The hidden risks inside open-source code – Help Net Security
Published on: 2025-09-30
Intelligence Report: The hidden risks inside open-source code – Help Net Security
1. BLUF (Bottom Line Up Front)
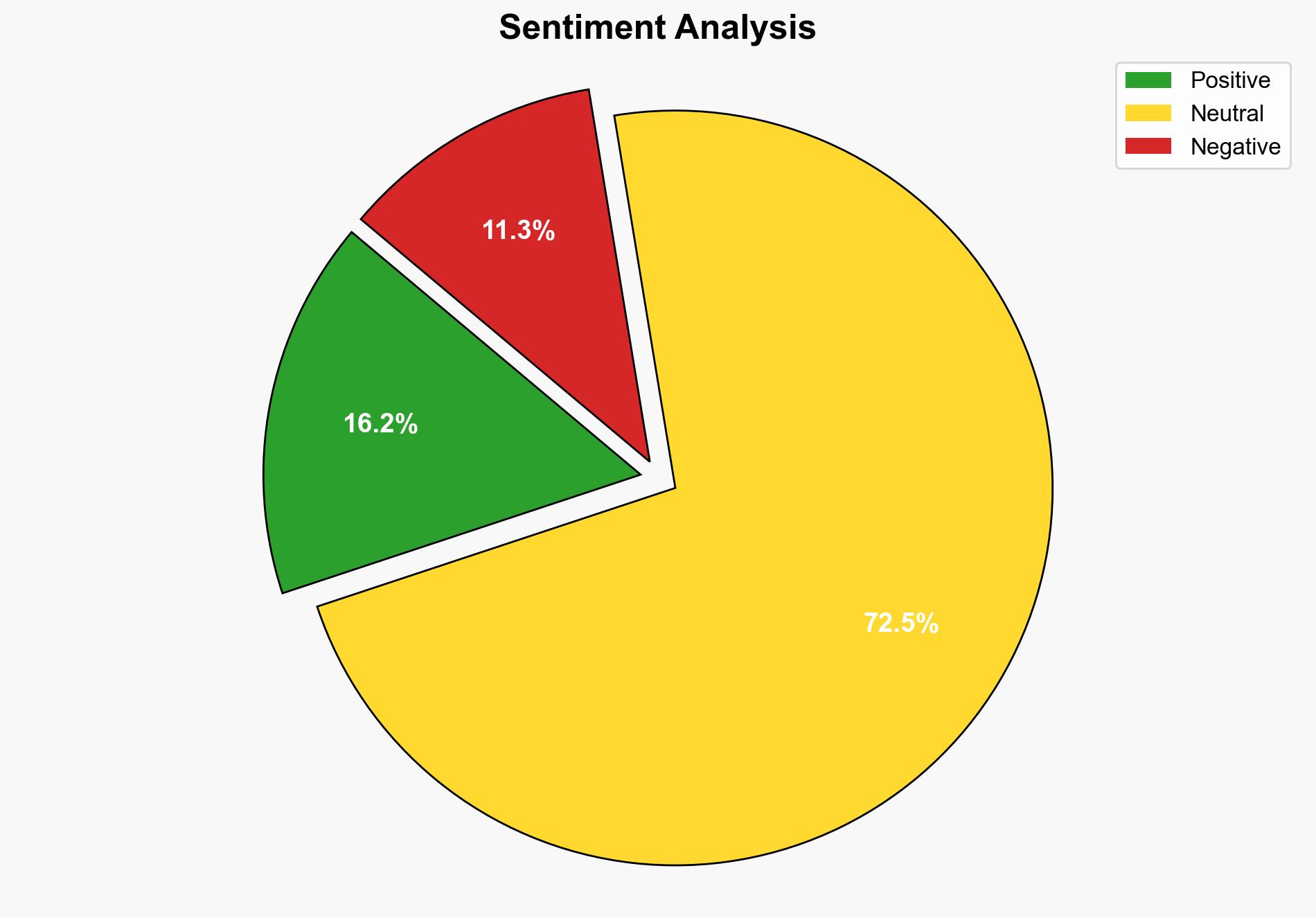
The analysis suggests that while open-source code is integral to modern software development, it presents significant security risks due to potential hidden vulnerabilities. The hypothesis that open-source projects, despite their transparency, can harbor undetected vulnerabilities is better supported. It is recommended that organizations implement continuous scanning and security integration processes to mitigate these risks. Confidence Level: Moderate.
2. Competing Hypotheses
1. **Open-source software is inherently riskier than proprietary software due to its open nature, which allows vulnerabilities to be more easily exploited.**
– This hypothesis suggests that the transparency of open-source software makes it more susceptible to exploitation, as malicious actors can easily access and analyze the code for vulnerabilities.
