The password problem we keep pretending to fix – Help Net Security
Published on: 2025-10-16
Intelligence Report: The password problem we keep pretending to fix – Help Net Security
1. BLUF (Bottom Line Up Front)
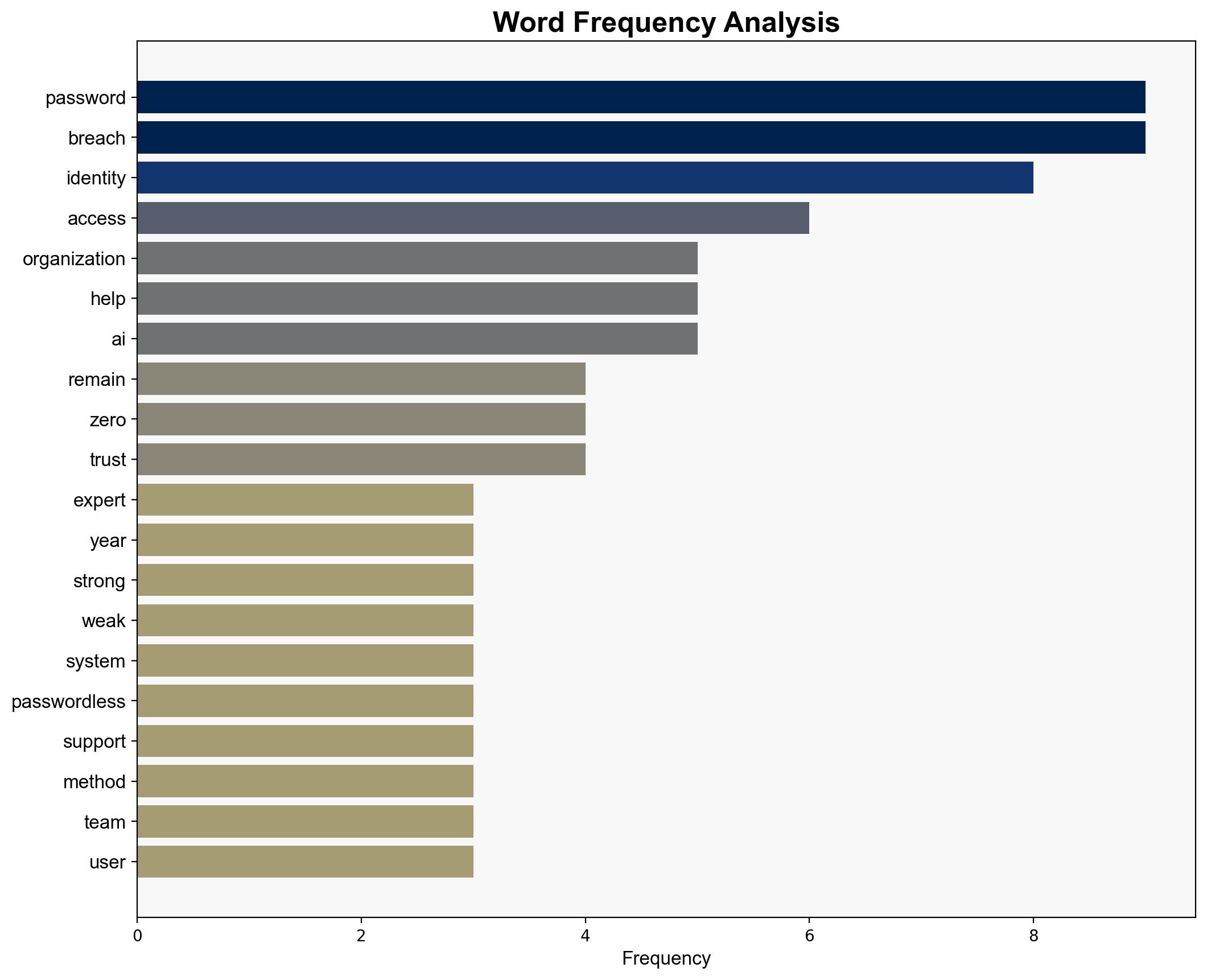
The most supported hypothesis suggests that despite efforts to transition to passwordless systems, passwords remain a dominant form of authentication due to legacy system constraints and organizational inertia. This perpetuates vulnerabilities to identity breaches. Confidence Level: Moderate. Recommended action: Accelerate the adoption of passwordless systems and enhance training for support teams to mitigate social engineering risks.
2. Competing Hypotheses
1. **Hypothesis A**: Organizations are genuinely committed to transitioning to passwordless systems, but face significant technical and operational barriers, such as legacy software compatibility and the need for major infrastructure overhauls.
2. **Hypothesis B**: Organizations are superficially addressing the password problem, using it as a facade to show progress while maintaining the status quo due to cost concerns and lack of immediate incentives to change.
Using ACH 2.0, Hypothesis A is better supported by the evidence of ongoing investments and the technical challenges cited, while Hypothesis B is weakened by the reported efforts and intent to modernize.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that organizations have the capability and resources to transition to passwordless systems if they choose to prioritize it.
