The Role of VPNs in Safeguarding Startups’ Online Financial Transactions Against Cyber Threats
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
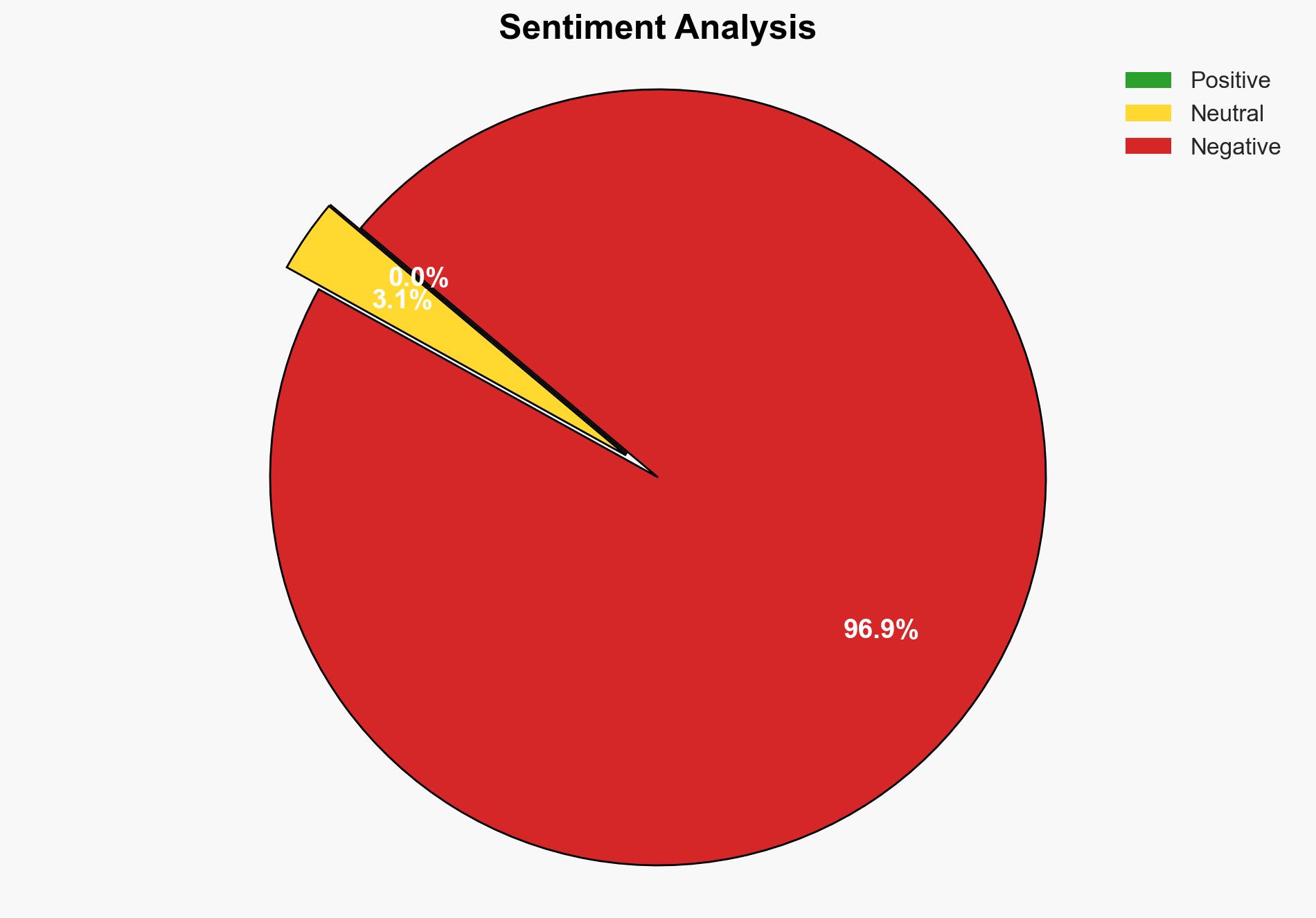
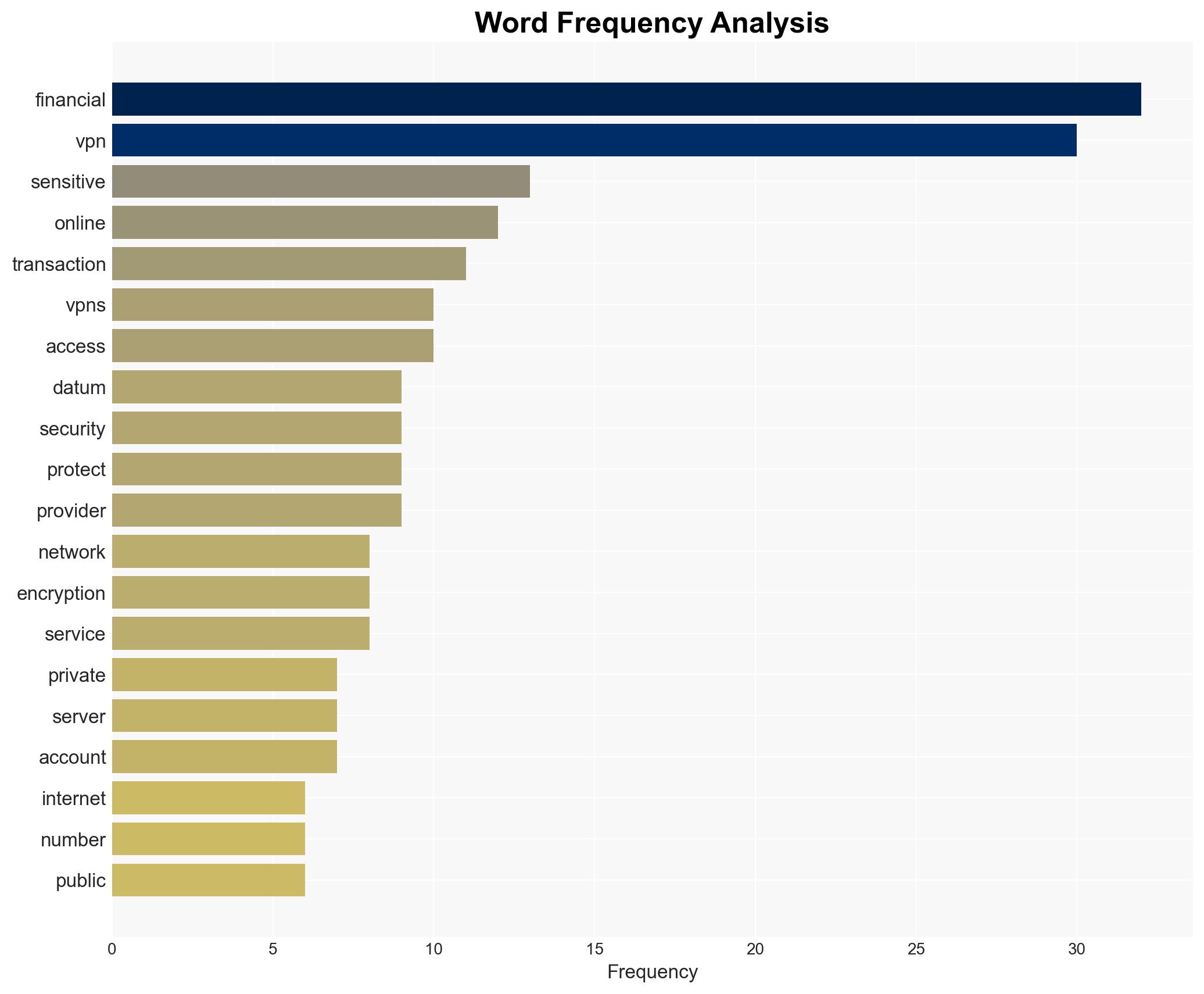
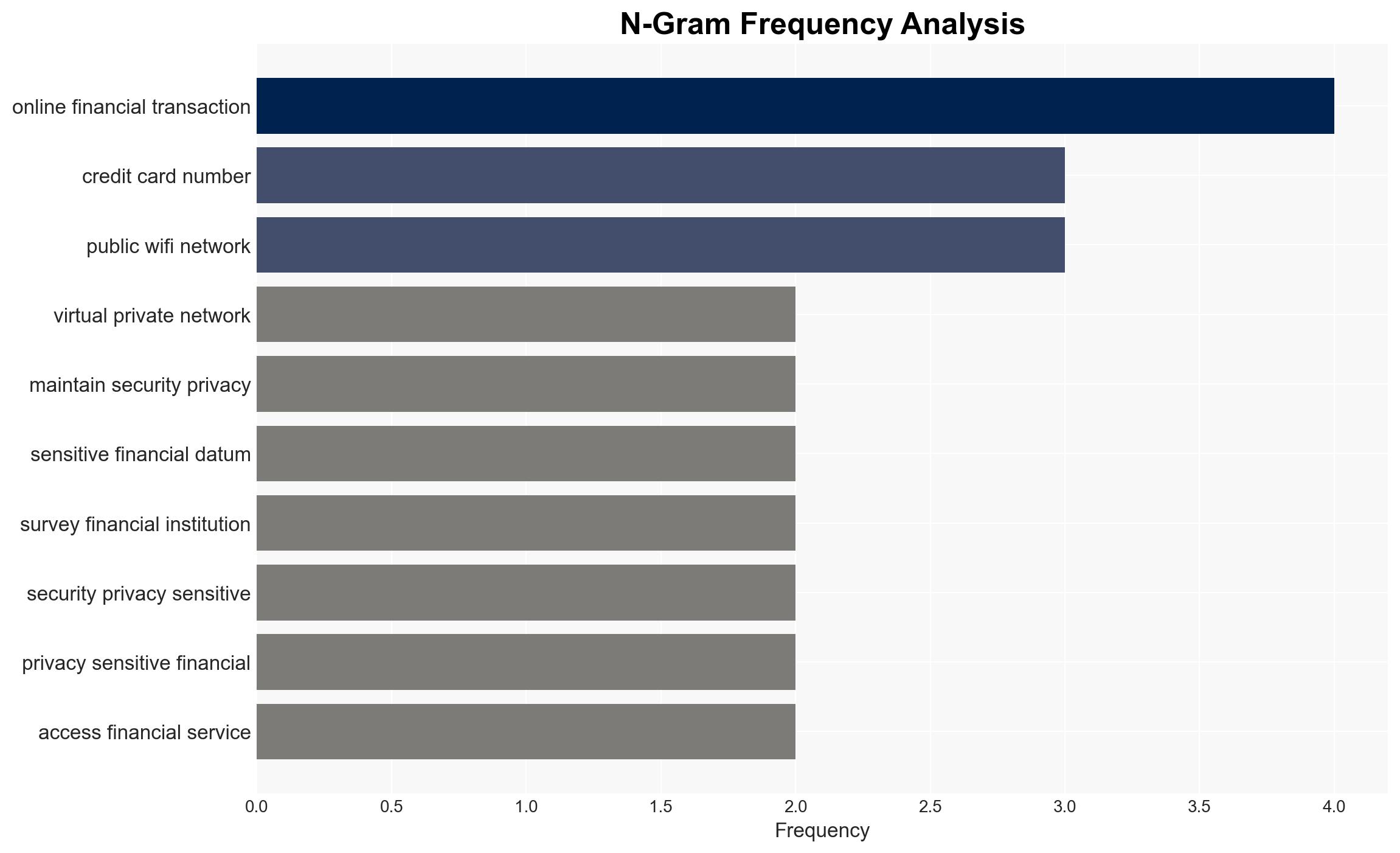
The use of Virtual Private Networks (VPNs) is a viable strategy to enhance the security of startups’ online financial activities, with a moderate to high confidence level. The most supported hypothesis is that VPNs significantly reduce the risk of cyber threats by encrypting data and masking IP addresses. It is recommended that startups integrate VPNs into their cybersecurity protocols to safeguard sensitive financial data.
2. Competing Hypotheses
Hypothesis 1: VPNs are effective in securing startups’ online financial activities by encrypting data and masking IP addresses, thus reducing the risk of cyber threats.
Hypothesis 2: VPNs provide limited security benefits for startups’ online financial activities due to potential vulnerabilities in VPN technology and the sophistication of cybercriminals.
