Technological Solutions Needed to Combat Rising Violence and Abductions in Nigeria
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
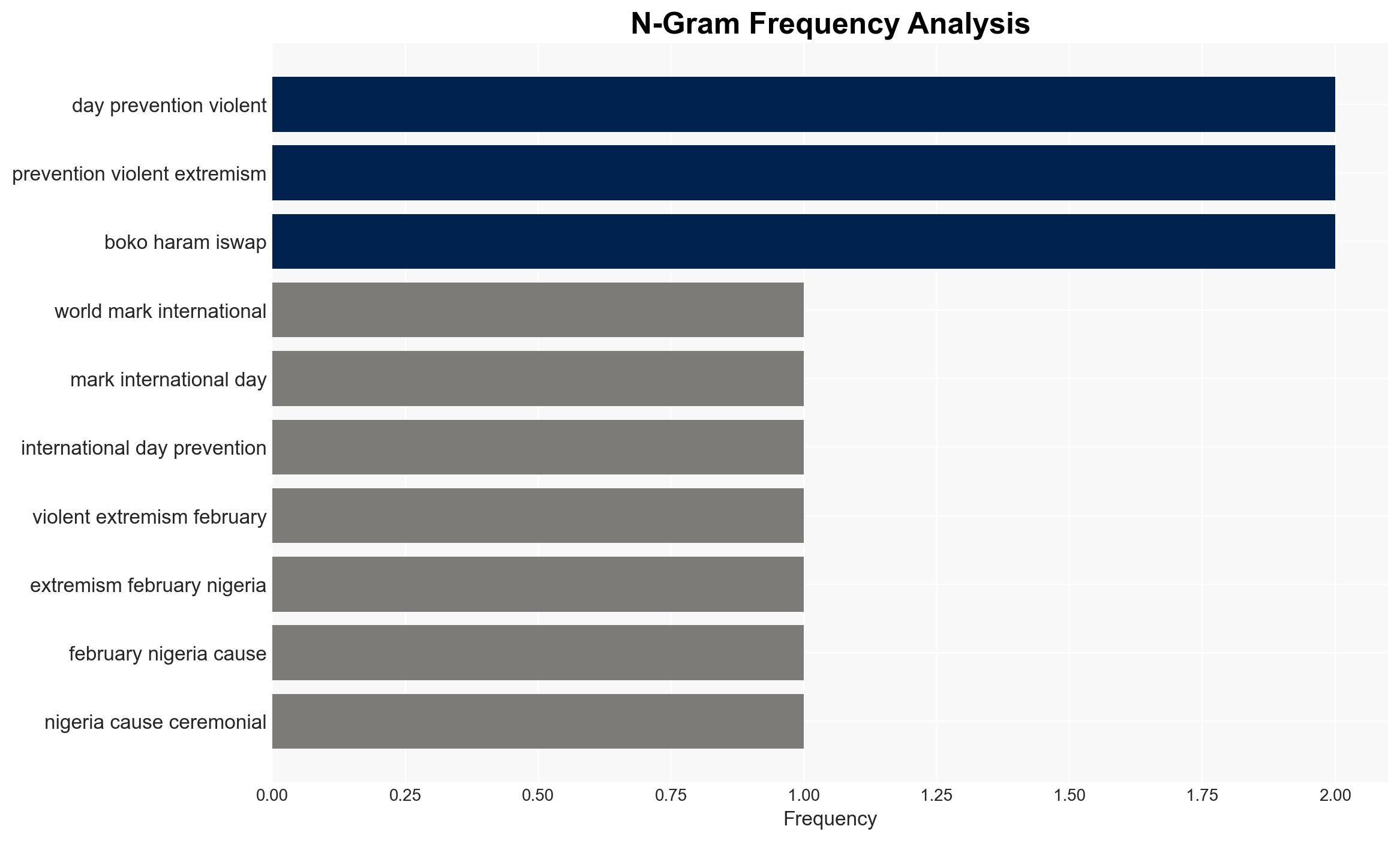
Intelligence Report: PVE Day 2026 Tech is the game changer
1. BLUF (Bottom Line Up Front)
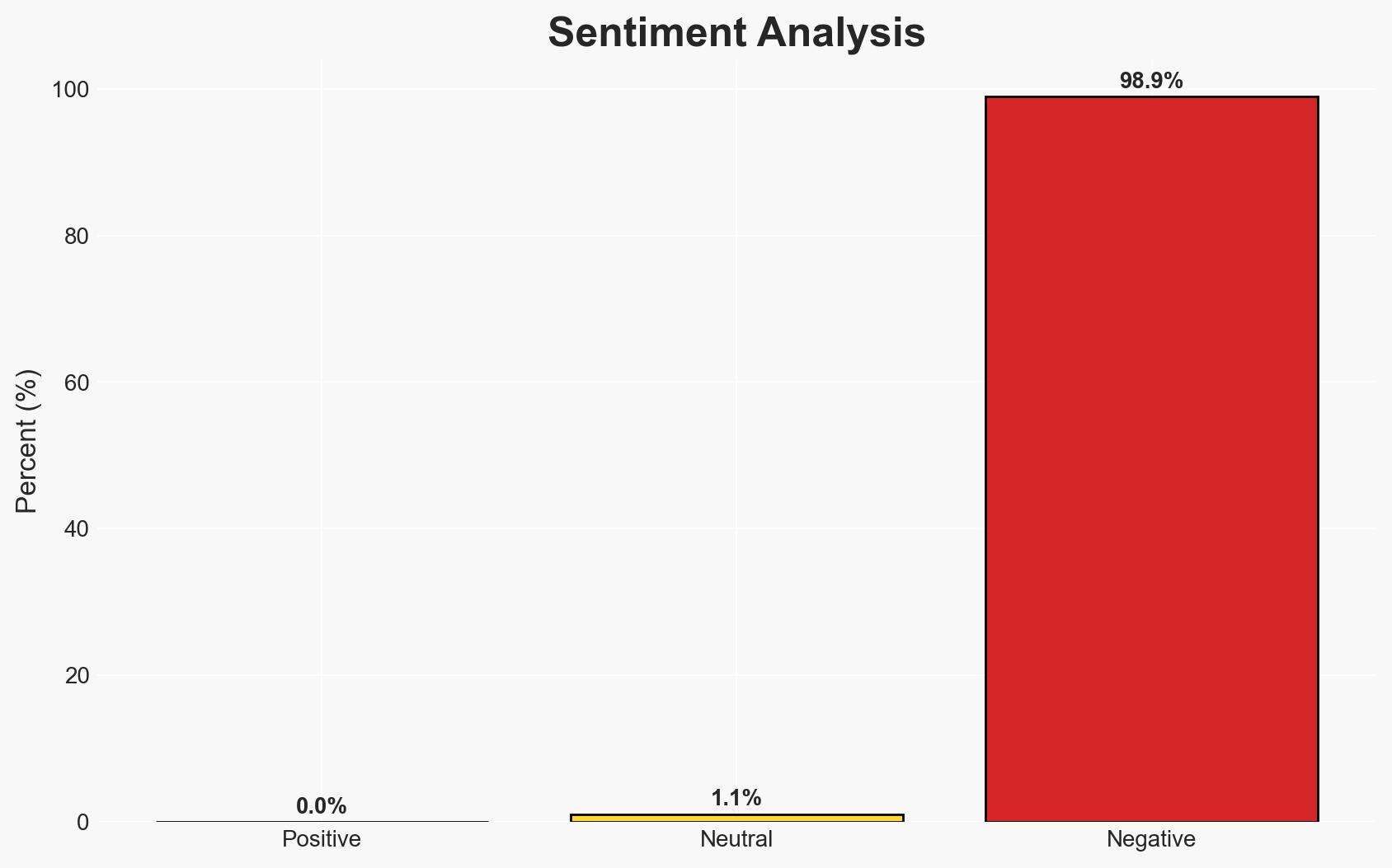
The escalation of violent extremism in Nigeria, marked by widespread kidnappings and attacks, underscores the urgent need for technological interventions to enhance security. The most likely hypothesis is that non-state actors are exploiting weak state responses, with moderate confidence in this assessment. This situation affects Nigerian civilians, particularly in the northern and central regions, and poses a significant threat to national stability.
2. Competing Hypotheses
- Hypothesis A: The increase in violence is primarily due to the strategic expansion of non-state actors seeking territorial control and financial gain through ransom. This is supported by the pattern of attacks and the ineffective state responses. Key uncertainties include the internal dynamics of these groups and their external support networks.
- Hypothesis B: The violence is a reaction to socio-economic grievances and government failures, with groups exploiting these conditions to gain local support. While socio-economic issues are evident, the organized nature of the attacks suggests a more strategic intent.
- Assessment: Hypothesis A is currently better supported due to the organized and widespread nature of the attacks, indicating a strategic expansion rather than spontaneous reactions to socio-economic conditions. Indicators such as changes in attack patterns or new alliances could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The state lacks the capability to effectively counter non-state actors; non-state actors are primarily motivated by financial and territorial gains; current peace deals are ineffective.
- Information Gaps: Detailed intelligence on the leadership and operational capabilities of non-state actors; the extent of local support for these groups.
- Bias & Deception Risks: Potential bias in local reporting; government statements may downplay the severity of the situation; non-state actors may exaggerate their capabilities.
4. Implications and Strategic Risks
The continuation of violence could lead to further destabilization, impacting regional security and economic conditions. The state’s inability to manage the threat may embolden non-state actors and erode public trust.
- Political / Geopolitical: Potential for increased foreign intervention or support for the Nigerian government; regional instability could affect neighboring countries.
