TARmageddon flaw in Async-Tar Rust library allows to smuggle extra archives when the library is processing nested TAR files – Securityaffairs.com
Published on: 2025-10-22
Intelligence Report: TARmageddon flaw in Async-Tar Rust library allows to smuggle extra archives when the library is processing nested TAR files – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
The TARmageddon vulnerability in the Async-Tar Rust library presents a significant cybersecurity risk, particularly in supply chain contexts. The most supported hypothesis is that this flaw could be exploited by malicious actors to introduce undetected files into systems, potentially leading to remote code execution (RCE). Confidence level: High. Recommended action: Immediate patching of affected systems and increased vigilance in monitoring supply chain components.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is primarily a result of a logic flaw in the handling of PAX and USTAR headers, which can be exploited to smuggle additional files into a system, leading to potential RCE.
Hypothesis 2: The vulnerability is overstated and primarily a theoretical risk, with limited practical applicability due to existing security measures in place that can detect and mitigate such exploits.
Structured Analytic Technique: Analysis of Competing Hypotheses (ACH) was used. Evidence strongly supports Hypothesis 1 due to the detailed description of the exploit mechanism and potential attack scenarios provided in the source. Hypothesis 2 is less supported due to the lack of evidence of existing measures effectively countering this specific flaw.
3. Key Assumptions and Red Flags
Assumptions:
– The vulnerability can be exploited as described without significant barriers.
– Current security measures are insufficient to detect this specific type of exploit.
Red Flags:
– Lack of detailed evidence on the prevalence of exploitation in the wild.
– Potential bias towards emphasizing the severity of the vulnerability for attention.
Blind Spots:
– The report does not address potential mitigations already in place or the speed of patch deployment.
4. Implications and Strategic Risks
The vulnerability poses a risk to software supply chains, potentially allowing attackers to introduce malicious code into trusted environments. This could lead to widespread RCE incidents, affecting critical infrastructure and sensitive data. The economic impact could be significant if exploited at scale, leading to loss of trust in affected software components and increased costs for remediation.
5. Recommendations and Outlook
- Immediate patching of affected Async-Tar library versions.
- Enhanced monitoring of software supply chains for anomalous activities.
- Scenario-based projections:
- Best Case: Rapid patch deployment mitigates the risk with minimal impact.
- Worst Case: Exploitation leads to widespread RCE incidents, causing significant economic and reputational damage.
- Most Likely: Moderate exploitation occurs, prompting increased security measures and patching efforts.
6. Key Individuals and Entities
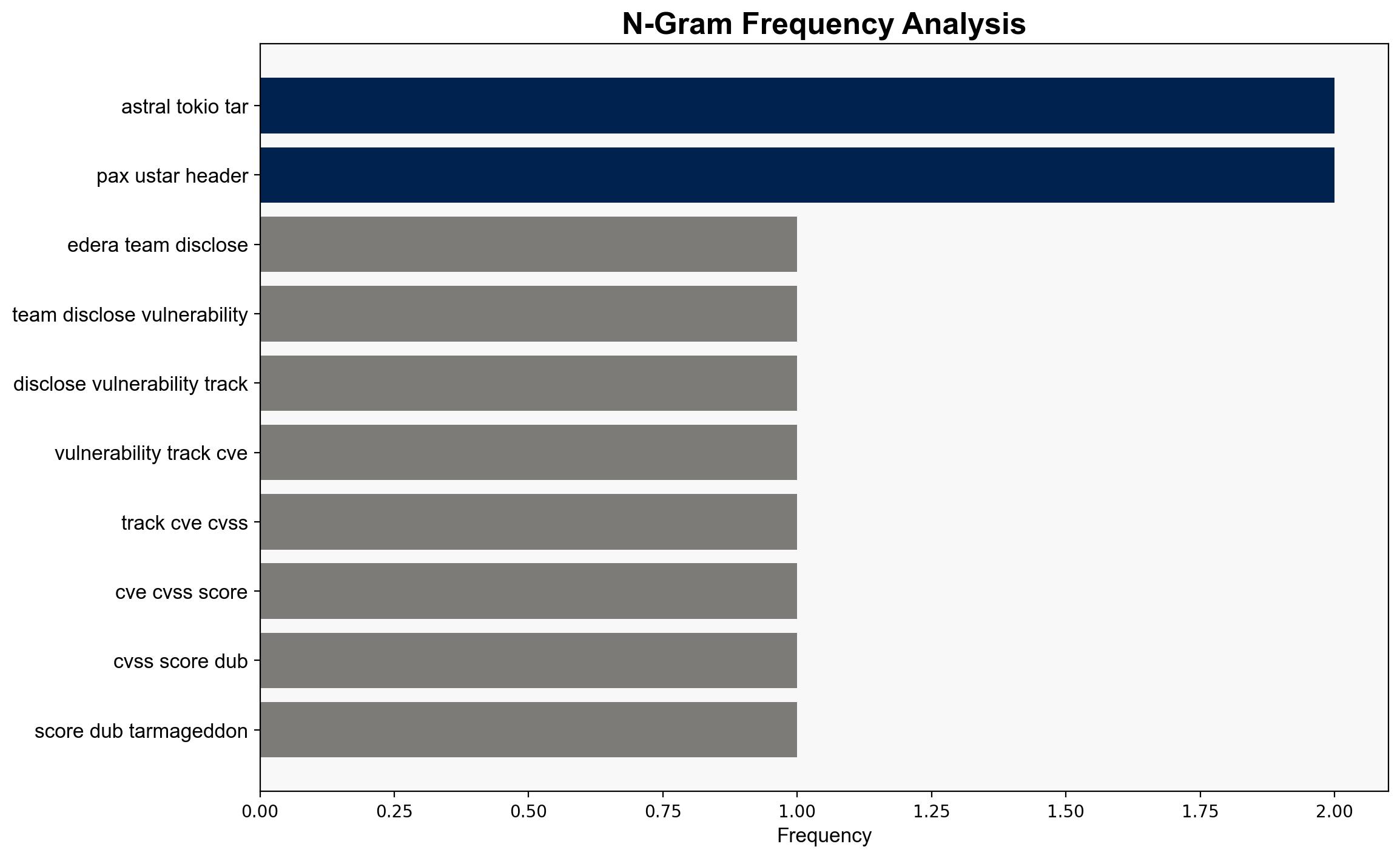
– Edera team: Disclosed the vulnerability.
– Astral: Involved in the development of the affected library versions.
7. Thematic Tags
national security threats, cybersecurity, software supply chain, vulnerability management