2. **Open-source software is not inherently riskier than proprietary software; rather, the risk is a function of the management and integration of open-source components.**
– This hypothesis posits that the security of open-source software depends largely on how it is managed, integrated, and updated within an organization’s infrastructure, rather than its open nature per se.
Using ACH 2.0, the second hypothesis is better supported by the evidence, which highlights the importance of continuous scanning and management of open-source components rather than the inherent nature of the software itself.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Open-source projects with large, active contributor bases are assumed to be more secure due to community scrutiny.
– Proprietary software is assumed to have fewer vulnerabilities due to controlled access.
– **Red Flags**:
– Over-reliance on static code scanning without integrating dynamic analysis or human review.
– Potential bias in assuming open-source software is inherently less secure without considering management practices.
4. Implications and Strategic Risks
– **Economic**: Increased costs associated with managing and securing open-source components.
– **Cyber**: Potential for significant breaches if vulnerabilities in open-source components are exploited.
– **Geopolitical**: Nations relying heavily on open-source software may face increased cyber threats.
– **Psychological**: Growing mistrust in open-source solutions could drive organizations to more expensive proprietary options.
5. Recommendations and Outlook
- Implement continuous scanning and integration of security measures in the development lifecycle.
- Develop a robust process for prioritizing and remediating vulnerabilities.
- Scenario Projections:
- Best Case: Organizations effectively manage open-source components, reducing vulnerabilities.
- Worst Case: Major security breaches due to unmanaged open-source vulnerabilities.
- Most Likely: Gradual improvement in open-source security management practices.
6. Key Individuals and Entities
– James Cusick
– Chromium Foundation
– Genann Project
7. Thematic Tags
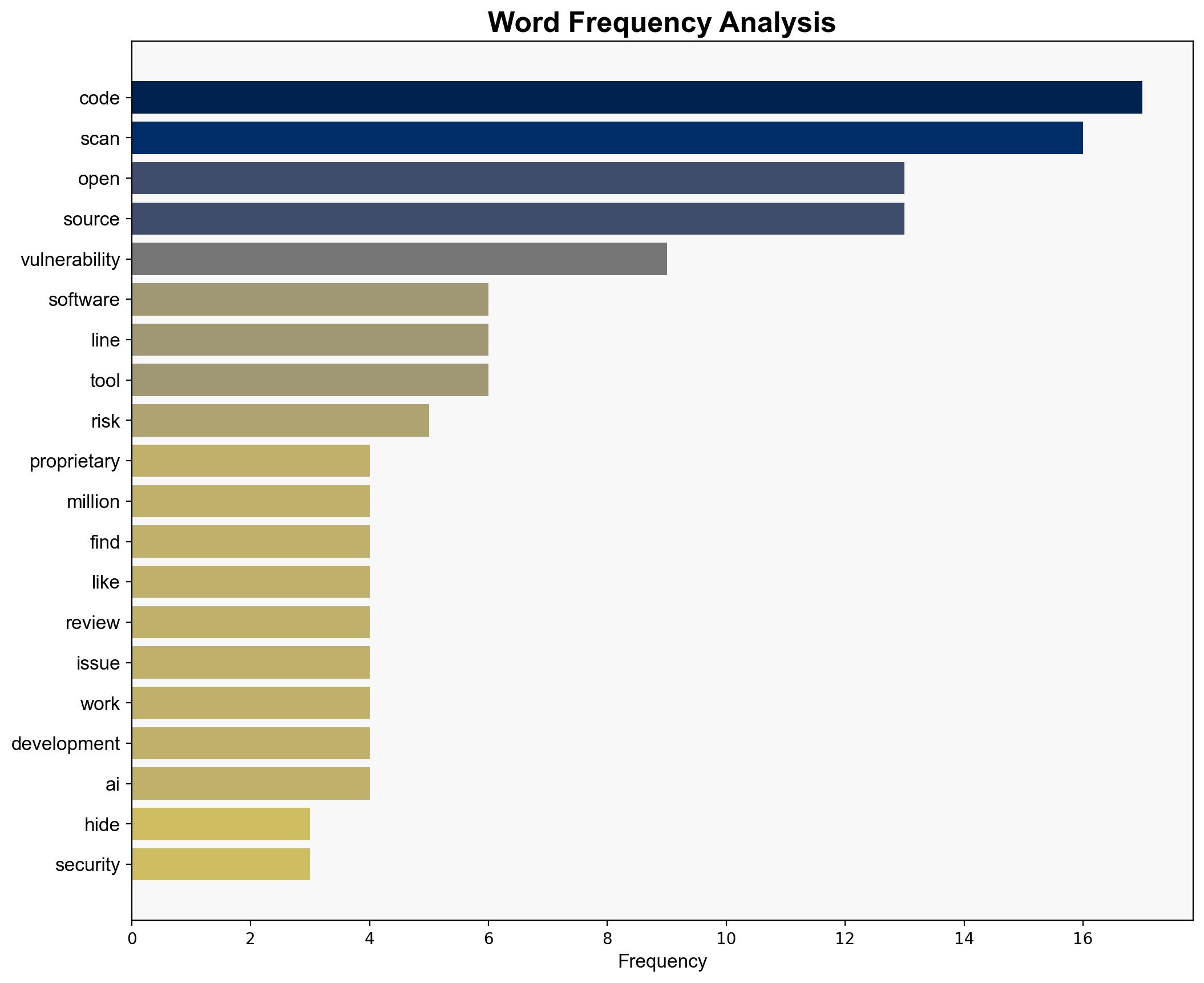
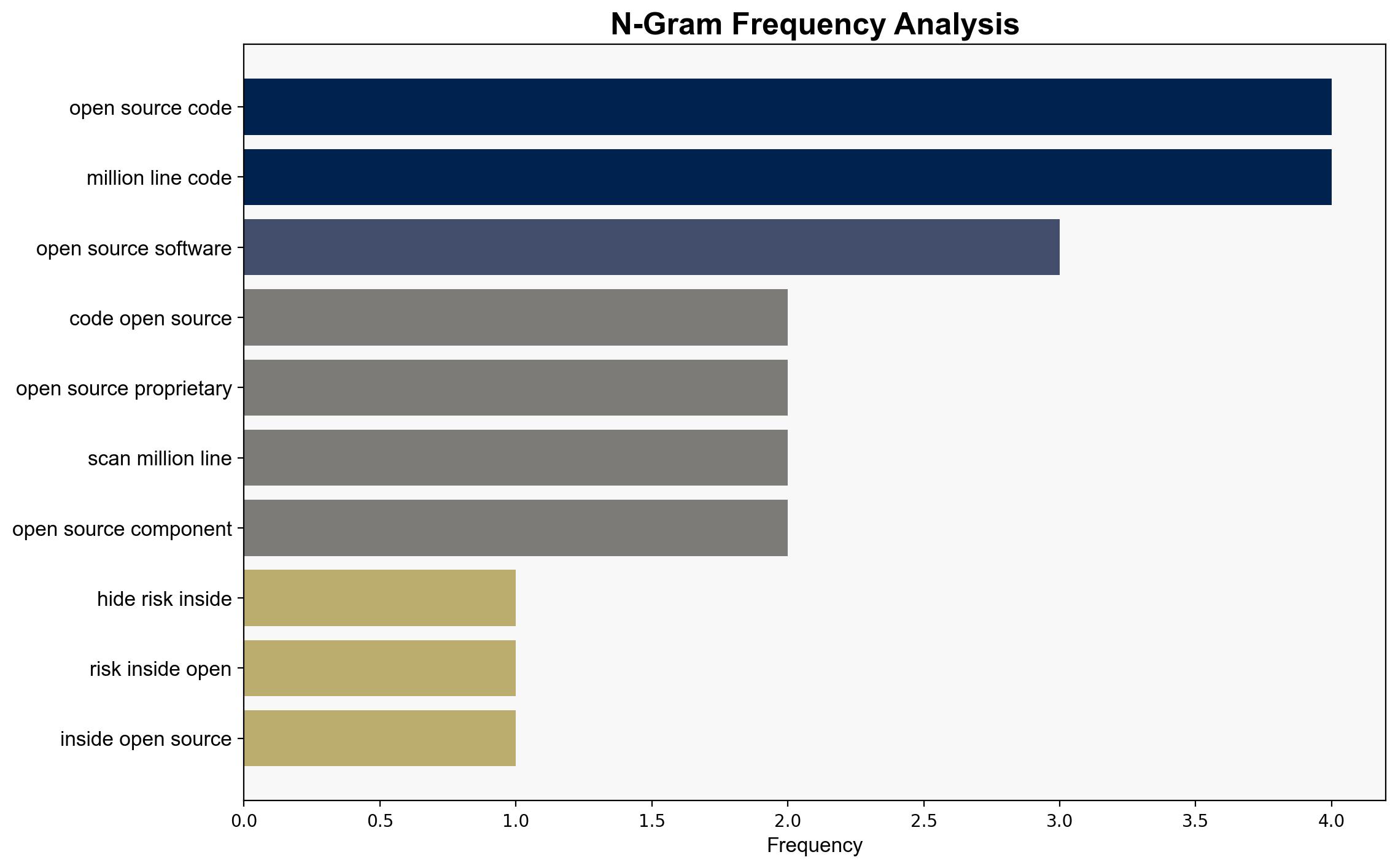
national security threats, cybersecurity, open-source software, software vulnerabilities