Hypothesis 1 is more likely due to the inherent encryption and IP masking capabilities of VPNs, which are designed to protect data from interception. However, the effectiveness of VPNs can be compromised by factors such as outdated software, weak passwords, or VPN service provider vulnerabilities.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that startups will implement VPNs correctly and maintain updated software. It is also assumed that VPNs are used in conjunction with other cybersecurity measures.
Red Flags: Over-reliance on VPNs without additional security measures could lead to a false sense of security. Additionally, VPN service providers may be susceptible to breaches themselves, posing a risk to users.
4. Implications and Strategic Risks
Failure to adequately secure online financial activities could lead to data breaches, financial loss, and reputational damage for startups. The increasing sophistication of cybercriminals poses a continuous threat, necessitating ongoing vigilance and adaptation of cybersecurity strategies. There is also a risk of regulatory repercussions if sensitive data is compromised.
5. Recommendations and Outlook
- Startups should adopt VPNs as part of a comprehensive cybersecurity strategy, ensuring regular updates and strong password policies.
- Conduct regular cybersecurity audits to identify and mitigate vulnerabilities.
- Best-case scenario: Startups successfully integrate VPNs and other security measures, significantly reducing cyber threats.
- Worst-case scenario: A major breach occurs due to reliance on a compromised VPN provider, leading to severe financial and reputational damage.
- Most-likely scenario: VPNs provide a moderate level of security, but startups must remain vigilant and proactive in their cybersecurity efforts.
6. Key Individuals and Entities
Shushant Sudarshan (Author of the source text)
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us