The confidence trap holding security back – Help Net Security
Published on: 2025-11-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the “confidence trap” in cybersecurity is primarily due to a misalignment between perceived readiness and actual capability, exacerbated by outdated training and metrics. Confidence Level: Moderate. Recommended action includes restructuring training programs to focus on current threats and improving metrics to better reflect true readiness.
2. Competing Hypotheses
Hypothesis 1: The confidence trap is a result of outdated training and metrics that do not accurately reflect current threat landscapes, leading to a false sense of security.
Hypothesis 2: The confidence trap stems from organizational culture and communication barriers that prevent accurate assessment and reporting of cybersecurity capabilities.
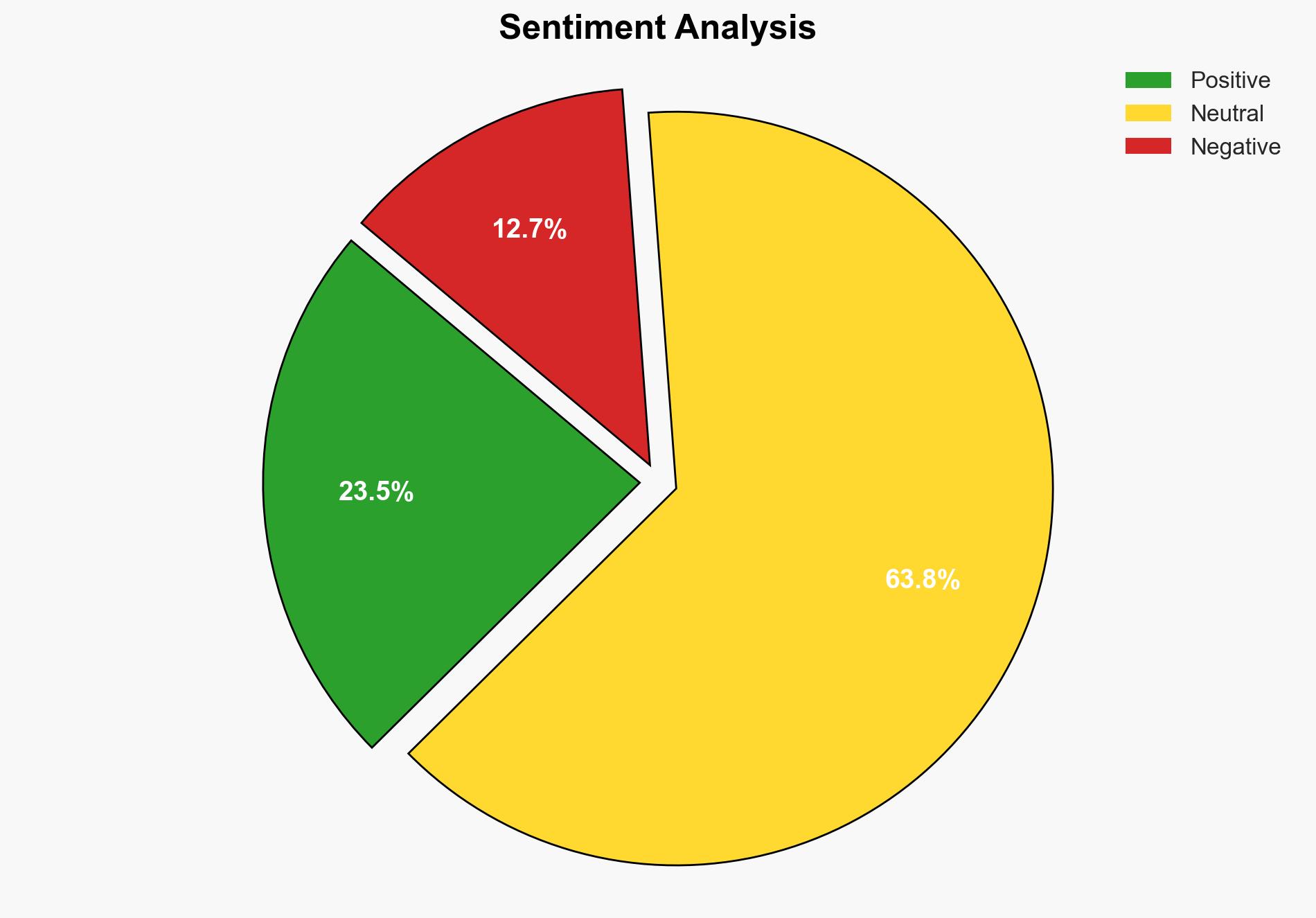
Assessment: Hypothesis 1 is more likely due to evidence indicating that training focuses on familiar threats and outdated scenarios, while metrics emphasize participation over performance. This aligns with the report’s findings that confidence rises while actual performance remains stagnant.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that training and metrics are the primary drivers of the confidence trap. There is an assumption that all relevant data has been accurately reported and interpreted.
Red Flags: Over-reliance on participation metrics as indicators of readiness. Potential bias in self-reported data from security teams. Lack of evidence showing improvement in response times and decision-making accuracy.
4. Implications and Strategic Risks
The confidence trap could lead to significant strategic risks, including increased vulnerability to advanced cyber threats, particularly AI-driven attacks. This misalignment between perceived and actual readiness could result in inadequate response to incidents, causing reputational damage, financial loss, and potential regulatory penalties. The gap in preparedness could also escalate into broader organizational risks, affecting legal, communication, and leadership functions.
5. Recommendations and Outlook
- Actionable Steps: Revise training programs to incorporate current and emerging threats, including AI-driven scenarios. Develop metrics that assess performance under pressure rather than mere participation.
- Best Scenario: Organizations successfully realign training and metrics, leading to improved readiness and reduced vulnerability to cyber threats.
- Worst Scenario: Continued reliance on outdated practices results in a major cyber incident, causing significant operational and reputational damage.
- Most-likely Scenario: Incremental improvements are made, but significant gaps remain, leaving organizations partially vulnerable to sophisticated attacks.
6. Key Individuals and Entities
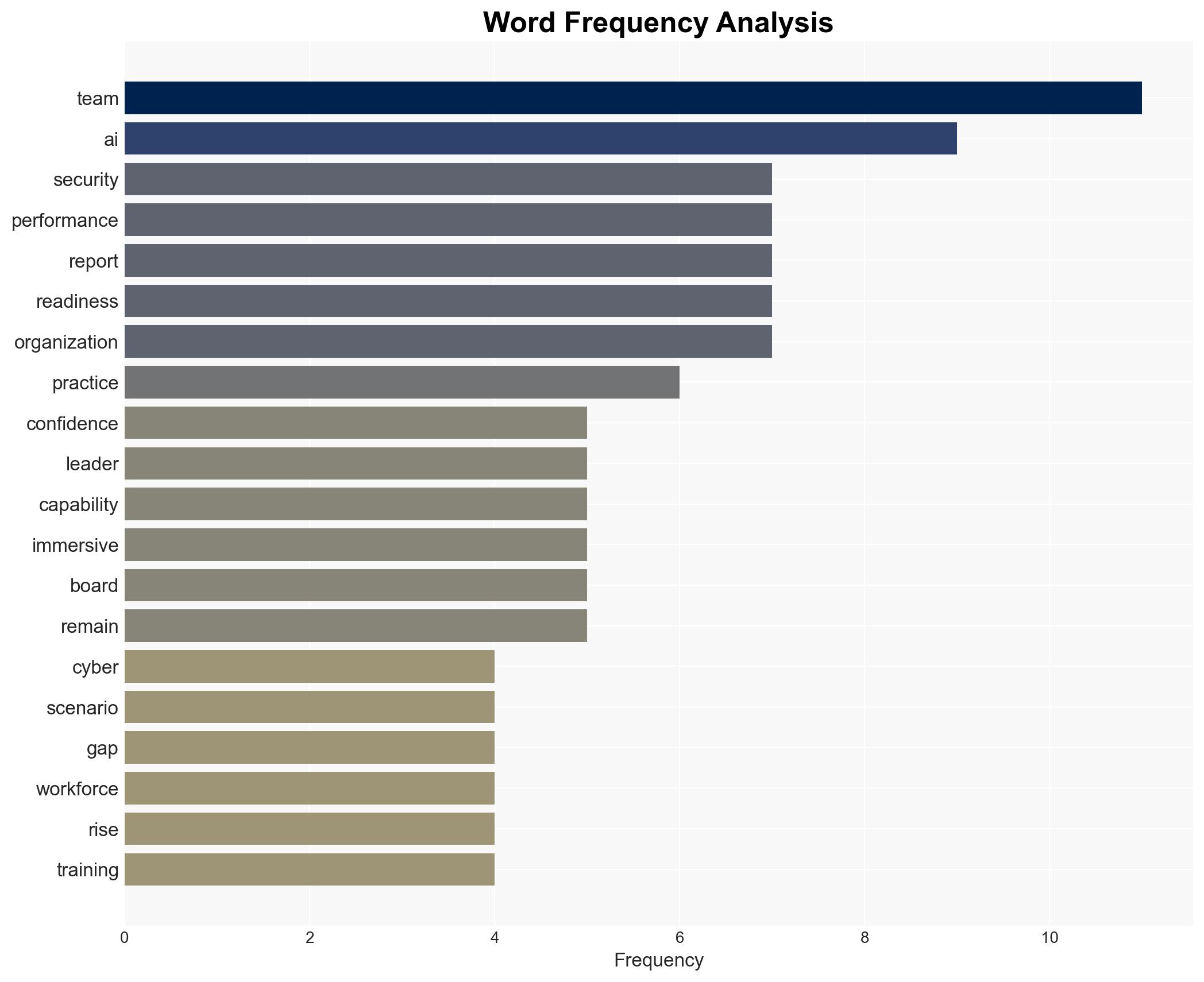
James Hadley, Chief Innovation Officer at Immersive, is a key individual advocating for improved training and metrics. His insights are critical to understanding the current landscape and potential solutions.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us