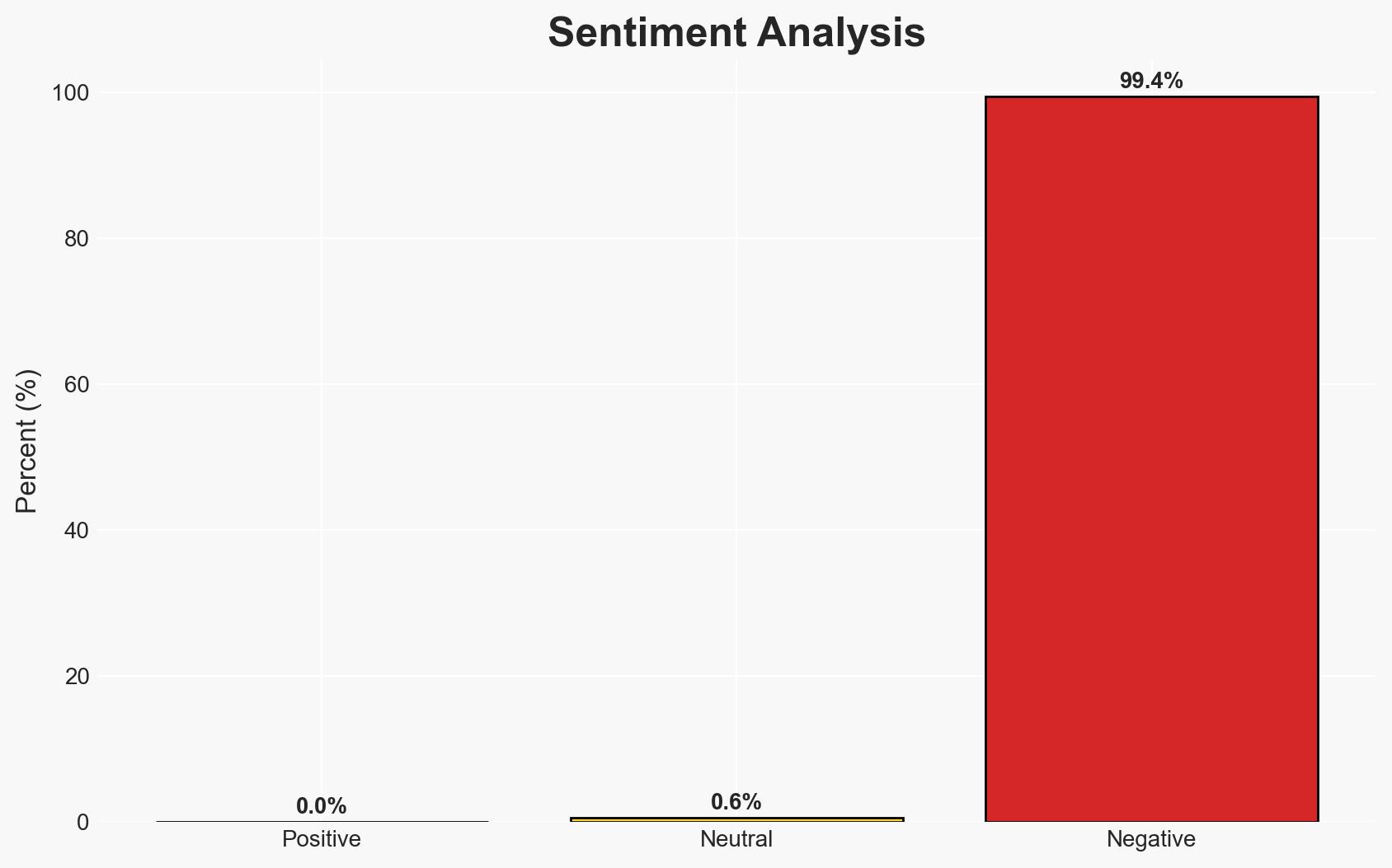
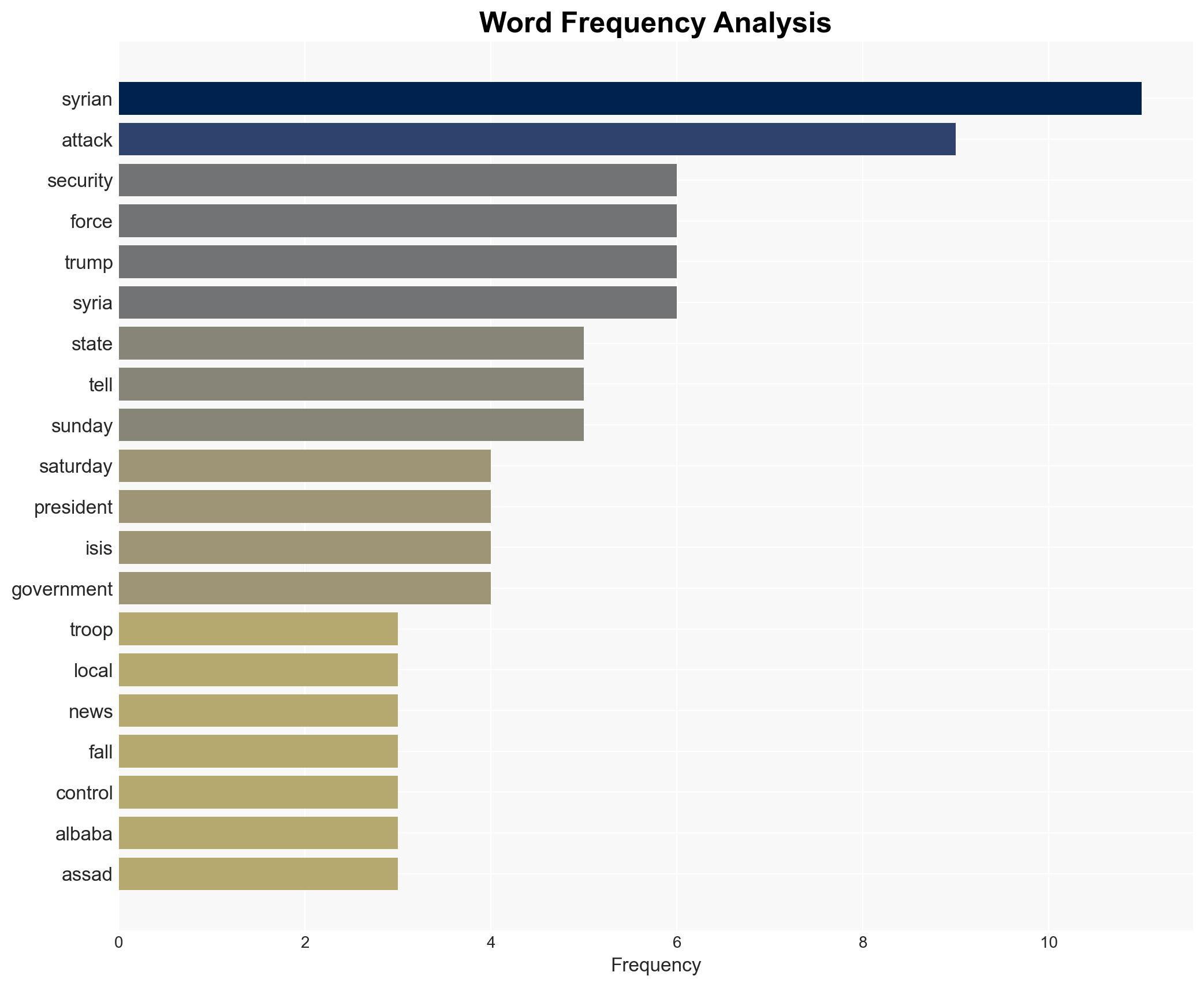
The attack on U.S. and Syrian troops near Palmyra, attributed to an ISIS infiltrator, highlights ongoing security vulnerabilities within Syrian security forces. The incident underscores the persistent threat of ISIS in the region despite territorial losses. Moderate confidence in the assessment that the attacker was an ISIS infiltrator due to corroborating reports and statements from multiple sources.
2. Competing Hypotheses
- Hypothesis A: The attacker was an ISIS infiltrator within the local security forces. This is supported by reports from CBS News and statements from Syrian officials identifying the attacker as having extremist Islamist ideas. However, the lack of a formal claim of responsibility by ISIS introduces uncertainty.
- Hypothesis B: The attack was conducted by a rogue individual with no direct ties to ISIS, exploiting existing tensions and security gaps. This is less supported due to the coordinated nature of the attack and the identification of the attacker as a risk by Syrian authorities prior to the incident.
- Assessment: Hypothesis A is currently better supported due to multiple corroborating sources and the pre-existing identification of the attacker as a security risk. Key indicators that could shift this judgment include a formal ISIS claim of responsibility or further evidence of the attacker’s affiliations.
3. Key Assumptions and Red Flags
- Assumptions: The attacker was acting under ISIS directives; the local security forces have systemic vulnerabilities; the Syrian government is committed to countering ISIS.
- Information Gaps: Direct evidence of the attacker’s communication with ISIS; detailed background on the attacker’s recruitment and infiltration process.
- Bias & Deception Risks: Potential source bias from Syrian officials aiming to deflect blame; risk of cognitive bias in interpreting the attack as solely ISIS-driven without considering other motives.
