The Imperative of Data Protection in the Cloud – WebProNews
Published on: 2025-04-25
Intelligence Report: The Imperative of Data Protection in the Cloud – WebProNews
1. BLUF (Bottom Line Up Front)
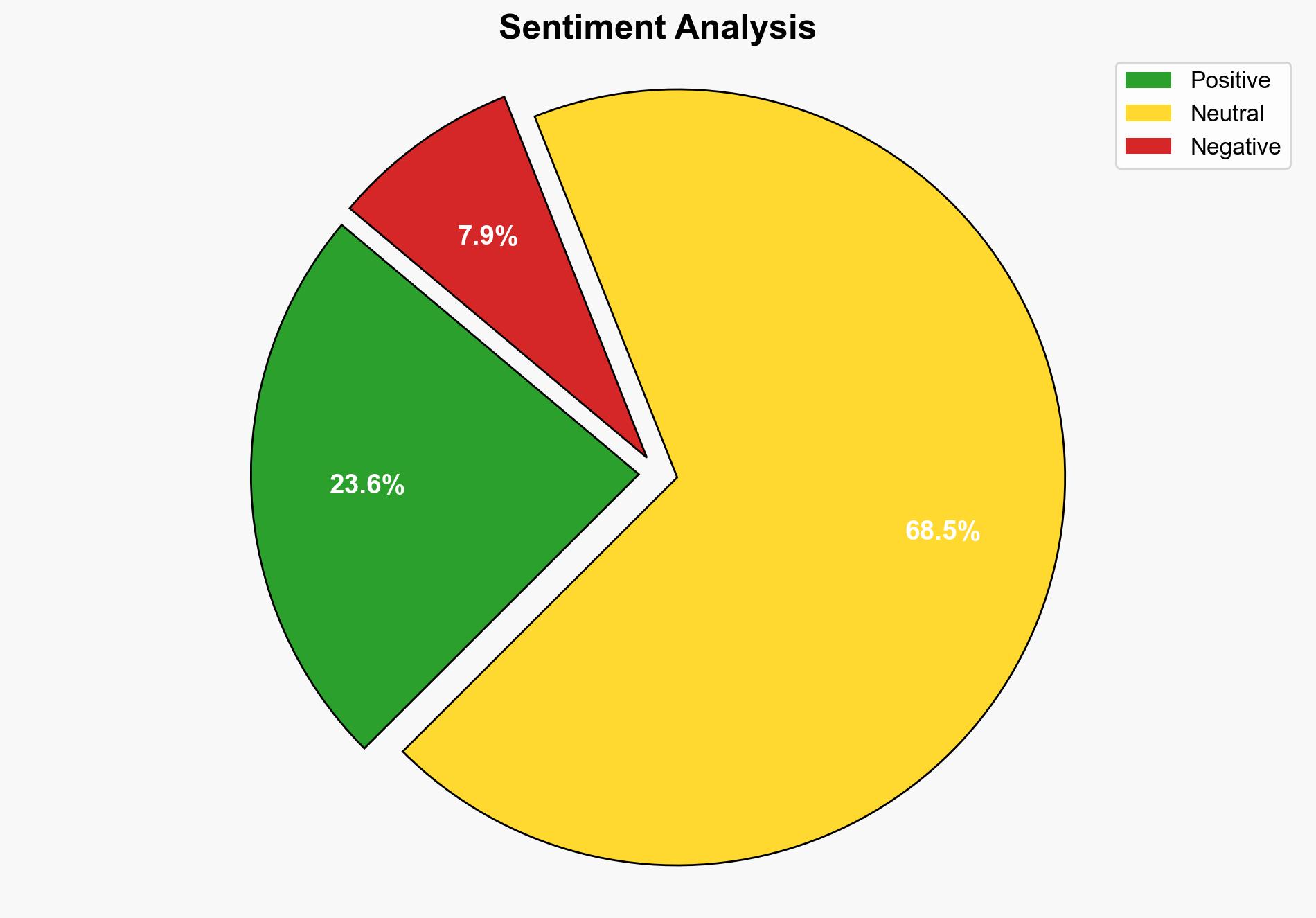
The rapid adoption of cloud computing offers significant business benefits but also introduces substantial risks related to data protection. Key findings indicate that misconfiguration, insider threats, and incomplete data backups are primary vulnerabilities. It is recommended that enterprises adopt a comprehensive data protection strategy incorporating robust identity access management, encryption, and regular data backups to mitigate these risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
Hypotheses regarding cloud data breaches include misconfiguration, insider threats, and inadequate backup strategies. Evidence strongly supports misconfiguration as the most frequent cause, with insider threats and backup failures also contributing significantly.
SWOT Analysis
Strengths: Cloud services offer scalability and efficiency.
Weaknesses: Misconfiguration and reliance on third-party security.
Opportunities: Implementing advanced security measures like zero trust and encryption.
Threats: Increasing sophistication of cyber attacks targeting cloud environments.
Indicators Development
Key indicators of emerging threats include unusual access patterns, unauthorized data access attempts, and phishing campaigns targeting cloud credentials.
3. Implications and Strategic Risks
The shift towards cloud computing increases exposure to cyber threats, with potential implications for data privacy and regulatory compliance. Misconfigurations can lead to significant data breaches, impacting organizational reputation and financial stability. The interconnected nature of cloud services amplifies the risk of cascading failures across sectors.
4. Recommendations and Outlook
- Implement a zero trust architecture and enforce strict identity access management protocols.
- Regularly audit and update cloud configurations to prevent misconfigurations.
- Maintain comprehensive data backup strategies independent of cloud service providers.
- Scenario Projections:
- Best Case: Enhanced security measures lead to reduced breach incidents.
- Worst Case: Persistent vulnerabilities result in major data breaches and regulatory penalties.
- Most Likely: Incremental improvements in security posture with ongoing challenges in compliance and threat mitigation.
5. Key Individuals and Entities
Specific individuals are not mentioned in the source text. The focus remains on enterprises and cloud service providers.
6. Thematic Tags
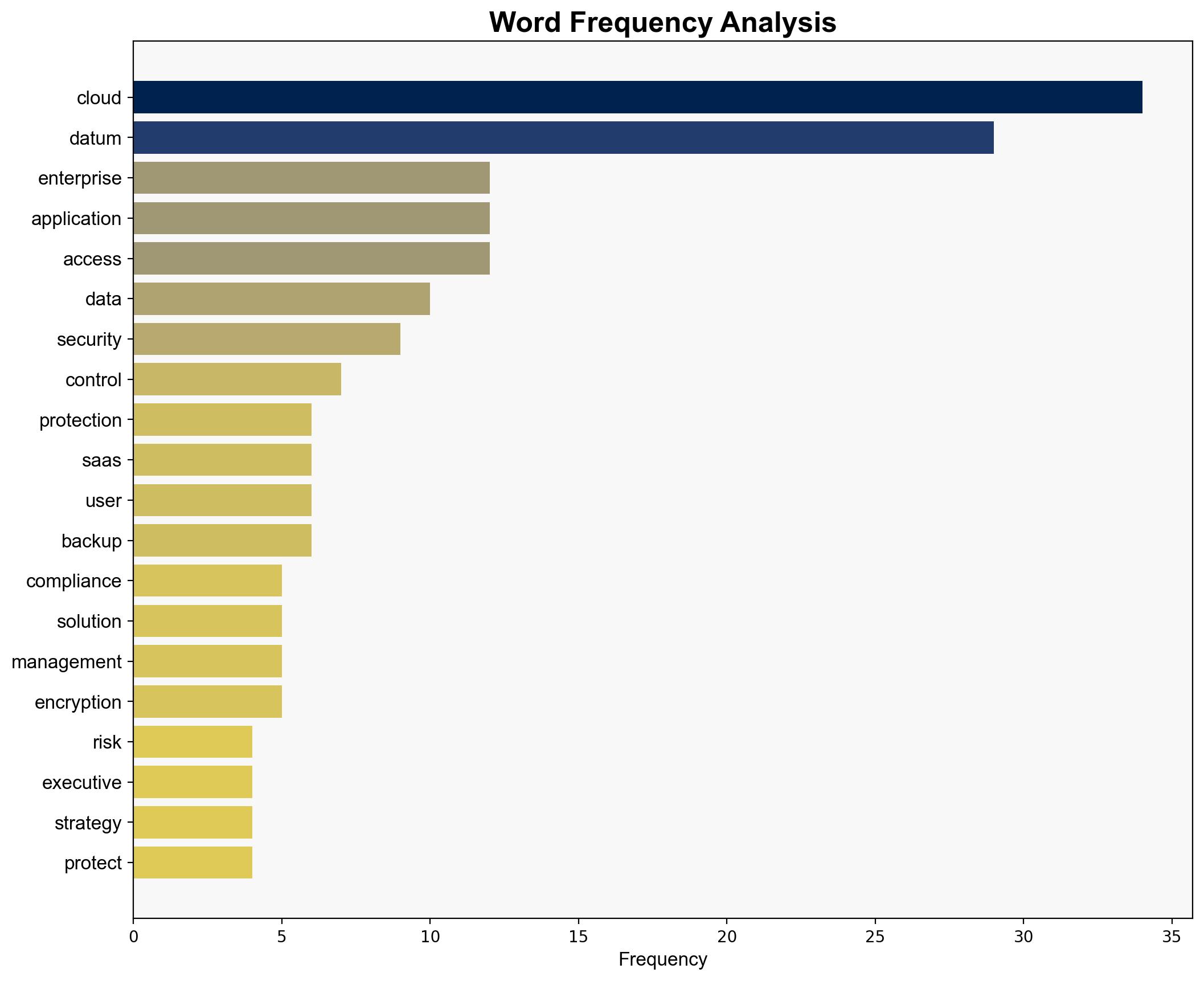
(‘cybersecurity’, ‘data protection’, ‘cloud computing’, ‘regulatory compliance’, ‘risk management’)