The browser is eating your security stack – Help Net Security
Published on: 2025-11-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The browser is eating your security stack – Help Net Security
1. BLUF (Bottom Line Up Front)
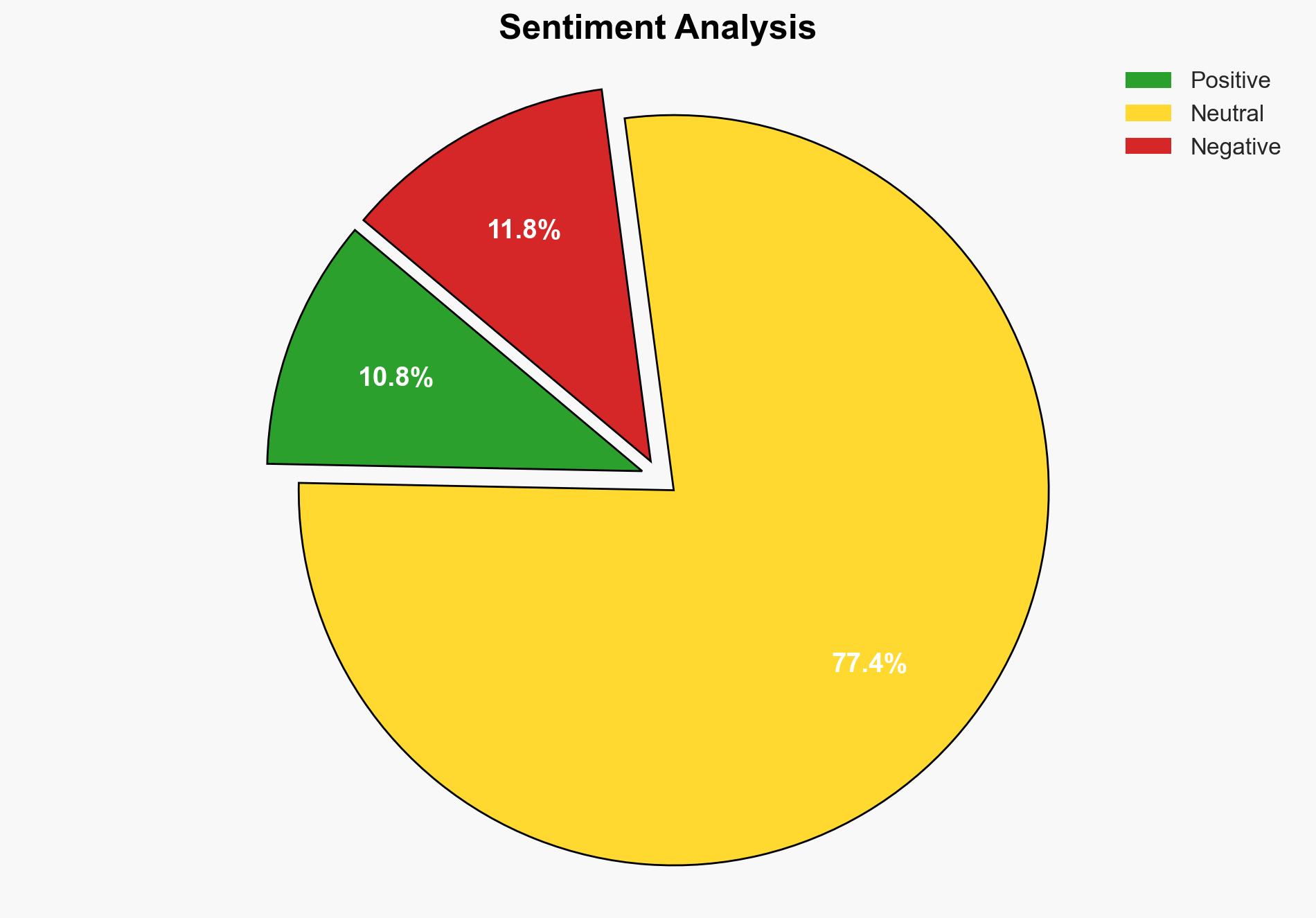
There is a significant risk that enterprise data security is being compromised through browser-based activities, particularly due to the use of unmanaged browsers and AI tools. The most supported hypothesis is that the lack of visibility and control over browser activities is leading to data leaks and identity theft. Recommended actions include enhancing browser security controls and increasing employee awareness of secure data handling practices. Confidence Level: Moderate.
2. Competing Hypotheses
Hypothesis 1: The primary threat to enterprise data security stems from unmanaged browser activities and extensions that bypass existing security controls, leading to data leaks and identity theft.
Hypothesis 2: The integration of AI tools and SaaS platforms into browsers is the main driver of security vulnerabilities, as these tools often operate outside of enterprise oversight and can inadvertently expose sensitive data.
Hypothesis 1 is more likely due to the widespread use of unmanaged browsers and extensions, which provide numerous entry points for data breaches. The evidence suggests that browser extensions and personal account usage are significant factors in security lapses.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that enterprises lack sufficient visibility into browser activities and that employees frequently use personal accounts for work-related tasks.
Red Flags: The rapid adoption of AI tools without adequate governance and the potential for browser extensions to be compromised are significant concerns.
Deception Indicators: There is a risk of underestimating the sophistication of attackers who may exploit these vulnerabilities through seemingly benign browser extensions.
4. Implications and Strategic Risks
The primary risk is the potential for large-scale data breaches resulting from browser-based vulnerabilities. This could lead to significant financial losses, reputational damage, and regulatory penalties. The integration of AI tools without proper oversight exacerbates these risks, as sensitive data may be inadvertently exposed or misused. Additionally, the lack of centralized control over browser activities increases the attack surface for cyber threats.
5. Recommendations and Outlook
- Actionable Steps: Implement stricter browser security policies, including the use of managed browsers and restrictions on browser extensions. Increase employee training on secure data handling practices and the risks associated with AI tools.
- Best Scenario: Enterprises successfully implement enhanced browser security measures, reducing the risk of data breaches and improving overall cybersecurity posture.
- Worst Scenario: Continued neglect of browser security leads to a major data breach, resulting in severe financial and reputational damage.
- Most-likely Scenario: Incremental improvements in browser security are made, but vulnerabilities persist due to the rapid evolution of AI tools and employee behavior.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Key entities include enterprises using SaaS platforms and AI tools, browser developers, and cybersecurity teams.
7. Thematic Tags
Cybersecurity, Data Security, Browser Security, AI Tools, SaaS Platforms
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology