The Ongoing Fallout from a Breach at AI Chatbot Maker Salesloft – Krebs on Security
Published on: 2025-09-01
Intelligence Report: The Ongoing Fallout from a Breach at AI Chatbot Maker Salesloft – Krebs on Security
1. BLUF (Bottom Line Up Front)
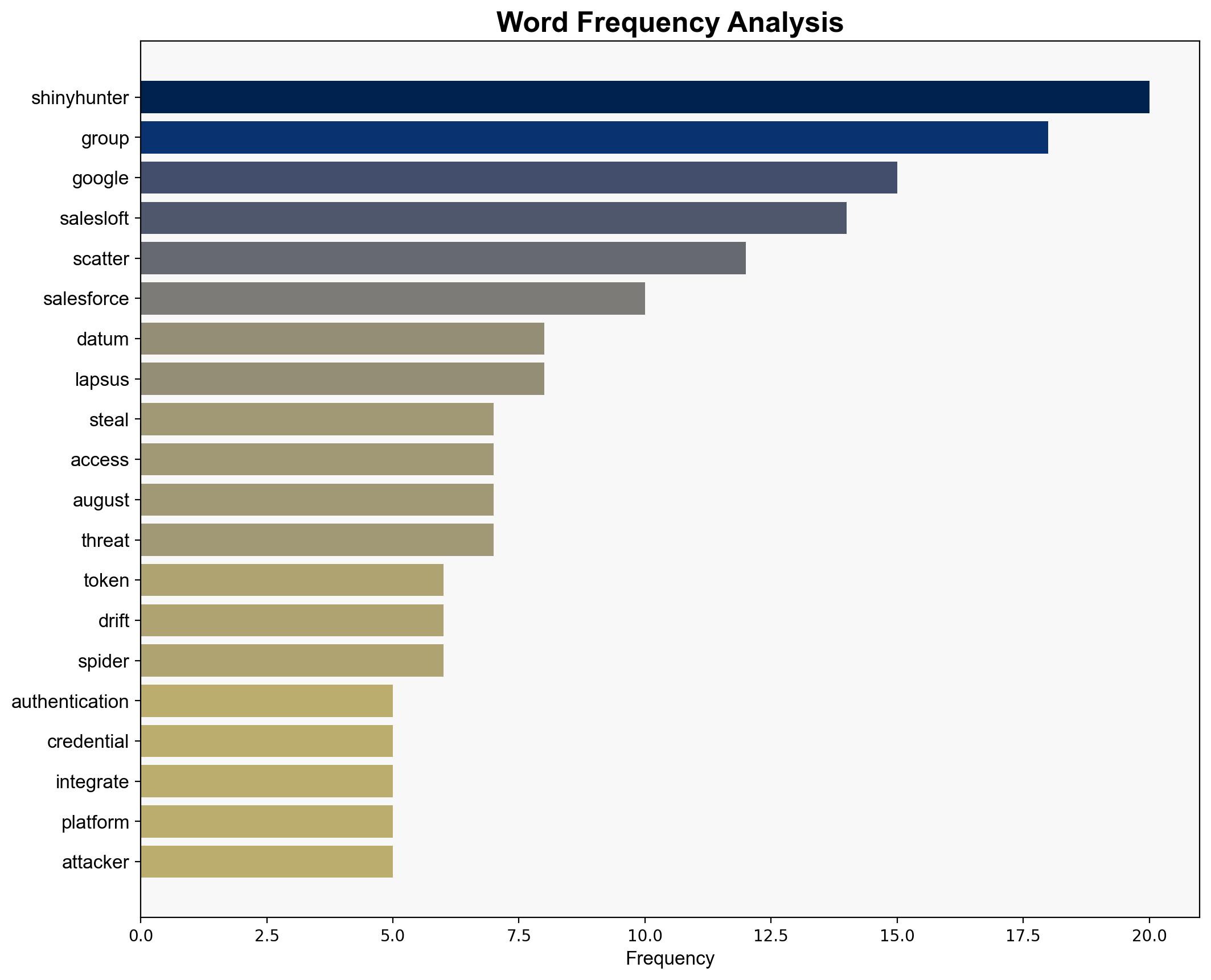
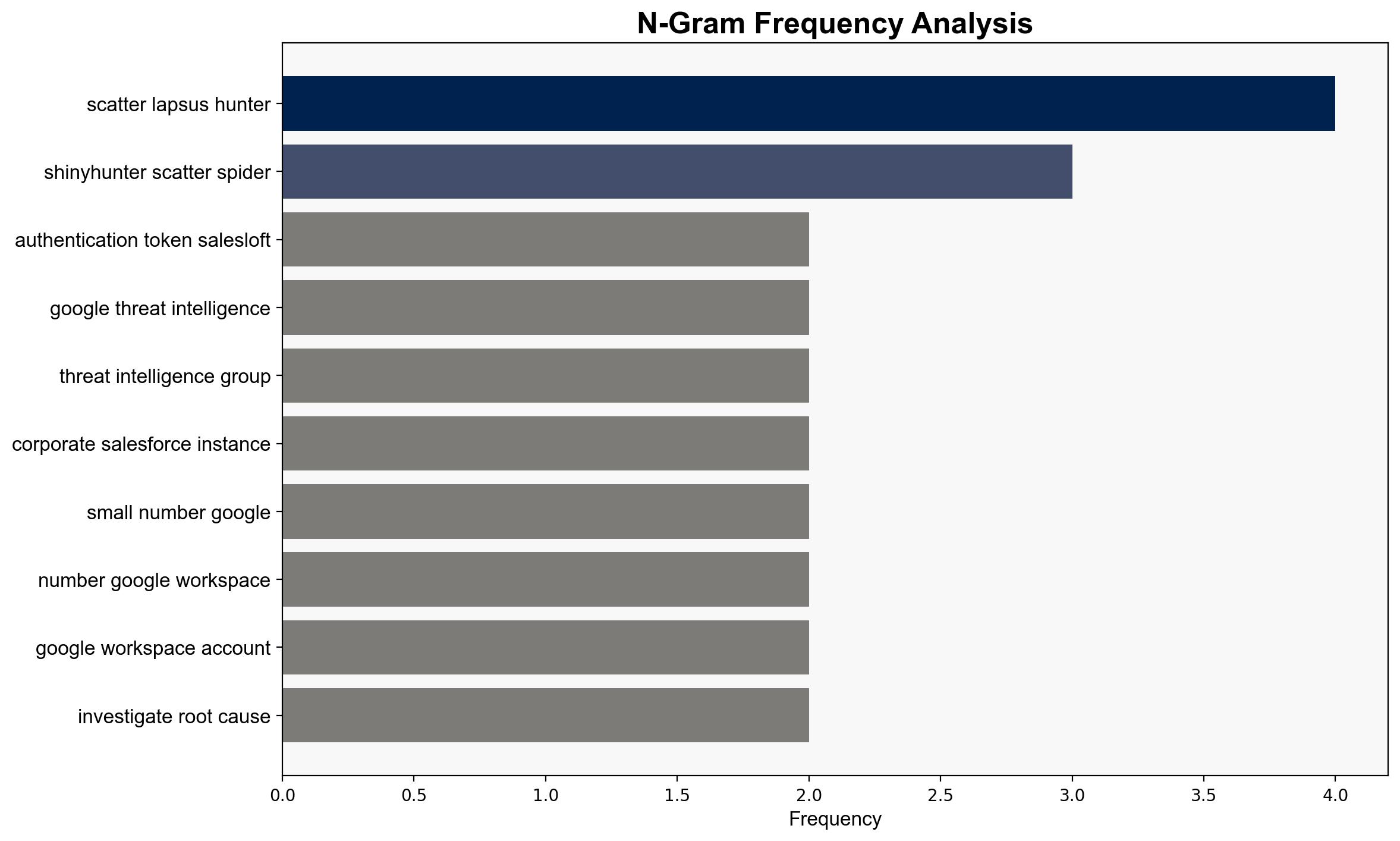
The breach at Salesloft, involving the theft of authentication tokens, poses significant risks to numerous corporate entities due to potential unauthorized access to integrated services like Salesforce, Google Workspace, and others. The most supported hypothesis is that the breach is part of a broader, coordinated cyber campaign by a sophisticated threat group. Immediate action is recommended to invalidate all potentially compromised tokens and enhance monitoring for unusual activity. Confidence level: High.
2. Competing Hypotheses
Hypothesis 1: The breach is an isolated incident conducted by opportunistic cybercriminals seeking to exploit vulnerabilities for immediate financial gain through extortion or data resale.
Hypothesis 2: The breach is part of a coordinated campaign by a sophisticated threat group, such as ShinyHunter, aiming to infiltrate multiple corporate environments for long-term strategic advantage and data exploitation.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes limited coordination and short-term objectives.
– Hypothesis 2 assumes high coordination and strategic objectives.
Red Flags:
– Lack of specific attribution to a known group.
– The potential for underreporting of affected entities.
– Inconsistent data on the extent of data exfiltration.
4. Implications and Strategic Risks
The breach could lead to widespread unauthorized access to sensitive corporate data, resulting in financial losses, reputational damage, and potential regulatory penalties. The involvement of a sophisticated threat group suggests a risk of further coordinated attacks, possibly escalating to include ransomware or targeted data leaks. The incident underscores vulnerabilities in third-party integrations and the need for robust security protocols.
5. Recommendations and Outlook
- Immediate invalidation of all potentially compromised authentication tokens.
- Enhanced monitoring and anomaly detection across integrated platforms.
- Conduct a comprehensive security audit of third-party integrations.
- Best Case: Rapid containment and remediation with minimal data loss.
- Worst Case: Escalation to widespread data breaches and extortion attacks.
- Most Likely: Continued attempts at exploitation by the threat group, necessitating ongoing vigilance.
6. Key Individuals and Entities
– ShinyHunter (Threat Group)
– Google Threat Intelligence Group (GTIG)
– Salesloft
– Salesforce
– Google Workspace
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus