The Challenges of Relying on Disparate Security Solutions in a Rapidly Evolving Cyber Threat Landscape
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New Microsoft e-book 3 reasons point solutions are holding you back
1. BLUF (Bottom Line Up Front)
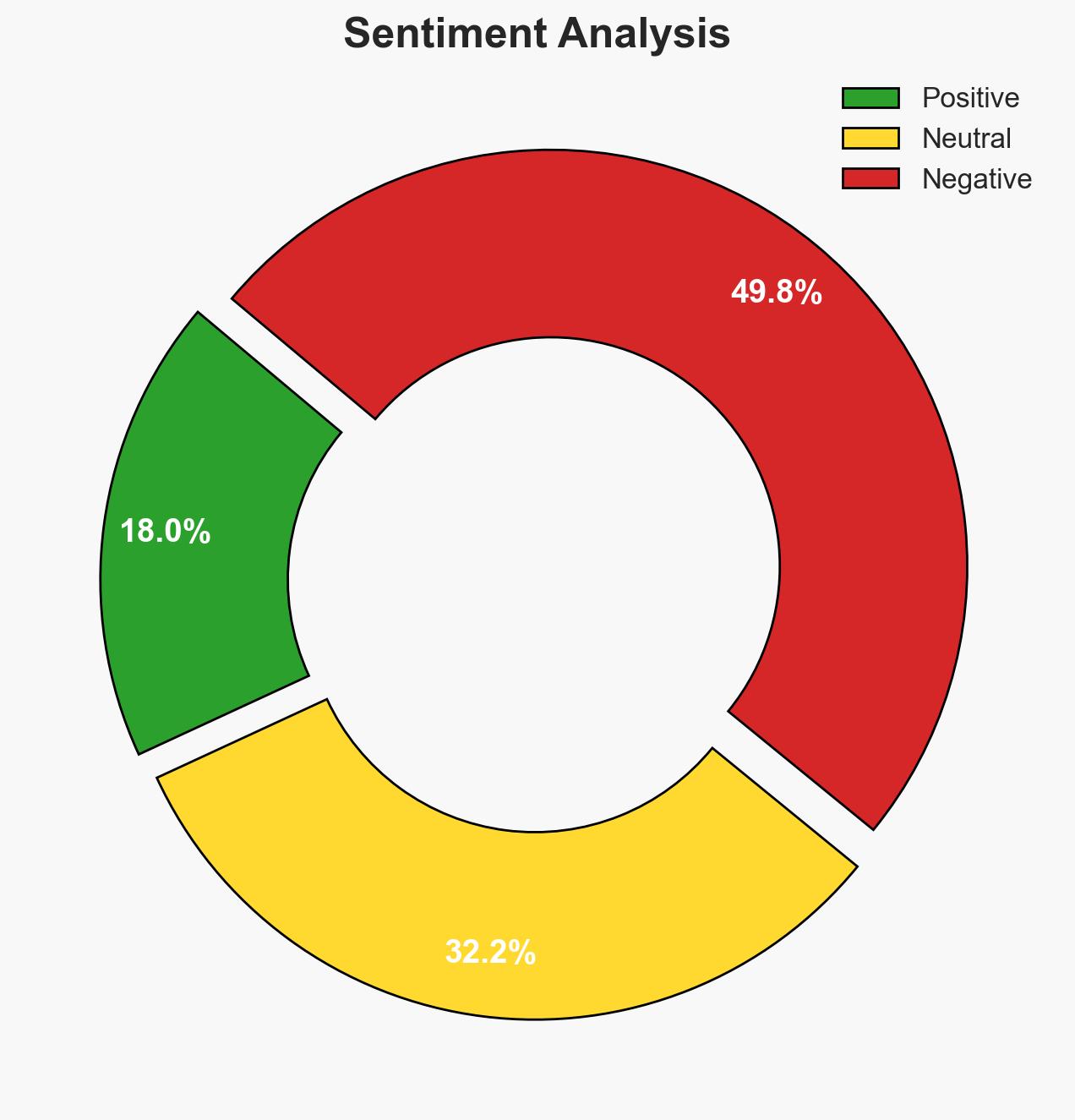
The Microsoft e-book argues that fragmented cybersecurity tools hinder effective threat detection and response, advocating for a unified, AI-ready security platform. This approach is likely to improve organizational resilience against cyber threats by enhancing visibility and predictive capabilities. The assessment holds moderate confidence, as it is based on general trends in cybersecurity and the potential benefits of integrated systems.
2. Competing Hypotheses
- Hypothesis A: Fragmented security tools significantly impede organizational cybersecurity effectiveness. Evidence includes increased operational costs and reduced AI efficacy due to lack of unified data. However, the extent of these impacts across different organizations remains uncertain.
- Hypothesis B: Organizations can maintain effective cybersecurity with fragmented tools through strategic integration and manual processes. This is supported by the existence of successful security operations using diverse tools, though it may require more resources and expertise.
- Assessment: Hypothesis A is currently better supported due to the documented challenges of managing disparate systems and the potential efficiency gains from unified platforms. Indicators such as increased breach incidents or cost inefficiencies could further support this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations face increasing cyber threats; unified platforms inherently improve security; AI integration is beneficial.