- Security / Counter-Terrorism: Escalation in attacks could overwhelm security forces, necessitating international assistance.
- Cyber / Information Space: Potential for increased use of digital platforms by non-state actors for recruitment and propaganda.
- Economic / Social: Displacement of populations, disruption of agriculture, and increased poverty could exacerbate social tensions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing mechanisms; deploy technology for surveillance and monitoring; increase community engagement to gather local intelligence.
- Medium-Term Posture (1–12 months): Develop resilience measures such as community policing; strengthen regional partnerships for coordinated responses; invest in technology-driven security solutions.
- Scenario Outlook:
- Best: Successful implementation of technology and international support reduces violence.
- Worst: Violence escalates, leading to widespread instability and humanitarian crises.
- Most-Likely: Continued sporadic violence with gradual improvements in security through technological interventions.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
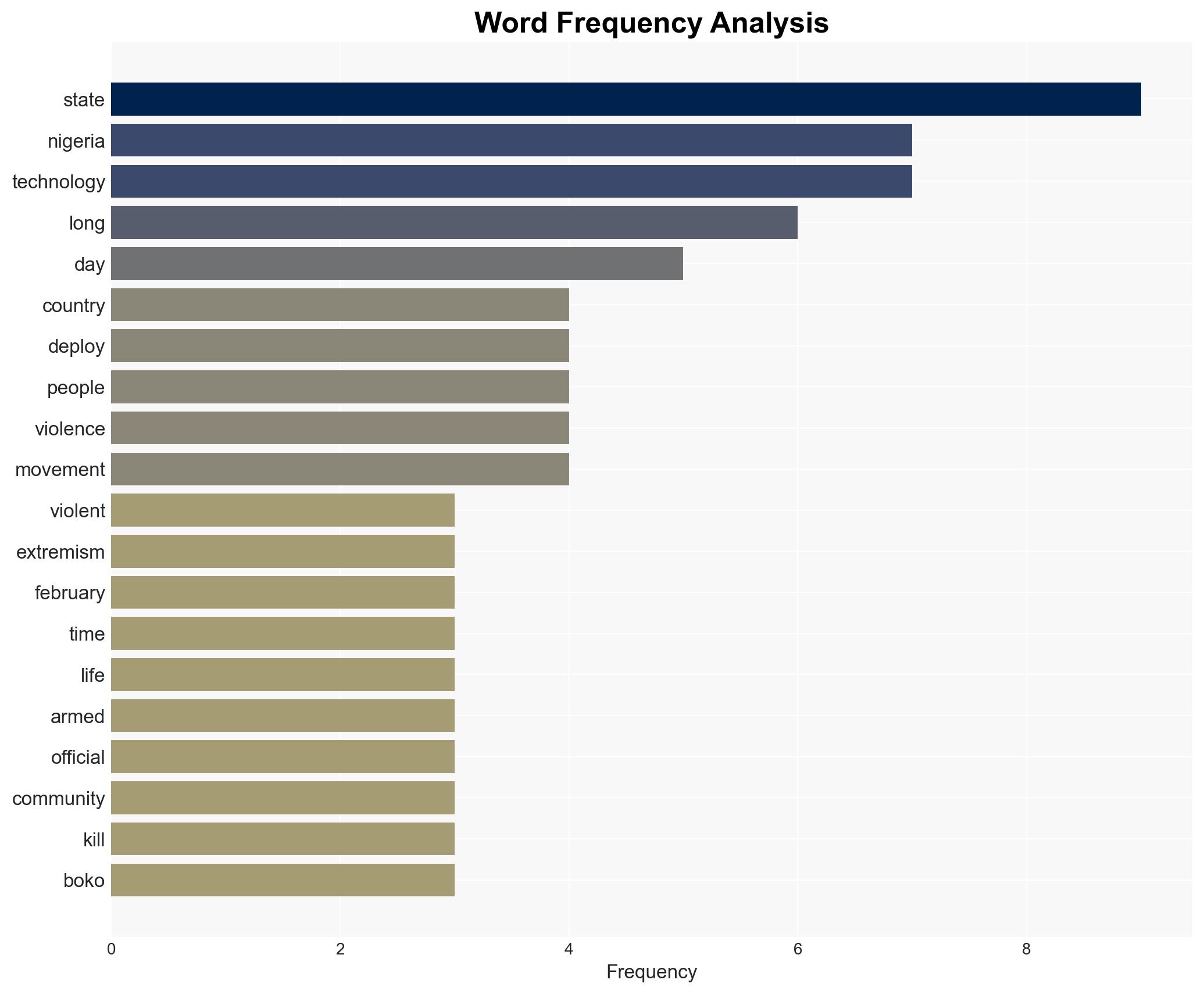
Counter-Terrorism, violent extremism, Nigeria security, non-state actors, technology in security, regional stability, socio-economic impact
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us