4. Implications and Strategic Risks
This development could exacerbate tensions between U.S. and Syrian forces and complicate coalition efforts against ISIS. It may also embolden ISIS elements to exploit similar vulnerabilities.
- Political / Geopolitical: Increased strain on U.S.-Syrian relations; potential for retaliatory actions impacting regional stability.
- Security / Counter-Terrorism: Heightened threat environment for coalition forces; potential for similar insider attacks.
- Cyber / Information Space: Potential for ISIS to leverage the incident in propaganda to recruit or radicalize sympathizers.
- Economic / Social: Possible destabilization of local economies due to increased military activity and security measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance vetting and monitoring of local security forces; increase intelligence-sharing with Syrian counterparts; conduct a security audit of coalition bases.
- Medium-Term Posture (1–12 months): Develop resilience measures against insider threats; strengthen partnerships with regional allies to counter ISIS influence.
- Scenario Outlook:
- Best: Successful mitigation of insider threats leading to reduced ISIS influence.
- Worst: Escalation of attacks leading to broader regional instability.
- Most-Likely: Continued sporadic attacks with gradual improvements in security protocols.
6. Key Individuals and Entities
- Tarek Satouf al-Hamd (alleged attacker)
- President Ahmed al-Sharaa (Syrian President)
- Secretary of State Marco Rubio
- Foreign Minister Asaad al-Shaibani
- Noureddine al-Baba (Syrian Interior Ministry spokesman)
- Joe Kent (Director of the National Counterterrorism Center)
7. Thematic Tags
Counter-Terrorism, ISIS, insider threat, U.S.-Syria relations, regional security, military operations, intelligence sharing
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us