- Information Gaps: Specific case studies or metrics demonstrating the impact of unified vs. fragmented tools on security outcomes.
- Bias & Deception Risks: Potential bias from Microsoft as a vendor promoting its own solutions; lack of independent verification of claims.
4. Implications and Strategic Risks
The shift towards unified security platforms could redefine cybersecurity strategies, influencing resource allocation and organizational structures.
- Political / Geopolitical: Potential for increased regulatory scrutiny on cybersecurity practices and vendor influence.
- Security / Counter-Terrorism: Enhanced detection and response capabilities could reduce the success rate of cyber-attacks.
- Cyber / Information Space: Greater reliance on AI and data integration may increase vulnerability to sophisticated cyber threats.
- Economic / Social: Organizations may face initial costs for transitioning to unified platforms, impacting budgets and potentially leading to workforce changes.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Evaluate current cybersecurity toolsets for integration opportunities; initiate discussions with vendors about unified solutions.
- Medium-Term Posture (1–12 months): Develop a roadmap for transitioning to a unified platform; invest in AI and data analytics capabilities.
- Scenario Outlook: Best: Enhanced security posture and reduced breach incidents; Worst: High transition costs with minimal security improvement; Most-Likely: Gradual improvement in security efficiency and effectiveness.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
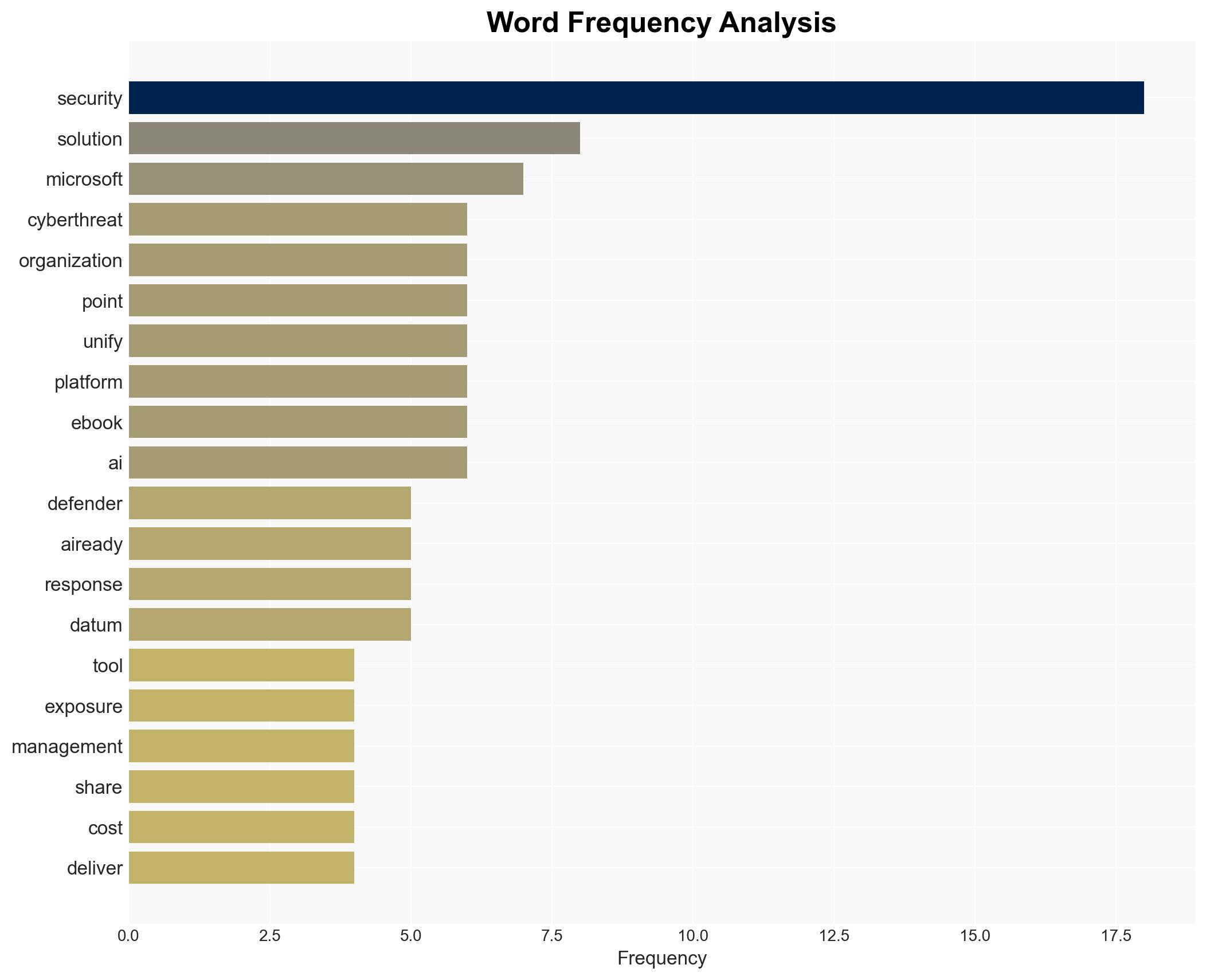
cybersecurity, AI integration, threat detection, security platforms, operational efficiency, digital transformation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us