The Best Crypto Apps for Android A 2025 Guide to Trading and Managing Your Portfolio – Android Headlines
Published on: 2025-11-03
Intelligence Report: The Best Crypto Apps for Android A 2025 Guide to Trading and Managing Your Portfolio – Android Headlines
1. BLUF (Bottom Line Up Front)
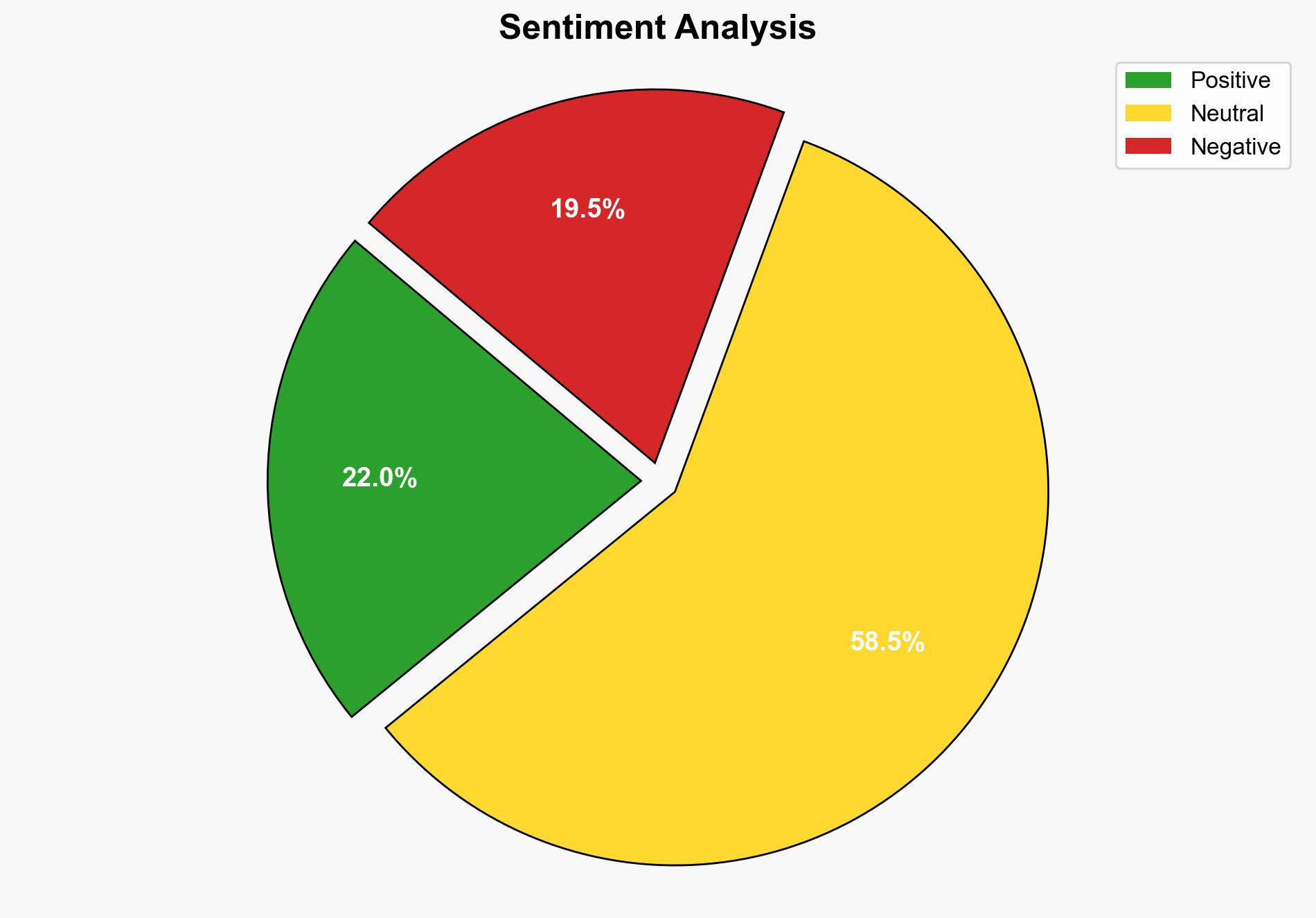
The report’s analysis suggests that the security measures implemented by Android Headlines, possibly using Cloudflare, are causing access issues to their content, potentially impacting their user engagement and information dissemination. The most supported hypothesis is that these security measures are overly restrictive, leading to unintended access blocks. Confidence level: Moderate. Recommended action: Review and optimize security protocols to balance protection and accessibility.
2. Competing Hypotheses
Hypothesis 1: The access issues are primarily due to overly aggressive security settings by Cloudflare, leading to legitimate users being blocked inadvertently.
Hypothesis 2: The access issues are a result of targeted cyber-attacks, prompting Android Headlines to implement stringent security measures, inadvertently affecting legitimate access.
3. Key Assumptions and Red Flags
– **Assumptions:**
– Hypothesis 1 assumes that the security settings are not fine-tuned for user access patterns.
– Hypothesis 2 assumes a credible threat level necessitating heightened security.
– **Red Flags:**
– Lack of direct evidence of cyber-attacks.
– Repeated mentions of “malformed data” and “SQL commands” suggest potential misconfiguration rather than external threats.
4. Implications and Strategic Risks
– **Economic:** Reduced user access can lead to decreased ad revenue and user engagement.
– **Cyber:** Over-reliance on automated security solutions without manual oversight can lead to service disruptions.
– **Geopolitical:** None directly identified.
– **Psychological:** User frustration due to access issues may harm brand reputation.
5. Recommendations and Outlook
- Conduct a comprehensive review of security protocols to ensure they are not overly restrictive.
- Implement a feedback loop for users to report access issues easily.
- Scenario Projections:
- Best Case: Optimized security settings restore full access without compromising security.
- Worst Case: Continued access issues lead to significant user attrition and reputational damage.
- Most Likely: Incremental adjustments improve access, but some issues persist.
6. Key Individuals and Entities
– Cloudflare (as the security service provider)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus