The Cost of Security Debt With Numbers – Rsolv.dev
Published on: 2025-07-31
Intelligence Report: The Cost of Security Debt With Numbers – Rsolv.dev
1. BLUF (Bottom Line Up Front)
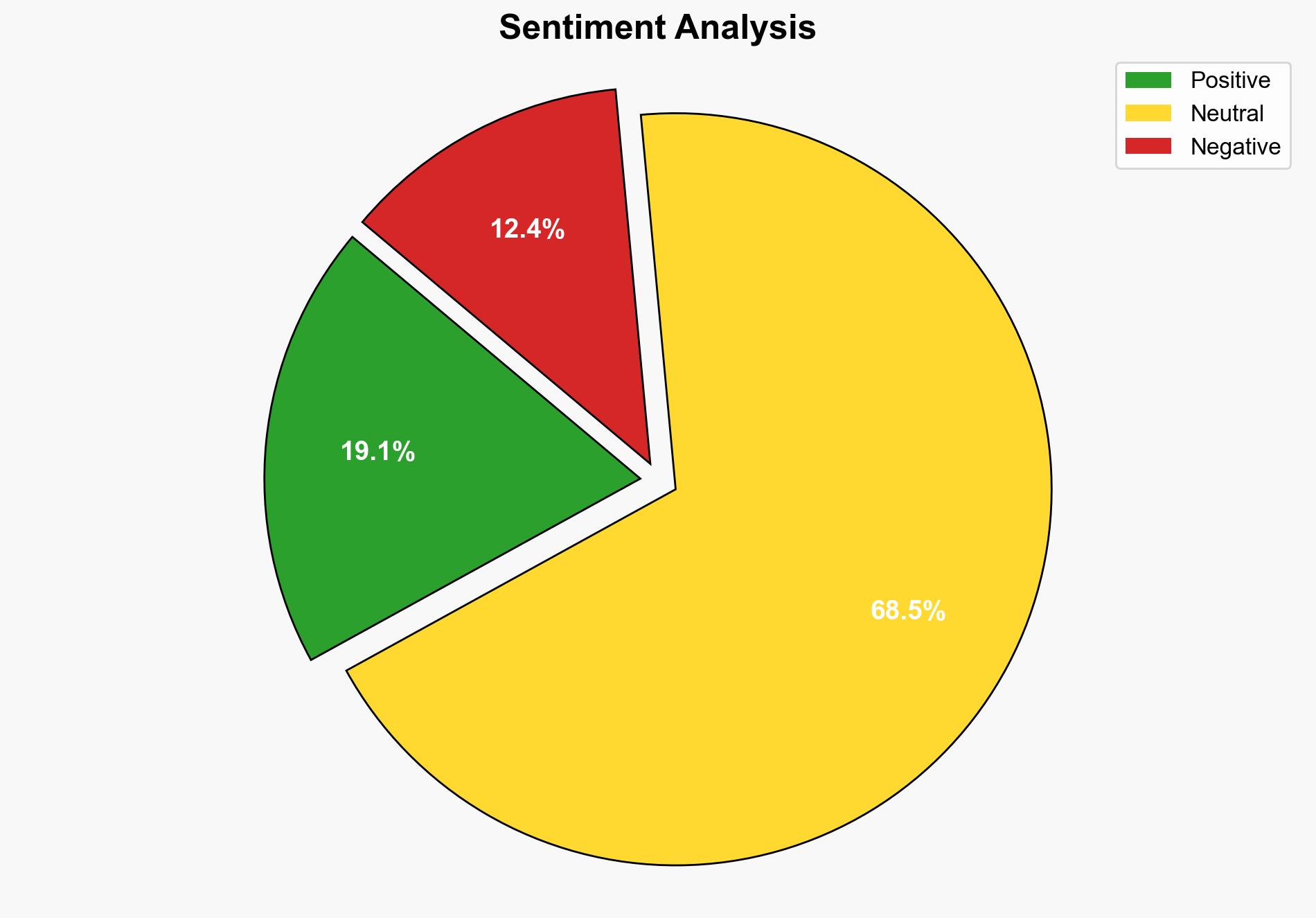
The analysis suggests that automating security vulnerability management significantly reduces costs and developer time compared to manual processes. This hypothesis is strongly supported by data from industry studies and reports. The recommended action is to invest in automation tools to enhance efficiency and reduce security debt. Confidence Level: High.
2. Competing Hypotheses
Hypothesis 1: Automating security vulnerability management reduces costs and developer time significantly compared to manual processes. This hypothesis is supported by data indicating that automation can cut the time spent on security tasks, leading to cost savings and improved efficiency.
Hypothesis 2: The perceived benefits of automation in security management are overstated, and manual processes remain necessary for effective vulnerability management. This hypothesis suggests that while automation can assist, the complexity and nuance of security vulnerabilities require human oversight that cannot be fully automated.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the consistency of data from multiple studies highlighting reduced developer time and cost savings through automation.
3. Key Assumptions and Red Flags
Assumptions:
– Automation tools are effective and reliable in identifying and managing vulnerabilities.
– The data provided by industry studies accurately reflects real-world scenarios.
Red Flags:
– Potential bias in studies funded by companies with vested interests in promoting automation.
– Lack of detailed information on the limitations of automation tools.
4. Implications and Strategic Risks
The shift towards automation in security management could lead to significant cost savings and efficiency gains. However, over-reliance on automation without adequate human oversight may increase the risk of undetected vulnerabilities. Economic implications include reduced operational costs, while cyber risks involve potential overconfidence in automated systems.
5. Recommendations and Outlook
- Invest in robust automation tools for security management to reduce costs and improve efficiency.
- Maintain a balanced approach by integrating human oversight to address complex vulnerabilities.
- Scenario Projections:
- Best Case: Successful integration of automation leads to significant cost reductions and enhanced security posture.
- Worst Case: Over-reliance on automation results in missed vulnerabilities and increased security incidents.
- Most Likely: A hybrid approach yields moderate cost savings and improved efficiency.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on companies and industry studies related to security management.
7. Thematic Tags
cybersecurity, automation, cost reduction, vulnerability management