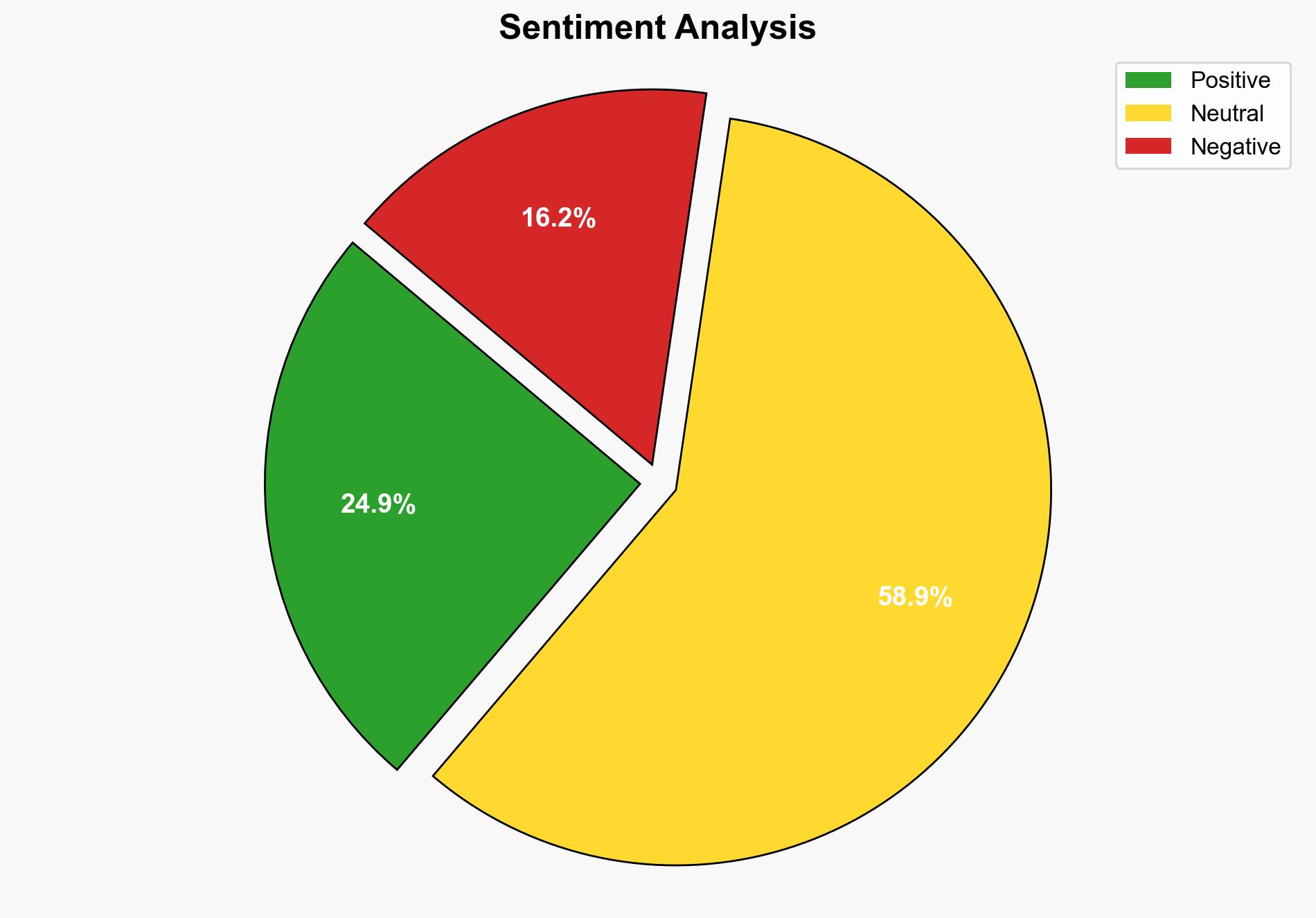
– **Red Flags**: The mismatch between reported zero trust maturity and actual breach numbers suggests potential over-reporting of progress.
– **Blind Spots**: The reliance on legacy systems and the complexity of transitioning to new authentication methods may be underestimated.
4. Implications and Strategic Risks
The continued reliance on passwords poses significant cybersecurity risks, including increased vulnerability to identity breaches and lateral attacks. Economically, the cost of breaches and the potential for operational disruption are substantial. Psychologically, repeated breaches can erode trust in organizational security measures. Geopolitically, widespread breaches could destabilize industries reliant on secure digital transactions.
5. Recommendations and Outlook
- **Mitigation**: Prioritize the transition to passwordless systems by allocating resources for infrastructure upgrades and training.
- **Opportunity**: Leverage AI to enhance detection and response capabilities, reducing the impact of breaches.
- **Scenario Projections**:
- **Best Case**: Successful transition to passwordless systems reduces breach incidents significantly.
- **Worst Case**: Continued reliance on passwords leads to a major breach with widespread operational impact.
- **Most Likely**: Gradual improvements in authentication methods with intermittent breaches due to legacy system vulnerabilities.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Entities include organizations facing identity breaches and those involved in the transition to passwordless systems.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus