The Security of Old Tech – Sqlservercentral.com
Published on: 2025-09-12
Intelligence Report: The Security of Old Tech – Sqlservercentral.com
1. BLUF (Bottom Line Up Front)
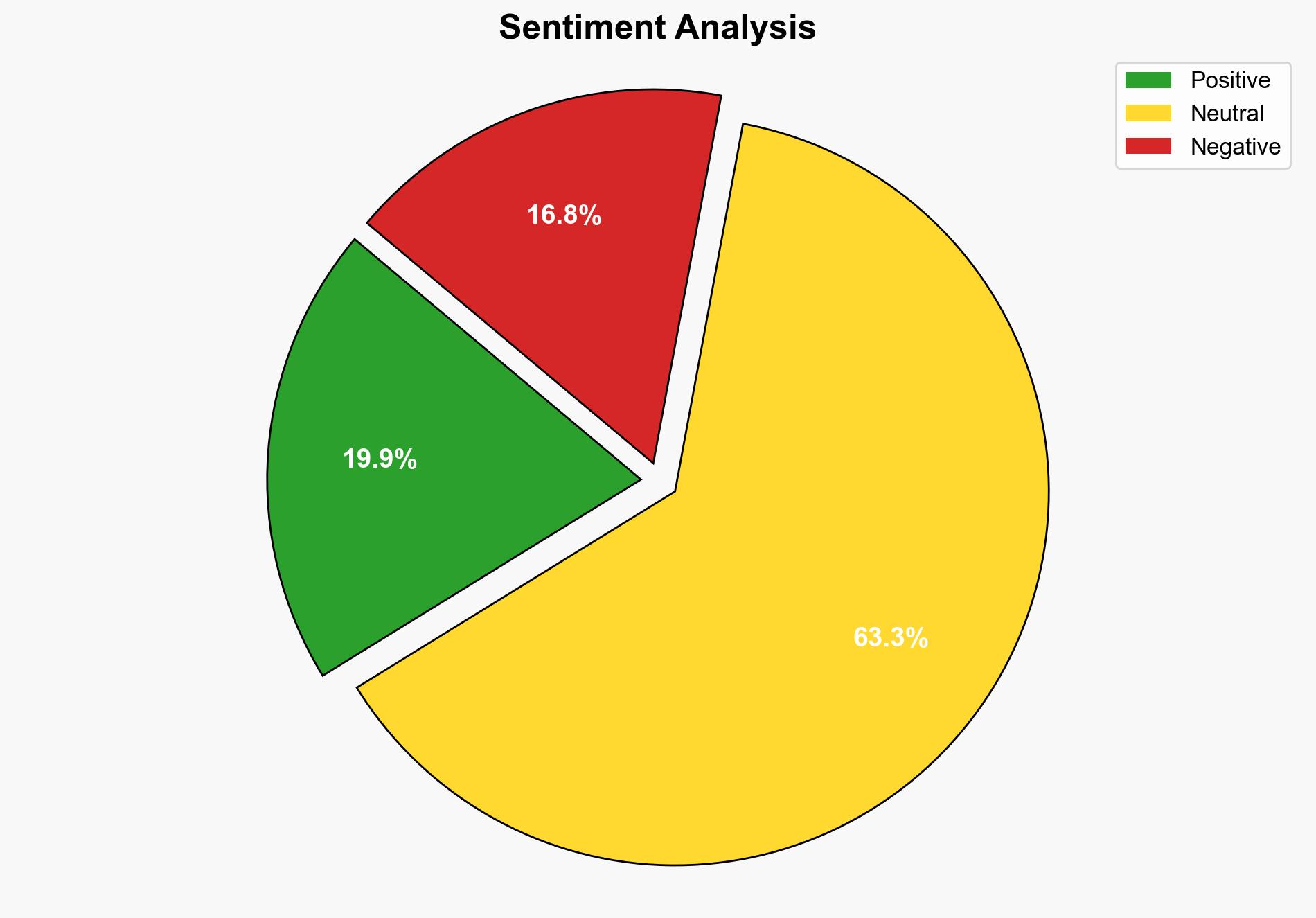
The most supported hypothesis is that outdated technology systems, such as those using old versions of Windows and SQL Server, pose significant cybersecurity risks, particularly in critical infrastructure sectors like air traffic management. Confidence Level: Moderate. Recommended action is to prioritize the modernization of these systems to enhance security and resilience against cyber threats.
2. Competing Hypotheses
– **Hypothesis 1**: The persistence of outdated technology in critical sectors is primarily due to budgetary constraints and operational inertia, leading to increased vulnerability to cyberattacks.
– **Hypothesis 2**: The use of outdated technology is a strategic choice to maintain stability and reliability, as newer systems may introduce unforeseen vulnerabilities and operational disruptions.
Using ACH 2.0, Hypothesis 1 is better supported by the evidence of successful cyber intrusions and the lack of modern security features such as multi-factor authentication (MFA) and robust monitoring. Hypothesis 2 is less supported due to the absence of evidence that newer systems are inherently less secure when properly managed and updated.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that upgrading technology will inherently improve security. It is also assumed that current systems lack adequate security measures due to their age.
– **Red Flags**: The article does not provide specific examples of newer systems failing due to unforeseen vulnerabilities, which weakens Hypothesis 2. There is also a lack of detailed financial analysis to support the budgetary constraint argument in Hypothesis 1.
4. Implications and Strategic Risks
The continued use of outdated technology in critical infrastructure increases the risk of cyberattacks, potentially leading to operational disruptions, economic losses, and national security threats. If not addressed, this could escalate into a broader crisis, affecting public trust and international relations, especially if state actors are involved in cyber intrusions.
5. Recommendations and Outlook
- Conduct a comprehensive audit of technology systems in critical sectors to identify vulnerabilities.
- Develop a phased modernization plan that includes budget allocation and risk management strategies.
- Implement immediate security measures, such as MFA and enhanced monitoring, on existing systems.
- Scenario Projections:
- Best Case: Successful modernization leads to enhanced security and operational efficiency.
- Worst Case: Failure to upgrade results in a major cyberattack with significant disruptions.
- Most Likely: Gradual improvements with intermittent challenges as systems are upgraded.
6. Key Individuals and Entities
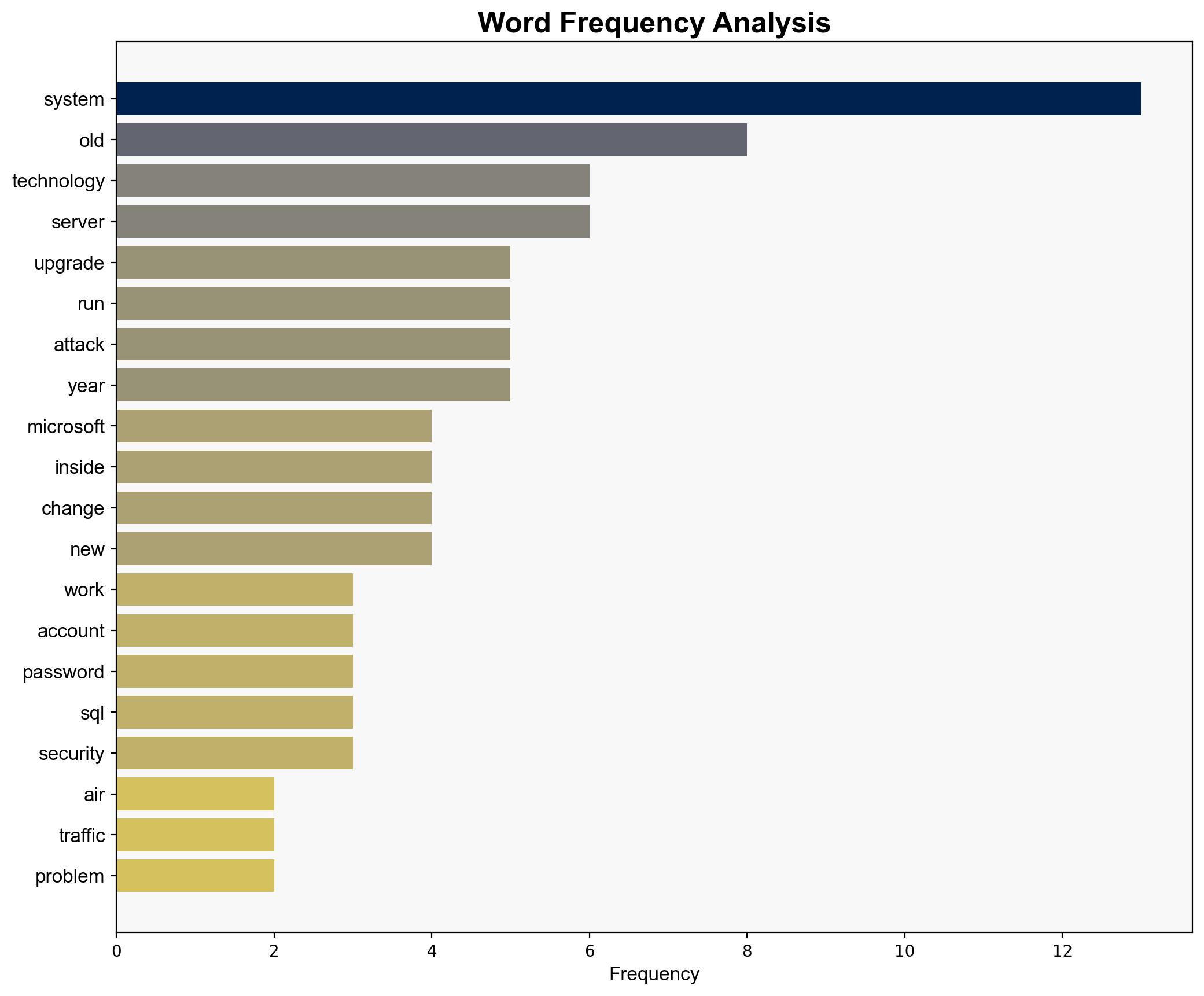
No specific individuals are mentioned in the source text. Entities involved include air traffic management systems, Microsoft, and potentially state actors involved in cyber threats.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus