The Iran cyber threat is real – Wnd.com
Published on: 2025-07-13
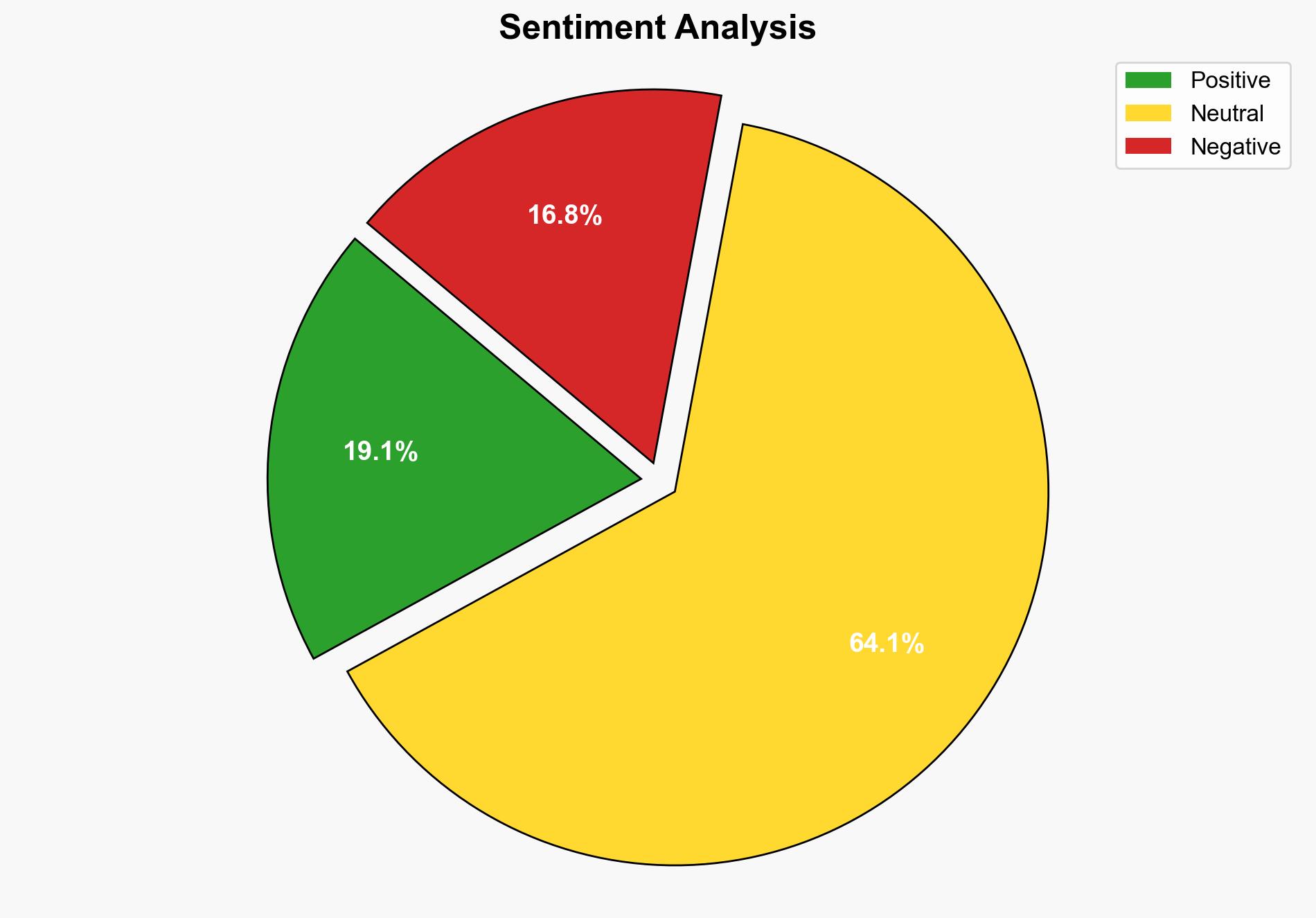
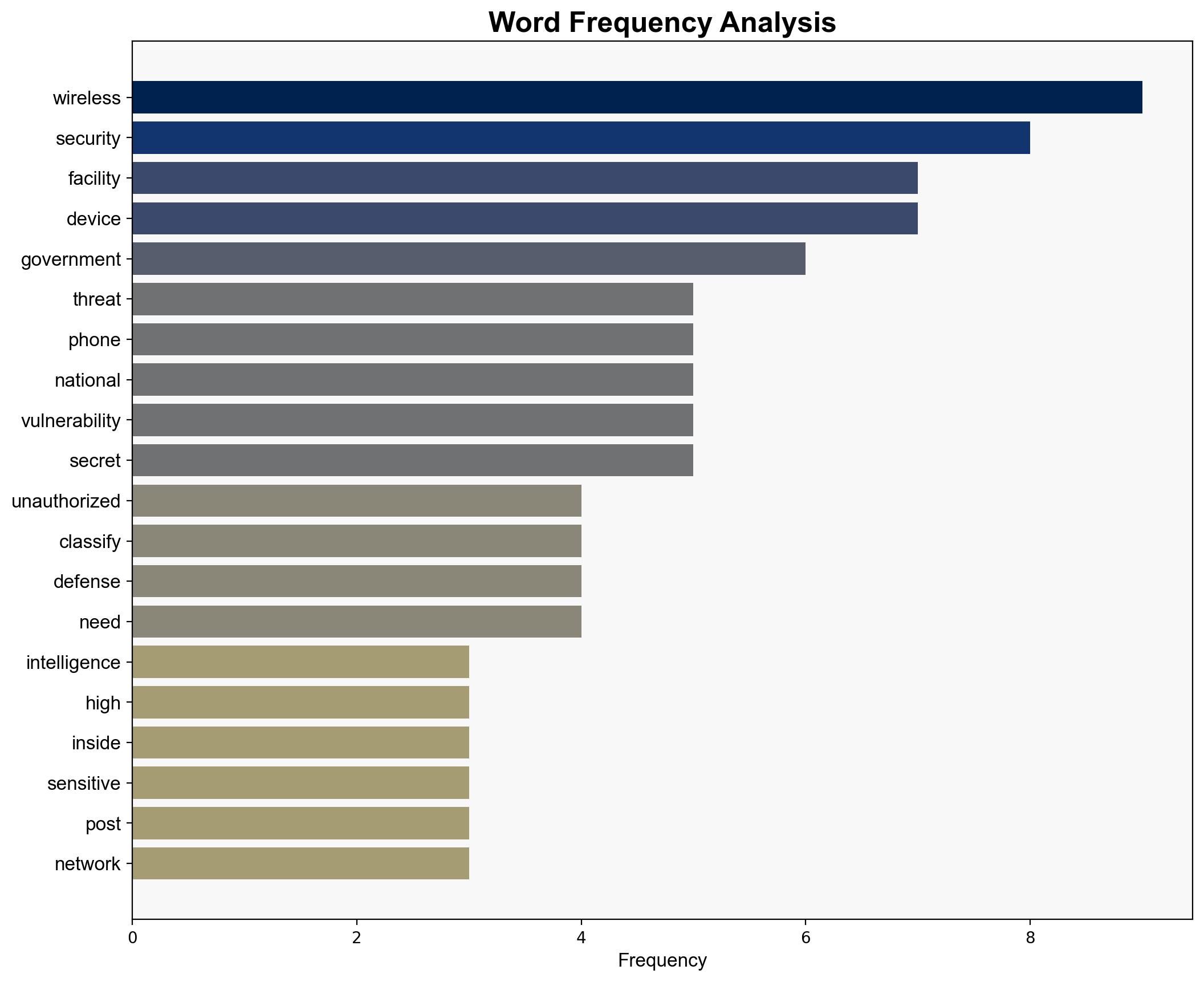
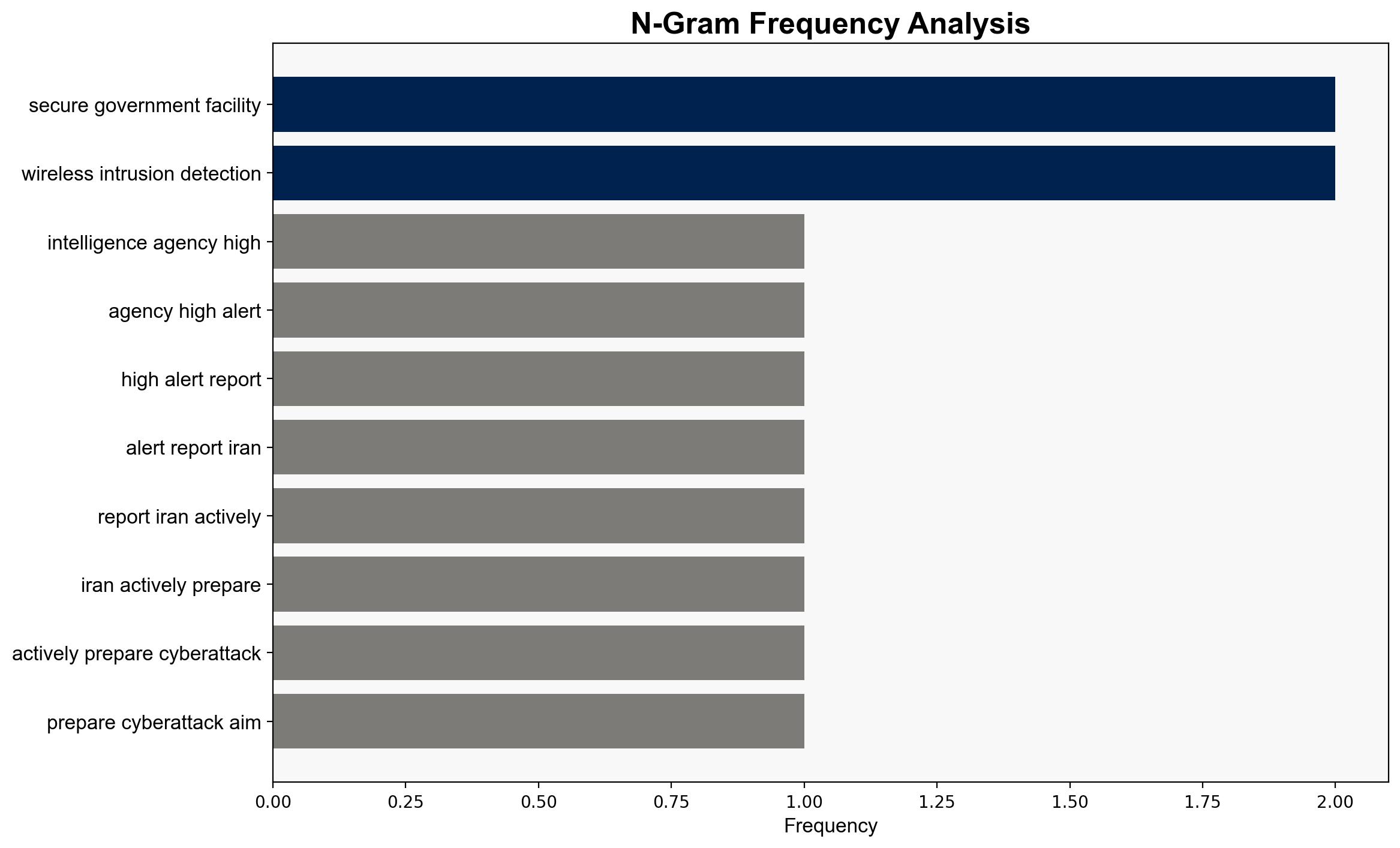
Intelligence Report: The Iran Cyber Threat is Real – Wnd.com
1. BLUF (Bottom Line Up Front)
The report identifies Iran as actively preparing for cyberattacks targeting critical government and military infrastructure. The vulnerabilities are exacerbated by inadequate investment in wireless intrusion detection systems and outdated security protocols in sensitive facilities. Immediate action is required to enhance cybersecurity measures and prevent potential breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that Iran’s cyber capabilities are evolving, with potential targets including government networks and military systems. This necessitates improved resilience strategies.
Indicators Development
Monitoring for anomalies in network traffic and user behavior is critical for early detection of cyber threats. This includes unauthorized device detection within secure areas.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of cyberattack attempts, with pathways potentially exploiting insider threats and unsecured wireless devices.
Network Influence Mapping
Mapping reveals key influence nodes that could be leveraged by adversaries to amplify cyberattack impacts, highlighting the need for robust countermeasures.
3. Implications and Strategic Risks
The systemic vulnerabilities in wireless security pose significant risks, potentially allowing adversaries to access classified information. The cascading effects of a successful cyberattack could disrupt national security operations and compromise sensitive data, leading to broader geopolitical instability.
4. Recommendations and Outlook
- Invest in and deploy comprehensive wireless intrusion detection systems across all sensitive facilities to detect unauthorized devices.
- Enhance training programs for personnel to recognize and report potential cyber threats, focusing on the risks posed by modern smartphones and other portable devices.
- Scenario-based projections:
- Best Case: Rapid implementation of security measures mitigates risks with minimal disruption.
- Worst Case: Delayed response leads to a successful cyberattack, compromising critical infrastructure.
- Most Likely: Incremental improvements reduce risk but leave some vulnerabilities exposed.
5. Key Individuals and Entities
Asif Rahman
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus